KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Threat actors are abusing the Microsoft Build Engine (MSBuild) to deploy remote access tools (RATs) and information-stealing malware filelessly as part of an ongoing campaign.
MSBuild (msbuild.exe) is a legitimate and open-source Microsoft development platform, similar to the Unix make utility, for building applications.
This development tool can build apps on any Windows system if provided with an XML schema project file telling it how to automate the build process (compilation, packaging, testing, and deployment.)
As Anomali’s Threat Research team observed, the malicious MSBuild project files delivered in this campaign bundled encoded executables and shellcode the threat actors used for injecting the final payloads into the memory of newly spawned processes.
“While we were unable to determine the distribution method of the .proj files, the objective of these files was to execute either Remcos or RedLine Stealer,” Anomali intelligence analysts Tara Gould and Gage Mele said.
Also Read: PDPA Compliance Singapore: 10 Areas To Work On
The attackers started pushing Remcos RAT, Quasar RAT, and RedLine Stealer payloads onto their victims’ computers last month in attacks that were still active Tuesday, two days before Anomali unveiled their research.
Once the RATs are installed on a targeted system, they can be used to harvest keystrokes, credentials, and screen snapshots, disable anti-malware software, gain persistence, and fully take over the devices remotely.
On computers where the attackers deployed the info stealer, the malware will scan for web browsers, messaging apps, and VPN and cryptocurrency software to steal user credentials.
RedLine can also collect and exfiltrate system information, cookies, and crypto wallet information from configuration files and app data stored on the victims’ devices.
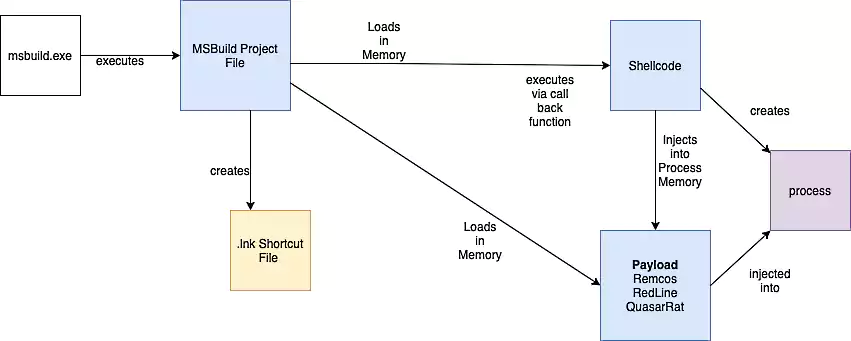
Using Microsoft’s legitimate MSBuild development tool enables the attackers to successfully evade detection while loading their malicious payloads directly into a targeted computer’s memory.
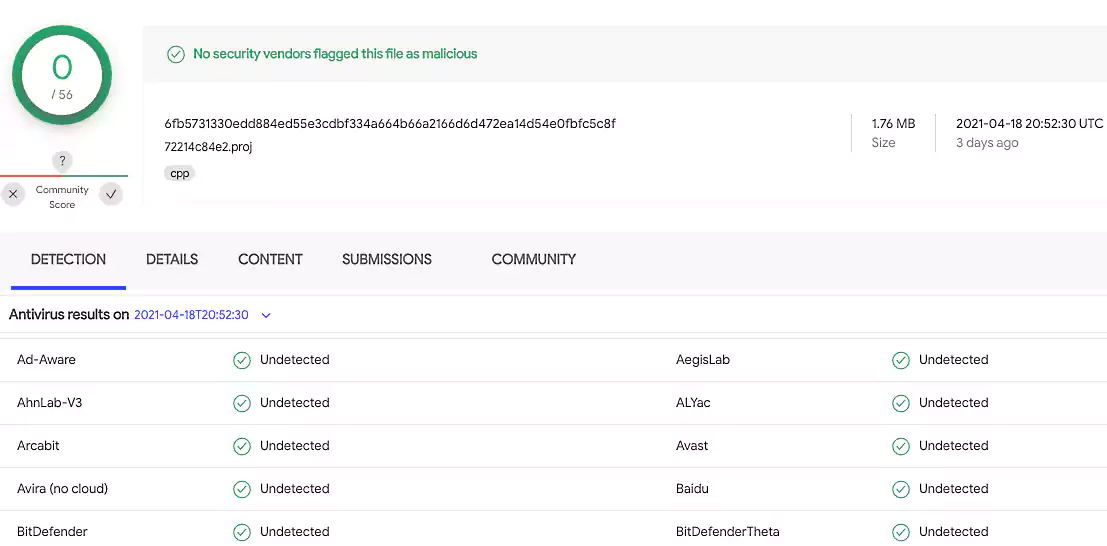
Malware samples used in this campaign are either not detected or detected by a very low number of anti-malware engines according to VirusTotal.
The fileless malware further decreases the chances that the attack is spotted since no actual files are written on the victims’ devices, with no physical traces of the payloads left on the infected devices’ hard drives.
According to a WatchGuard Internet security report published at the end of March, fileless malware delivery has seen a massive increase between 2019 and 2020, skyrocketing by 888% based on a year worth of endpoint threat intelligence data collected by WatchGuard Panda products.
Also Read: What Does A Data Protection Officer Do? 5 Main Things
“The threat actors behind this campaign used fileless delivery as a way to bypass security measures, and this technique is used by actors for a variety of objectives and motivations,” Anomali concluded.
“This campaign highlights that reliance on antivirus software alone is insufficient for cyber defense, and the use of legitimate code to hide malware from antivirus technology is effective and growing exponentially.”