KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft detected a large-scale business email compromise (BEC) campaign that targeted more than 120 organizations using typo-squatted domains registered a few days before the attacks started.
BEC scammers use various tactics (including social engineering, phishing, or hacking) to compromise business email accounts, later used to redirect payments to bank accounts under their control or target employees in gift card scams.
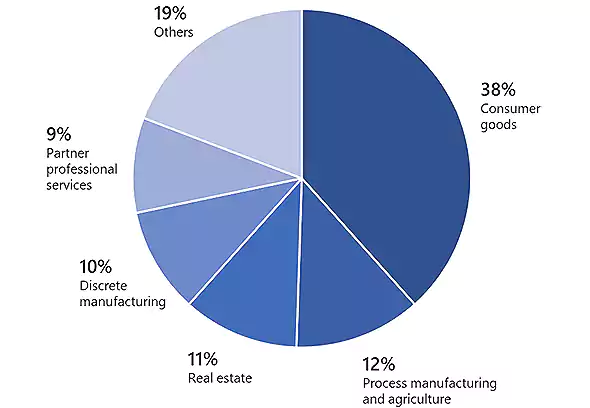
Microsoft used the typo-squatted domains to send emails impersonating managers of employees working at companies from various industry sectors, including real estate, discrete manufacturing, and professional services.
“We observed patterns in using the correct domain name but an incorrect TLD, or slightly spelling the company name wrong. These domains were registered just days before this email campaign began,” the Microsoft 365 Defender Threat Intelligence Team said.
However, despite the scammers’ efforts to match the spoofed domains to the right target, Microsoft “the registered domains did not always align with the organization being impersonated in the email.”
Although their approach was flawed at times, the attackers’ reconnaissance skills are apparent since they addressed the targeted employees’ using their first names.
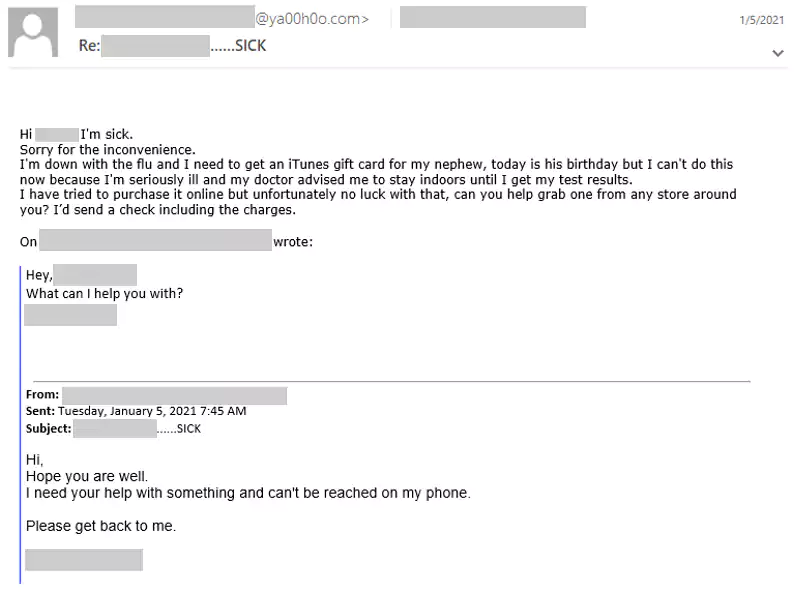
Microsoft also saw the scammers using standard phishing techniques like fake replies (improved by also spoofing In-Reply-To and References headers) to add legitimacy to the phishing emails.
“Filling these headers in made the email appear legitimate and that the attacker was simply replying to the existing email thread between the Yahoo and Outlook user,” Microsoft added.
Also Read: The DNC Registry Singapore: 5 Things You Must Know
“This characteristic sets this campaign apart from most BEC campaigns, where attackers simply include a real or specially crafted fake email, adding the sender, recipient, and subject, in the new email body, making appear as though the new email was a reply to the previous email.”
Although these BEC scammers’ methods might seem lacking sophistication and their phishing messages look obviously malicious in nature to some, BEC attacks are behind record-breaking financial losses each year since 2018.
In 2018, the Federal Bureau of Investigation (FBI) established a Recovery Asset Team focused on recovering money that can still be tracked and on freezing accounts used by fraudsters for unauthorized BEC transfers.
The FBI warned the US private sector companies in March about BEC attacks increasingly targeting state, local, tribal, and territorial (SLTT) government entities.
“The FBI’s Internet Crime Complaint Center (IC3) notes BEC is an increasing and constantly evolving threat as criminal actors become more sophisticated and adapt to current events,” the FBI said.
“There was a 5 percent increase in adjusted losses from 2019 to 2020, with over $1.7 billion adjusted losses reported to IC3 in 2019 and over $1.8 billion adjusted losses reported in 2020.”
Also Read: How To Comply With PDPA: A Checklist For Businesses
Furthermore, FBI’s 2020 annual report on cybercrime affecting US victims published earlier this week listed a record number of complaints and financial losses in 2020.