KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft has added support for security incident email notifications to the Microsoft 365 Defender enterprise threat protection solution.
The Microsoft 365 Defender suite is used by security teams for coordinated threat protection in enterprise environments for protecting devices, identity, data, and applications.
As Microsoft shared earlier today, Microsoft 365 admins can now set up Microsoft 365 Defender to alert them via email on new security incidents or updates to existing incidents.
“The email notification contains important details about the incident like the incident name, severity, and categories, among others,” Microsoft explains. “You can also directly go to incidents so you can start your investigation right away.”
After enabling the email alerts, admins will be able to track all new incidents and any subsequent updates without having to use API integrations or trouble ticketing systems.
From the email notifications, they can open the incident and begin investigating it straightaway.
Also Read: Limiting Location Data Exposure: 8 Best Practices
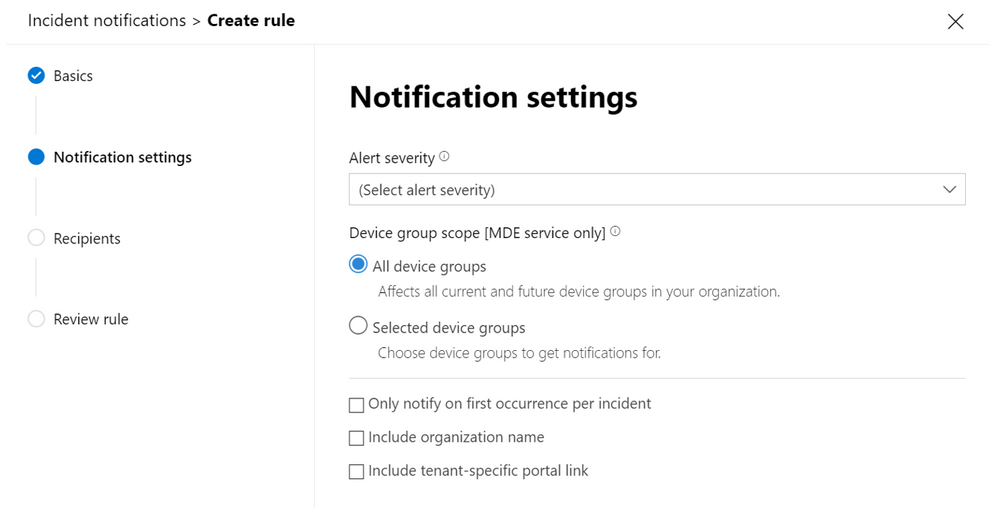
Depending on the way they are configured, email notifications can be received based on incident severity or by device group.
They can also be set up to be delivered only on the first incident update and you can also add or remove recipients for the email notifications (new recipients will get incident alerts after they’re added).
To be able to configure email notification settings admins need to have ‘Manage security settings’ permissions. Those with basic permissions will have to ask users with Security Administrator or Global Administrator roles to configure them.
“Likewise, if your organization is using role-based access control (RBAC), you can only create, edit, delete, and receive notifications based on device groups that you are allowed to manage,” Microsoft says.
Also Read: 10 Practical Benefits of Managed IT Services
“It can be a big help in transitioning your security operations processes and leveraging the great efficiency improvements provided through the incident’s alert correlation capabilities,” Microsoft added.