KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft Defender for Endpoint is currently detecting at least two Chrome updates as malware, tagging the Slovenian localization file bundled with the Google Chrome installer as a malicious file.
System admins are reporting that Microsoft’s enterprise endpoint security platform (previously known as Microsoft Defender ATP) is detecting the sl.pak component in both Chrome 88.0.4324.104 and 88.0.4324.146 (the latest version, released yesterday) installers as a PHP/Funvalget.A backdoor.
Even though multiple Microsoft security accounts were tagged on Twitter and the company was also contacted to provide a statement regarding this ongoing issue, Redmond hasn’t yet provided an official reply.
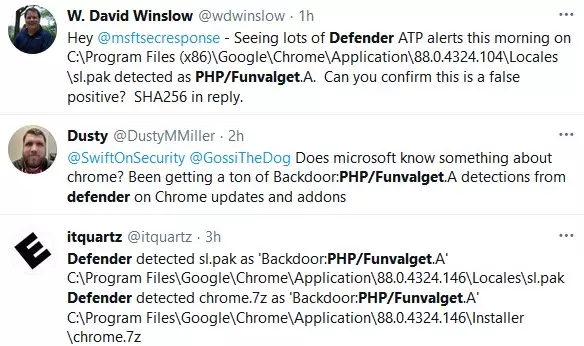
BleepingComputer has also contacted Microsoft for more information and to confirm that this is an issue of a false positive detection but has not heard back.
Also Read: How Formidable is Singapore Cybersecurity Masterplan 2020?
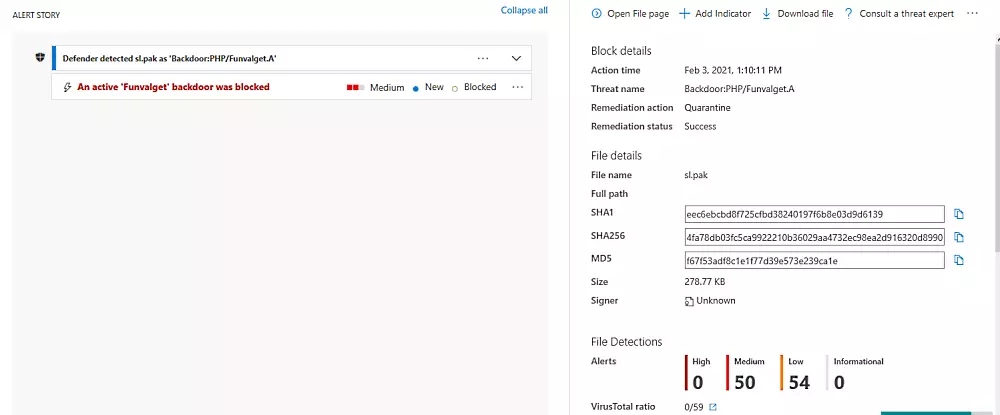
As first reported by ZDNet, according to a screenshot showing the Chrome sl.pak language file being tagged as a backdoor, Microsoft Defender for Endpoint automatically blocks the detected files using quarantine as a remediation action.
Microsoft has stated that the issue was an automation error and is now resolved.
“We’ve corrected an automation error that incorrectly classified the installation package as malware.” – a Microsoft spokesperson.
To clear the cached detection on endpoints in their environment, systems admins are advised to update to the latest malware definitions by using this procedure:
cd %ProgramFiles%\Windows DefenderMpCmdRun.exe -removedefinitions -dynamicsignatures and MpCmdRun.exe -SignatureUpdateAlso Read: Going Beyond DPO Meaning: Ever Heard of Outsourced DPO?