KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







This month a researcher has disclosed how he broke into the official GitHub repository of Microsoft Visual Studio Code.
A vulnerability in VS Code’s issue management function and a lack of authentication checks enabled the researcher to obtain push access, and write to the repository.
For responsibly reporting the vulnerability, the researcher was awarded a bug bounty award of an undisclosed amount.
While riding a train, researcher RyotaK discovered a vulnerability in the VS Code’s Continuous Integration (CI) script that let him break into Microsoft VS Code’s official GitHub repository and commit files.
“I was too bored while I was on the train, so I decided to read the VS Code code. After a while, I noticed that VS Code has a separate repository for CI scripts named vscode-github-triage-actions. So I decided to read it,” RyotaK told BleepingComputer.
Shortly, the researcher noticed an interesting line in the script that could be exploited in code injection attacks:
exec(`git -C ./repo merge-base –is-ancestor ${commit} ${release}`, (err) => {
Also Read: 10 Principles On How To Build A Good Governance Model
“Of course, there is command injection. But it requires control of the ‘commit’ variable or the ‘release’ variable,” continued RyotaK in an email interview.
The researcher soon realized the commit variable could be controlled by an attacker due to two reasons:
The closedWith command is used to associate a commit hash with the issue before the commit is closed.
However, a flawed regex expression (shown below) used to validate the closing comments and no authentication checks in the CI script meant, any user could associate a commit with an issue, and inject code within the closedWith value.const closingHashComment = /(?:\\|\/)closedWith (\S*)/
Because VS Code’s vulnerable CI workflow ran once a day, around midnight, the researcher carefully planned a Proof-of-Concept (PoC) exploit in advance, so as to not make any dangerous mistakes during night hours.
To do so, the researcher browsed through the GitHub Actions code files for the project to get an understanding of the Continuous Integration and Continuous Delivery (CI/CD) workflow.
“Fortunately, the workflow files for GitHub Actions are published on GitHub, so I have some idea of what’s going on inside GitHub Actions.”
“Since actions/checkout was executed in the step before the vulnerable workflow file is used, there was a GitHub token with write permission to the repository. So I made a plan to use this token,” the researcher told BleepingComputer.
