KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft says they are investigating claims that the Lapsus$ data extortion hacking group breached their internal Azure DevOps source code repositories and stolen data.
Unlike many extortion groups we read about today, Lapsus$ does not deploy ransomware on their victim’s devices.
Instead, they target the source code repositories for large companies, steal their proprietary data, and then attempt to ransom that data back to the company for millions of dollars.
While it is not known if the extortion group has successfully ransomed stolen data, Lapsus has gained notoriety over the past months for their confirmed attacks against NVIDIA, Samsung, Vodafone, Ubisoft, and Mercado Libre.
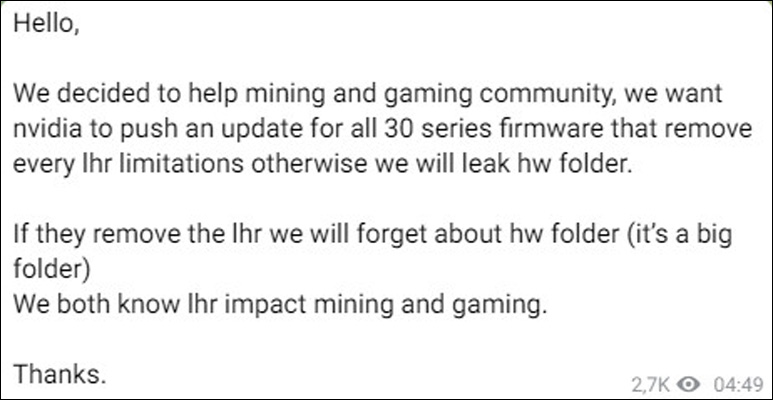
Early Sunday morning, the Lapsus$ gang indicated that they hacked Microsoft’s Azure DevOps server by posting a screenshot on Telegram of alleged internal source code repositories.
Also Read: What is a data protection officer? Through the lens of a Master DPO
This screenshot, shown below, is for an Azure DevOps repository containing the source code for Cortana and various Bing projects, named ‘Bing_STC-SV’, ‘Bing_Test_Agile’, and “Bing_UX.’
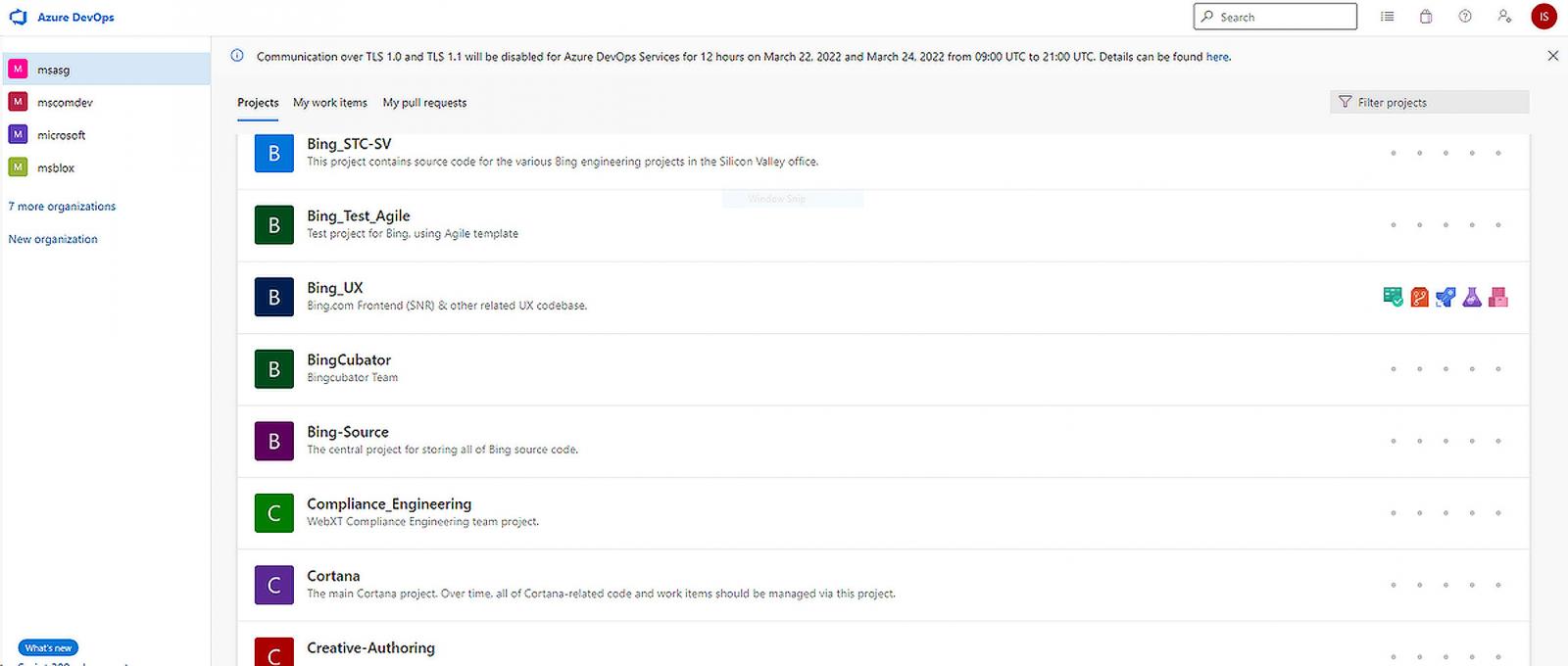
The screenshot also shows other source code repositories, but it is unknown what is contained within them.
