KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A Hive ransomware affiliate has been targeting Microsoft Exchange servers vulnerable to ProxyShell security issues to deploy various backdoors, including Cobalt Strike beacon.
From there, the threat actors perform network reconnaissance, steal admin account credentials, exfiltrate valuable data, ultimately deploying the file-encrypting payload.
The details come from security and analytics company Varonis, who was called in to investigate a ransomware attack on one of its customers.
ProxyShell is a set of three vulnerabilities in the Microsoft Exchange Server that allow remote code execution without authentication on vulnerable deployments. The flaws have been used by multiple threat actors, including ransomware like Conti, BlackByte, Babuk, Cuba, and LockFile, after exploits became available.
The flaws are tracked as CVE-2021-34473, CVE-2021-34523, and CVE-2021-31297, and their severity rating ranges from 7.2 (high) to 9.8 (critical).
The security vulnerabilities are considered fully patched as of May 2021, but extensive technical details about them were only made available in August 2021, and soon after that, malicious exploitation started [1, 2].
The fact that Hive’s affiliate was successful in exploiting ProxyShell in a recent attack shows that there is still room for targeting vulnerable servers.
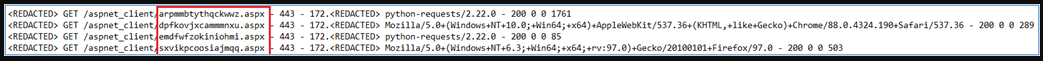
Following the exploitation of ProxyShell, the hackers planted four web shells in an accessible Exchange directory, and executed PowerShell code with high privileges to download Cobalt Strike stagers.
Also Read: Data Storage Security Standards: What Storage Professionals Need to Know
The web shells used in this particular attack were sourced from a public Git repository and were merely renamed to evade detection during potential manual inspections.
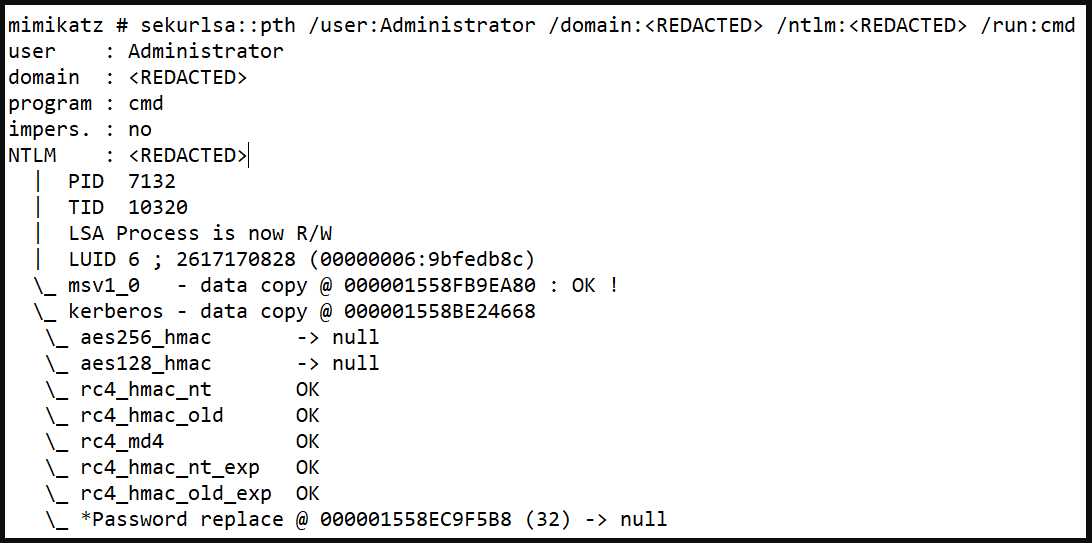
From there, the intruders used Mimikatz, a credentials stealer, to snatch the password of a domain admin account and perform lateral movement, accessing more assets in the network.
Next, the threat actors performed extensive file search operations to locate the most valuable data to pressure the victim into paying a larger ransom.
Varonis analysts have seen remnants of dropped network scanners, IP address lists, device and directory enumerations, RDPs to backup servers, scans for SQL databases, and more.
One notable case of network scanning software abuse was “SoftPerfect”, a lightweight tool that the threat actor used for enumerating live hosts by pinging them and saving the results on a text file.
Finally, and after all files had been exfiltrated, a ransomware payload named “Windows.exe” was dropped and executed on multiple devices.
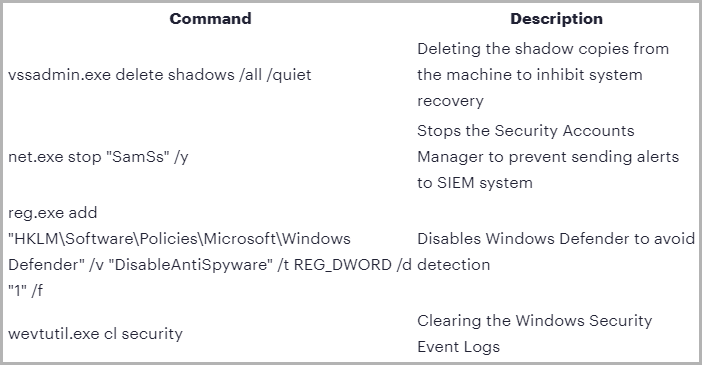
Before encrypting the organization’s files, the Golang payload deleted shadow copies, disabled Windows Defender, cleared Windows event logs, killed file-binding processes, and stopped the Security Accounts Manager to incapacitate alerts.
Also Read: IT Governance Framework PDF Best Practices And Guidelines
Hive has gone a long way since it was first observed in the wild back in June 2021, having a successful start that prompted the FBI to release a dedicated report on its tactics and indicators of compromise.
In October 2021, the Hive gang added Linux and FreeBSD variants, and in December it became one of the most active ransomware operations in attack frequency.
Last month, researchers at Sentinel Labs reported on a new payload-hiding obfuscation method employed by Hive, which indicates active development.