KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





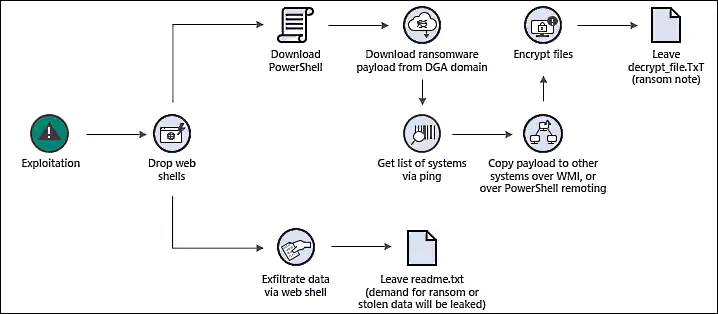
Microsoft has discovered web shells deployed by Black Kingdom operators on approximately 1,500 Exchange servers vulnerable to ProxyLogon attacks.
“They started later than some other attackers, with many compromises occurring between March 18 and March 20, a window when fewer unpatched systems were available,” the Microsoft 365 Defender Threat Intelligence Team said.
“These web shells were observed on around 1,500 systems, not all of which moved to the ransomware stage.
“Many of the compromised systems have not yet received a secondary action, such as human-operated ransomware attacks or data exfiltration, indicating attackers could be establishing and keeping their access for potential later actions.”
Malware analyst Marcus Hutchins was the first to spot Black Kingdom (also tracked as Pydomer by Microsoft) targeting Exchange servers over the weekend after one of his ProxyLogon honeypots picked up the malicious activity.
More than 30 Black Kingdom submissions coming directly from impacted mail servers have been added to ransomware identification site ID Ransomware starting on March 18.
While the ransomware gang failed to encrypt any files on Hutchins’ honeypots, the ID Ransomware submissions are all from successfully encrypted Exchange servers.
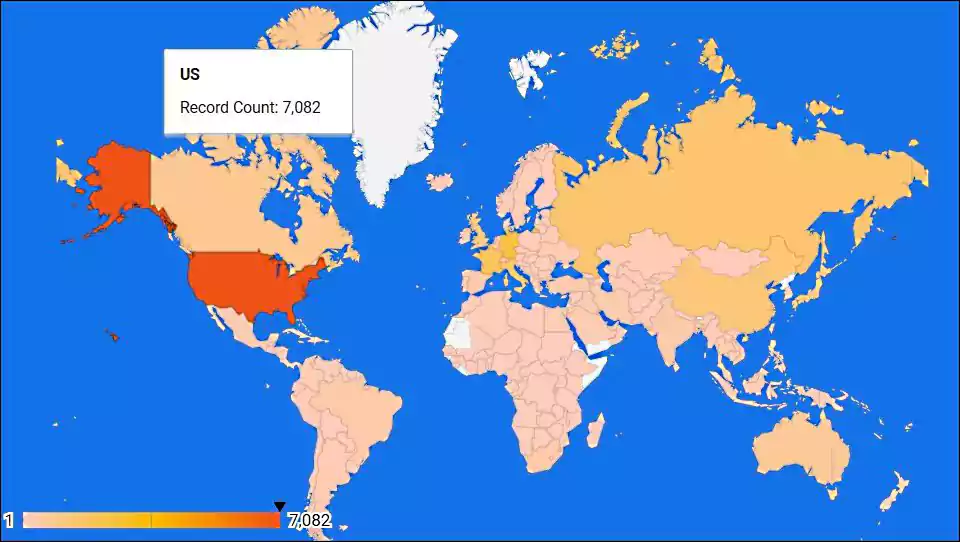
Black Kingdom ransomware victims are located in the US, Russia, Canada, Germany, Austria, Switzerland, France, Israel, United Kingdom, Italy, Greece, Australia, and Croatia.
When BleepingComputer analyzed the Black Kingdom ransomware, it created a ransom note demanding $10,000 in bitcoins for a decryption key.
