KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft said that over 40 of its customers had their networks infiltrated by hackers following the SolarWinds supply chain attack after they installed backdoored versions of the Orion IT monitoring platform.
Last weekend, FireEye discovered that a group of nation-state hackers (tracked as UNC2452 or Dark Halo) breached SolarWinds and used their auto-update mechanism to deploy a backdoor onto clients’ systems.
The backdoor, tracked as Solarigate (Microsoft) or Sunburst (FireEye), was deployed on the networks of roughly 18,000 customers according to a SolarWinds 8K SEC filing.
The APT group behind this campaign, suspected to be the Russian state-sponsored APT29 (aka Cozy Bear), maintained persistence on the networks of hacked organizations for long periods of time according to CISA.
After the malicious Orion upgrades were installed on the systems of thousands of SolarWinds customers, Microsoft President Brad Smith said that the suspected Russian hacking group were able to “pick and choose” targets of interest already compromised organizations.
Also Read: How To Prevent WhatsApp Hack: 7 Best Practices
So far, based on information gathered while investigating the still ongoing hacking campaign, Microsoft has notified the over 40 organizations that were “targeted more precisely and compromised through additional and sophisticated measures.”
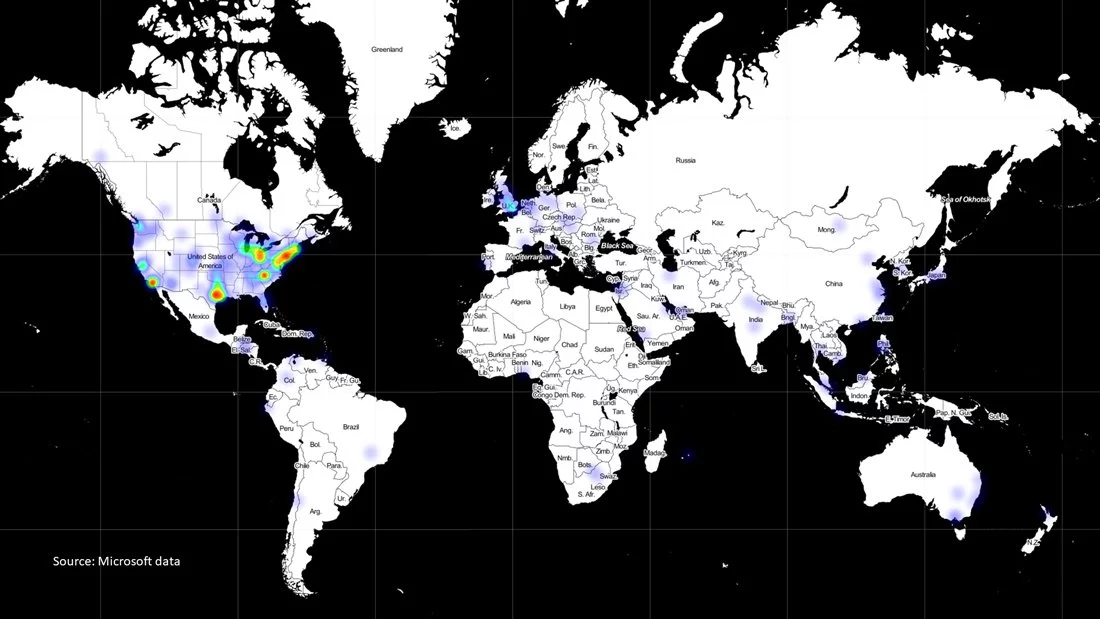
80% of the identified victims are located in the United States and the rest of 20% is spread over seven other countries including Canada, Mexico, Belgium, Spain, the United Kingdom, Israel, and the UAE.
A heat map of all Microsoft customers that were hit in the SolarWinds supply chain attack after installing the backdoor tracked as Solarigate or Sunburst via the compromised Orion auto-update mechanism.
“As this makes clear, this aspect of the attack created a supply chain vulnerability of nearly global importance, reaching many major national capitals outside Russia,” Smith said. “This also illustrates the heightened level of vulnerability in the United States.”
“This has already led to subsequent news reports of penetration into multiple parts of the U.S. Government. We should all be prepared for stories about additional victims in the public sector and other enterprises and organizations.”