Strangely, the extortion gang left the initials of the logged-in user, “IS,” in the screenshot, potentially allowing Microsoft to identify and secure the compromised account.
Including the initials may also mean that they no longer have access to the repository or are simply taunting Microsoft, which the extortion gang is known to do with previous victims.
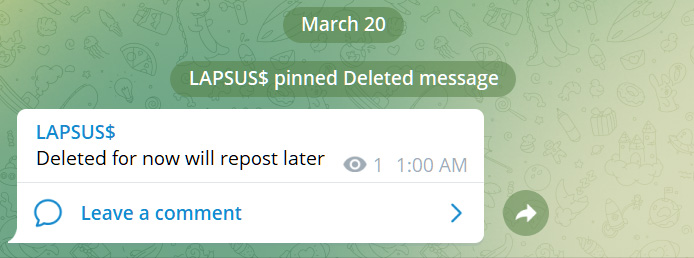
Soon after posting the screenshot, the Lapsus$ gang took their post down and replaced it with a message stating, “Deleted for now will repost later.” However, security researchers had already grabbed the screenshot and shared it on Twitter by that time.
While Microsoft has not confirmed if their Azure DevOps account was breached, they have told BleepingComputer that they are aware of the claims and are investigating them.
Unfortunately, Lapsus$ has a good track record, with their claims of attacks on other companies later confirmed to be true.
Also Read: How can businesses protect their enterprise from Business Email Compromise (BEC) attacks?
While the leaking of source code makes it easier to find vulnerabilities in a company’s software, Microsoft has previously stated that leaked source code does not create an elevation of risk.
Microsoft says that their threat model assumes that threat actors already understand how their software works, whether through reverse engineering or previous source code leaks.
“At Microsoft, we have an inner source approach – the use of open source software development best practices and an open source-like culture – to making source code viewable within Microsoft. This means we do not rely on the secrecy of source code for the security of products, and our threat models assume that attackers have knowledge of source code,” explained Microsoft in a blog post about the SolarWinds attackers gaining access to their source code.
“So viewing source code isn’t tied to elevation of risk.”
However, source code repositories also commonly contain access tokens, credentials, API keys, and even code signing certificates.
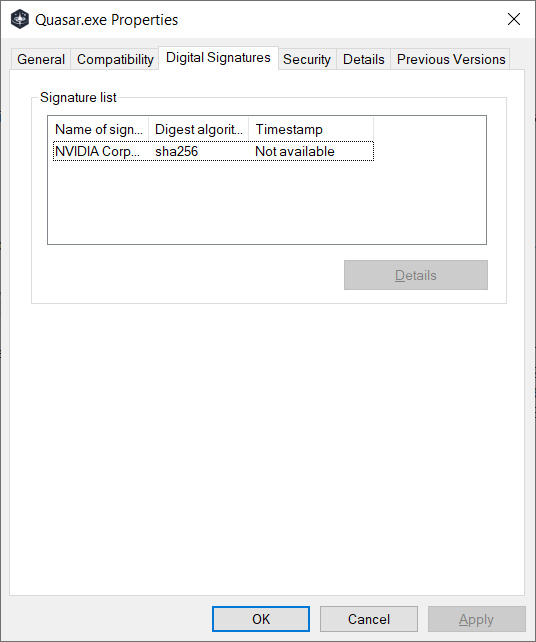
When Lapsus$ breached NVIDIA and released their data, it also included code-signing certificates that other threat actors quickly used to sign their malware. Using NVIDIA’s code signing certificate could cause antivirus engines to trust the executable and not detect it as malicious.
Microsoft has previously said that they have a development policy that prohibits “secrets,” such as API keys, credentials, or access tokens, from including their source code repositories.
Even if that is the case, it does not mean that there is no other valuable data included in the source code, such as private encryption key or other proprietary tools.
It is unknown what is contained within these repositories, but as was done with previous victims, it is only a matter of time before Lapsus$ leaks whatever stolen data they claim to have obtained.