Also Read: Practitioner Certificate In Personal Data Protection: Everything You Need To Know
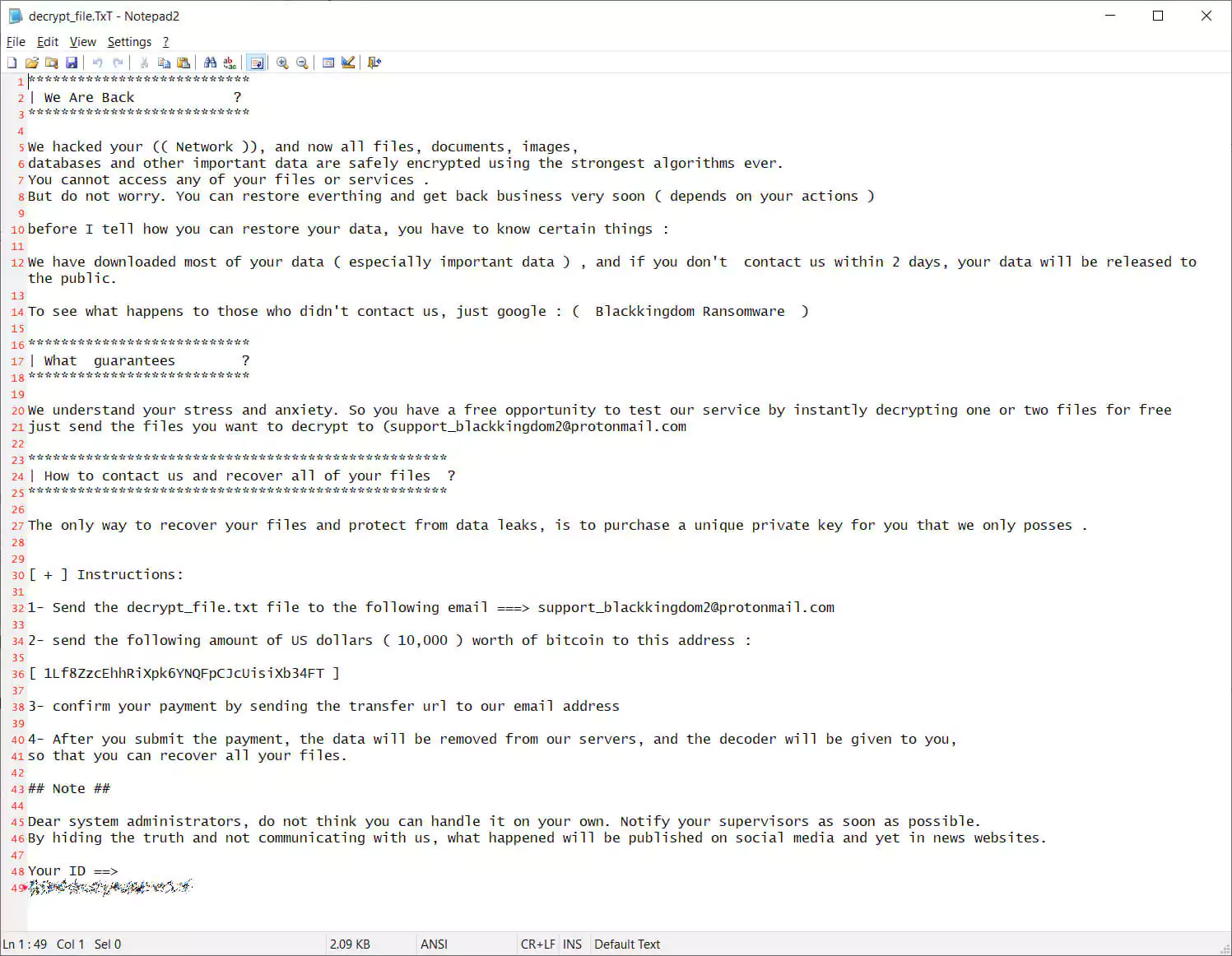
The ransom note also warned victims that data was stolen before their devices were encrypted and would be publicly released if a ransom is not paid.
In some of the attacks, Microsoft noted that a ransom note was created even though the device was not encrypted. It is unknown if this was a failed encryption attempt or they were simply exfiltrating data and ransoming it off.
“The note should be taken seriously if encountered, as the attackers had full access to systems and were likely able to exfiltrate data,” Microsoft added.
While a connection has not yet been made, another ransomware dubbed Black Kingdom targeted corporate networks with Pulse Secure VPN exploits in June 2020.
Hutchins said that the current ransomware executable is a Python script compiled as a Windows executable. BleepingComputer has confirmed that last year’s Black Kingdom ransomware was also a Python-based malware.
Black Kingdom is the second confirmed ransomware that targets unpatched Microsoft Exchange servers with ProxyLogon exploits.
The first one was DearCry ransomware, a new strain deployed in attacks that started about one week after Microsoft released ProxyLogon security updates.
Threat actors behind ProxyLogon attacks have also been observed while stealing credentials via LSASS dumps and deploying cryptomining malware.
Microsoft revealed on Monday that roughly 92% of all on-premises Exchange servers reachable over the Internet and affected by the ProxyLogon vulnerabilities are now patched and safe from ongoing attacks.
From a total of 400,000 Internet-connected Exchange servers impacted by the ProxyLogon flaws when Microsoft issued the initial security patches on March 2, there are now under 30,000 still exposed to attacks, according to RiskIQ telemetry.
Also Read: The DNC Singapore: Looking At 2 Sides Better