KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft has announced a new security product allowing security teams to spot Internet-exposed resources in their organization’s environment that attackers could use to breach their networks.
The focus is on unmanaged or unknown assets added to the environment after mergers or acquisitions, created by shadow IT, missing from inventory due to incomplete cataloging, or left out due to rapid business growth.
Dubbed Microsoft Defender External Attack Surface Management, this new product provides customers with an overview of their businesses’ attack surface, making it simpler to discover vulnerabilities and block potential attack vectors.
By continuously scanning Internet connections, this tool will create a catalog of the organization’s entire environment, including unmanaged and agentless devices.
Also Read: A Review of PDPC Undertakings July 2021 Cases
“The new Defender External Attack Surface Management gives security teams the ability to discover unknown and unmanaged resources that are visible and accessible from the internet – essentially, the same view an attacker has when selecting a target,” Microsoft Corporate VP for Security Vasu Jakkal said.
“Defender External Attack Surface Management helps customers discover unmanaged resources that could be potential entry points for an attacker.”
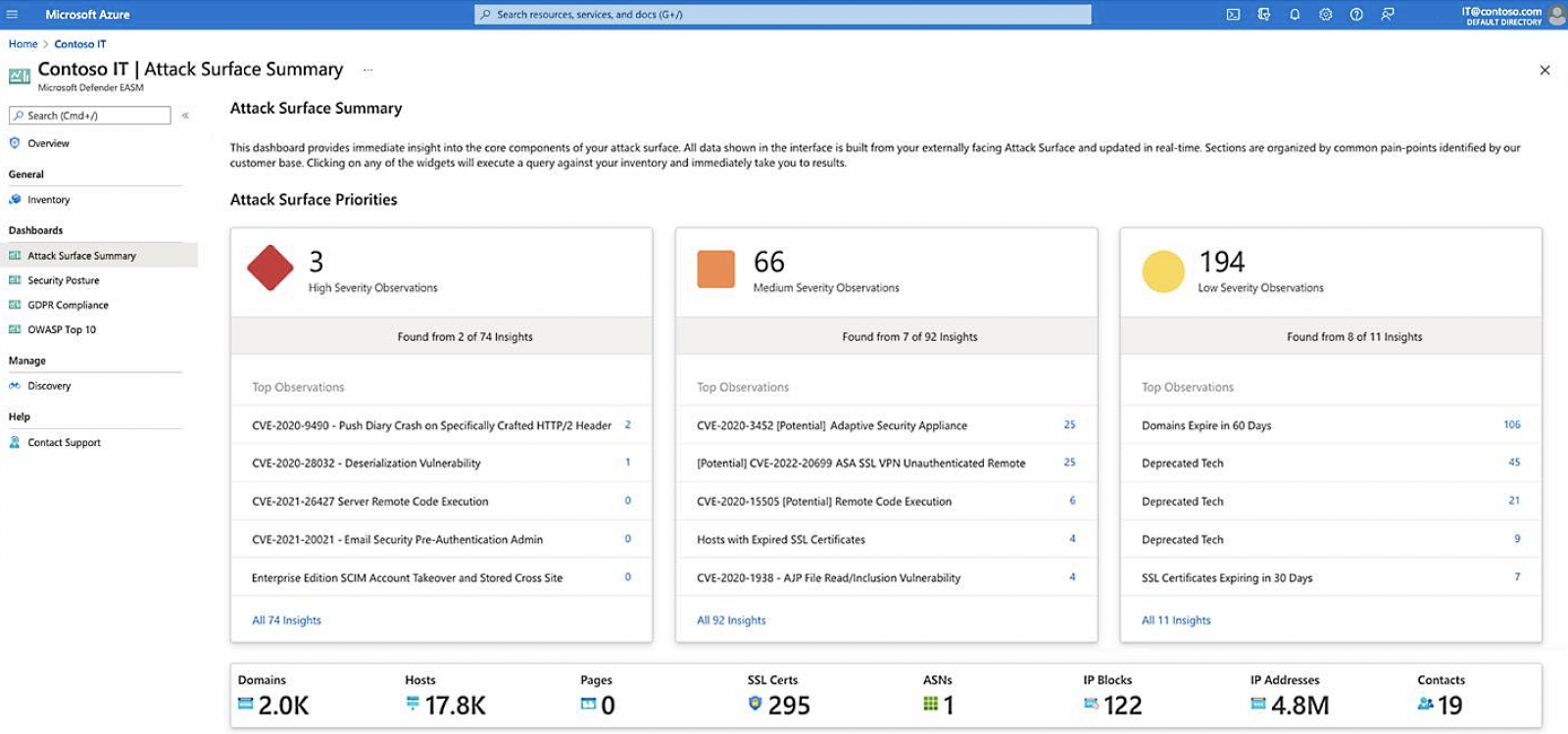
By continuously tracking connections and looking for unprotected devices exposed to Internet attacks, Microsoft Defender External Attack Surface Management enables security teams to see their environment the way an attacker does and discover exploitable vulnerabilities before they do.
“Continuous monitoring, without the need for agents or credentials, prioritizes new vulnerabilities,” Jakkal explained.
“With a complete view of the organization, customers can take recommended steps to mitigate risk by bringing these unknown resources, endpoints, and assets under secure management within their SIEM and XDR tools.”
Microsoft also announced today Microsoft Defender Threat Intelligence, a second security product that will supply security operations (SecOps) teams with the threat intelligence needed to discover attacker infrastructure and speed up attack investigations and remediation efforts.
Also Read: Protecting Data Online in the New Normal
It will also give SecOps team members access to real-time data from Microsoft’s massive set of 43 trillion daily security signals to hunt for threats in their environments proactively.
The data is provided as a library of raw threat intelligence with info on adversariess’ names and correlating their tools, tactics, and procedures (TTPs).
According to Microsoft, all this extra information into threat actors’ TTPs and their infrastructure will help customers’ security teams detect, remove, and block hidden adversary tools within their org’s environment.
“This depth of threat intelligence is created from the security research teams formerly at RiskIQ with Microsoft’s nation-state tracking team, Microsoft Threat Intelligence Center (MSTIC) and the Microsoft 365 Defender security research teams,” Jakkal added.
“The volume, scale and depth of intelligence is designed to empower Security Operations Centers to understand the specific threats their organization faces and to harden their security posture accordingly.”