KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft says attackers increasingly use malicious Internet Information Services (IIS) web server extensions to backdoor unpatched Exchange servers as they have lower detection rates compared to web shells.
Because they’re hidden deep inside the compromised servers and often very hard to detect being installed in the exact location and using the same structure as legitimate modules, they provide attackers’ with a perfect and durable persistence mechanism.
“In most cases, the actual backdoor logic is minimal and cannot be considered malicious without a broader understanding of how legitimate IIS extensions work, which also makes it difficult to determine the source of infection,” the Microsoft 365 Defender Research Team said Tuesday.
Threat actors rarely deploy such malicious extensions after compromising a server using exploits for various unpatched security flaws in a hosted app.
Also Read: The 11 obligations under PDPA and data protection
They’re usually deployed after a web shell is deployed as the first payload in the attack. The IIS module is deployed later to provide stealthier and persistent (update resistant) access to the hacked server.
Microsoft previously saw custom IIS backdoors installed after threat actors exploited ZOHO ManageEngine ADSelfService Plus and SolarWinds Orion vulnerabilities.
After deployment, malicious IIS modules allow threat actors to harvest credentials from system memory, collect information from the victims’ network and infected devices, and deliver more payloads.
More recently, in a campaign between January and May 2022 that targeted Microsoft Exchange servers, attackers deployed malicious IIS extensions to gain access to victims’ email mailboxes, run commands remotely, and steal credentials and confidential data.
“After a period of doing reconnaissance, dumping credentials, and establishing a remote access method, the attackers installed a custom IIS backdoor called FinanceSvcModel.dll in the folder C:\inetpub\wwwroot\bin\,” Microsoft added.
“The backdoor had built-in capability to perform Exchange management operations, such as enumerating installed mailbox accounts and exporting mailboxes for exfiltration.”
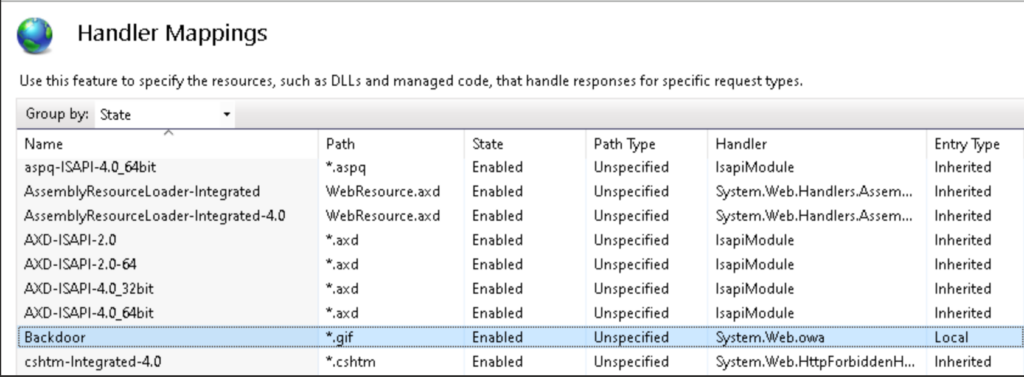
Kaspersky has also recently spotted malware delivered as IIS extensions onto Microsoft Exchange servers to execute commands and steal credentials remotely.
Also Read: Knowing the basics of cybersecurity
In December, a malicious IIS web server module named Owowa was used to target government organizations and public transportation companies across Southeast Asia and Europe.
Another IIS malware dubbed SessionManager was used in the wild without being detected since at least March 2021 (right after the start of last year’s massive wave of ProxyLogon attacks) in attacks against government and military orgs from Europe, the Middle East, Asia, and Africa.
“Once dropped into the victim’s system, cybercriminals behind the backdoor can gain access to company emails, update further malicious access by installing other types of malware or clandestinely manage compromised servers, which can be leveraged as malicious infrastructure,” Kaspersky said at the time.
“IIS modules are not a common format for backdoors, especially when compared to typical web application threats like web shells and can therefore easily be missed during standard file monitoring efforts.”
To defend against attacks using malicious IIS modules, Microsoft advises customers to keep their Exchange servers up to date, keep anti-malware and security solutions enabled, review sensitive roles and groups, restrict access to IIS virtual directories, prioritize alerts, and inspect config files and bin folders.