By injecting his basic PoC exploit into the VS Code’s CI script which ran around midnight, the researcher obtained a reverse shell.
Further, the researcher obtained the GitHub authorization token for VS Code repository that would give him write access to the repository.
Eventually, after obtaining the token, the researcher posted a PoC commit to the repository:
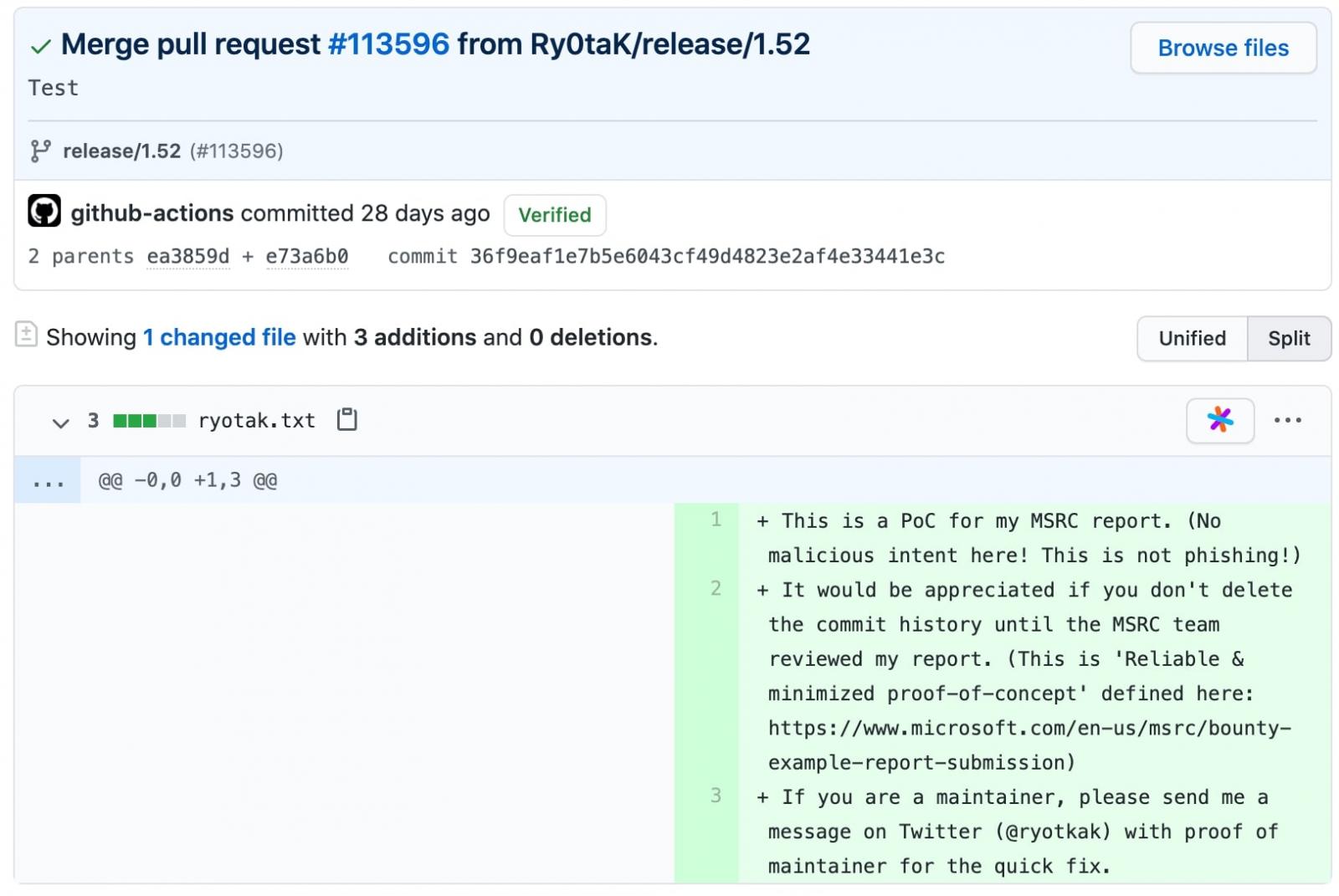
Although, the master branch of the repository had account-based branch protections that could not be bypassed with the GitHub Actions token, it was possible to push the file to the release branch using the token, states the researcher.
It is worth noting RyotaK performed this PoC exploit while adhering to Microsoft’s “safe harbor” guidelines when reporting vulnerabilities through their bug bounty programs.
“Microsoft permits the diagnosis of vulnerabilities through safe harbors. This article describes the vulnerabilities discovered / reported in compliance with the safe harbor, and is not intended to recommend unauthorized vulnerability diagnosis,” stated RyotaK in his blog post.
Also Read: The Importance Of DPIA And Its 3 Types Of Processing
For his discovery of the vulnerability and following responsible disclosure guidelines, the researcher told BleepingComputer, that he was awarded a cash bounty prize of an undisclosed amount by Microsoft.
Flaws of this extent that enable adversaries to break into otherwise secure software codebases can lay the groundwork for sophisticated software supply chain attacks.
This astounding discovery comes to light when the SolarWinds supply chain attack incident has already been making headlines.
In this case, the ethical hacker RyotaK discovered and responsibly reported the flaw to Microsoft before advanced threat actors could exploit it, to push their malicious code upstream into the Visual Studio Code repository.
Corruption of source-code editors and IDEs in a targeted supply chain attack can have devastating consequences for its users, developers, and the clients that would then be receiving the applications built using a tainted IDE.
Recently, another group of security researchers reported finding exposed Git credentials due to improperly secured .git directories on UN domains.
This discovery enabled them to clone the entire Git repository of the United Nations Environment Programme (UNEP) and eventually access over 100,000 employee records.
Securing your CI/CD tools, and proactively auditing their scripts for security flaws before adversaries exploit any vulnerabilities are a few defenses towards preventing software supply-chain compromises.