KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft announced that consent phishing protections including OAuth app publisher verification and app consent policies are now generally available in Office 365.
These protections are designed to defend Office 365 users from an application-based phishing attack variant known as consent phishing.
In this type of phishing attack, targets are tricked into providing access to their Office 365 accounts by granting permissions to malicious Office 365 OAuth apps (web apps attackers register with an OAuth 2.0 provider).
Microsoft says that it’s rolling out three updates designed to bolster the security of the Office 365 app ecosystem including:
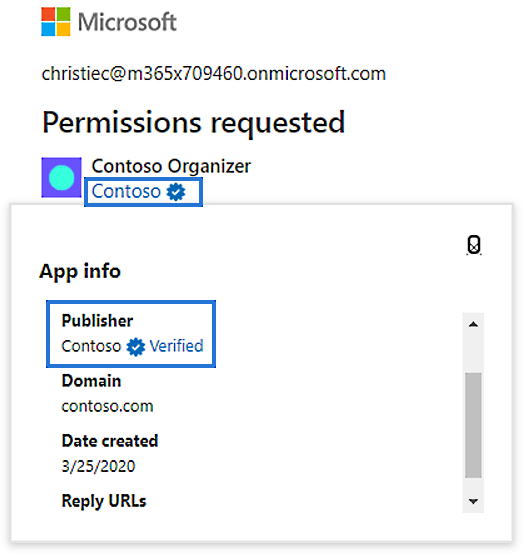
Publisher verification enables developers to “add a verified identity to their app registrations and demonstrate to customers that the app comes from an authentic source.”
Since this feature entered public preview in May, more than 700 app publishers have been verified by Microsoft amounting to a total of over 1300 app registrations.
Apps developed by verified publishers feature a blue “verified” badge on all Azure AD consent prompts, as well as other screens where they’re featured to make it easier for end-users to verify application authenticity.
Also Read: The Importance Of Knowing Personal Data Protection Regulations
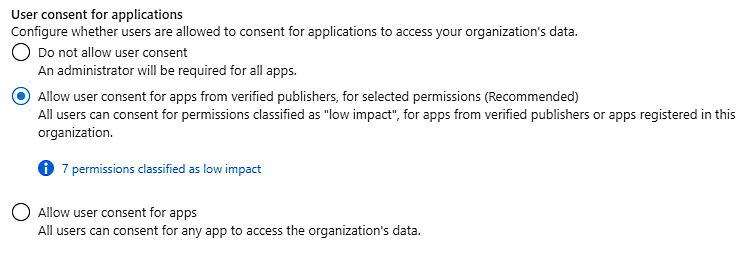
The new generally available app consent policies for end-user consent provide administrators with “more controls over the apps and permissions to which users can consent.”
“To reduce the risk of malicious applications attempting to trick users into granting them access to your organization’s data, we recommend that you allow user consent only for applications that have been published by a verified publisher,” Microsoft explains.
Once app consent policies are configured, users will only be able to grant permissions to apps developed by verified publishers thus blocking future consent phishing attacks.
Using Azure AD PowerShell, admins can also set up custom app consent policies when they need more granular control.
To configure user consent settings through the Azure portal, admins need to go through the following steps:
All Office 365 users will be protected from app-based attacks now that publisher verification is generally available as they “will no longer be able to consent to new multi-tenant apps registered after November 8th, 2020 coming from unverified publishers.”
Also Read: Is it Illegal to Email Someone Without Their Permission?
Such apps will be automatically flagged as risky and tagged as unverified on all consent screens, except for apps that request consent within their tenants and of those only asking for basic sign-in and permissions to read user profiles.
Microsoft warned customers in July of threat actors using Office 365 OAuth applications in consent phishing attacks as part of Business Email Compromise (BEC) fraud schemes.
The attackers’ end goal in such cases is to take over their victims’ Microsoft accounts and to make API calls on their behalf through attacker-controlled apps.
After compromising a victim’s Office 365 account, the attackers obtain access to their mail, files, contacts, notes, and profiles, as well as a wide range of other sensitive info and resources stored on their corporate OneDrive for Business cloud storage space and the SharePoint document management/storage system.
“While application use has accelerated and enabled employees to be productive remotely, attackers are looking at leveraging application-based attacks to gain unwarranted access to valuable data in cloud services,” Microsoft Partner Group PM Manager Agnieszka Girling said at the time.
BleepingComputer reported on the inner-workings of a consent phishing attack during December 2019, showing it allowed the attackers to hijack their victims’ Office 365 accounts.
 Phishing email sample Phishing email sample | 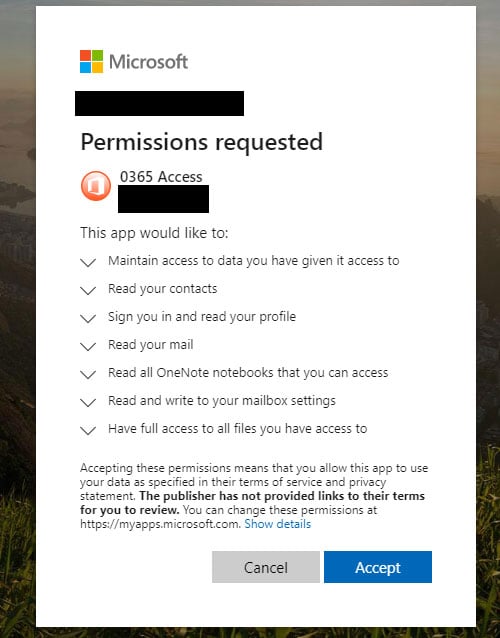 Malicious Office 365 OAuth app Malicious Office 365 OAuth app |
“Once victims clicked on the deceptive links, they were ultimately prompted to grant access permissions to a malicious web application (web app),” Microsoft Corporate Vice President for Customer Security & Trust Tom Burt explained.
“Unknown to the victim, these malicious web apps were controlled by the criminals, who, with fraudulently obtained permission, could access the victim’s Microsoft Office 365 account.”
Microsoft took legal action against the threat actors behind these attacks, announcing the takedown of six domains (officeinvetorys[.]com, officehnoc[.]com, officesuited[.]com, officemtr[.]com, officesuitesoft[.]com, and mailitdaemon[.]com) that were used to host malicious Office 365 OAuth apps.
For more tips on how to defend against consent security threats, organizations can also review the Detect and Remediate Illicit Consent Grants in Office 365 support document.