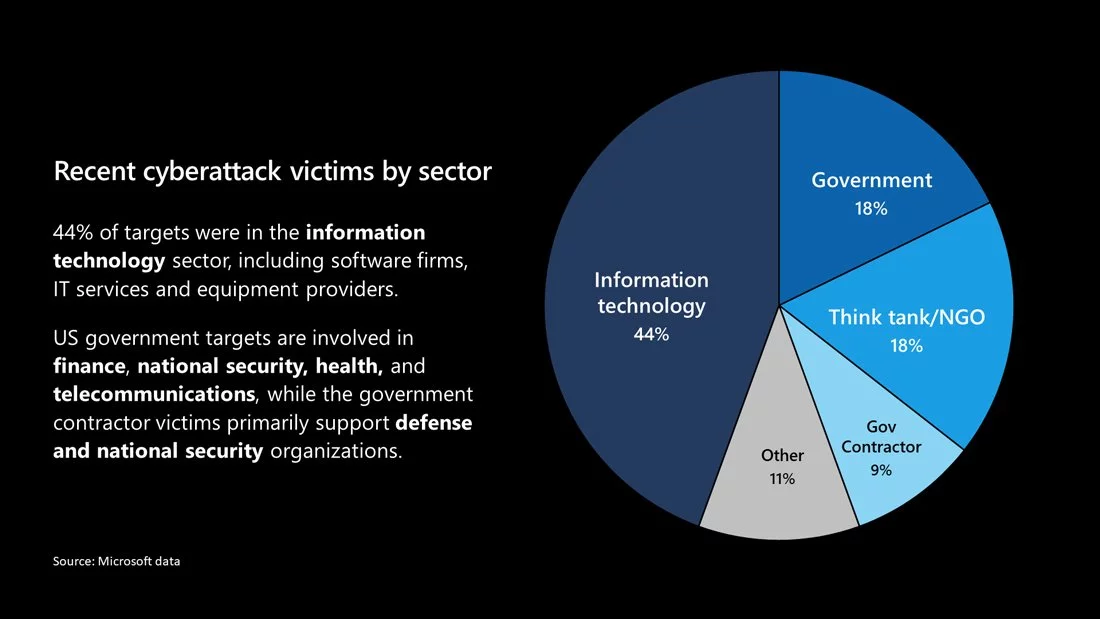
The initial list of Microsoft customers hacked in this ongoing espionage campaign includes organizations from a wide range of verticals, with 44% of them being information technology firms and 18% government agencies.
The US government targets breached following the SolarWinds hack coordinate finance, national security, health, and telecommunications sectors, while government contractor victims are focused on supporting defense and national security organizations.
What’s certain is that, following the ongoing investigation of these attacks, “the number and location of victims will keep growing.”
“This is not ‘espionage as usual,’ even in the digital age,” Smith said. “Instead, it represents an act of recklessness that created a serious technological vulnerability for the United States and the world.
“In effect, this is not just an attack on specific targets, but on the trust and reliability of the world’s critical infrastructure in order to advance one nation’s intelligence agency.
Also Read: 15 Best Tools For Your Windows 10 Privacy Settings Setup
“While the most recent attack appears to reflect a particular focus on the United States and many other democracies, it also provides a powerful reminder that people in virtually every country are at risk and need protection irrespective of the governments they live under.”
Microsoft has also confirmed yesterday that they were hacked in the ongoing SolarWinds attacks but denied reports that their software was compromised as part of a supply-chain attack to infect customers.
The FBI, CISA, and the ODNI also officially confirmed the hacking of multiple US government networks in a joint statement.
Victims of these attacks confirmed so far are FireEye, Microsoft, the US Treasury, US NTIA, US Department of Homeland Security, US Department of Commerce’s National Telecommunications and Information Administration (NTIA), US Department of State, US Department of Health’s National Institutes of Health (NIH), the Cybersecurity and Infrastructure Agency (CISA), the National Nuclear Security Administration (NNSA), and the US Department of Energy (DOE).
“CISA has determined that this threat poses a grave risk to the Federal Government and state, local, tribal, and territorial governments as well as critical infrastructure entities and other private sector organizations,” the agency said.
Also Read: How Formidable is Singapore Cybersecurity Masterplan 2020?
SolarWinds’ list of 300,000 customers [1, 2] includes over 425 US Fortune 500 companies, all top ten US telecom companies, and US government agencies including the US Military, the US Pentagon, the US Department of Justice, the State Department, NASA, NSA, Postal Service, NOAA, and the Office of the President of the United States, some of which have already been confirmed as hacked.