KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Security researchers warn that some attackers are compromising Microsoft Teams accounts to slip into chats and spread malicious executables to participants in the conversation.
More than 270 million users are relying on Microsoft Teams every month, many of them trusting the platform implicitly, despite the absence of protections against malicious files.
Researchers at Avanan, a Check Point company that secures cloud email and collaboration platforms, found that hackers started to drop malicious executable files in conversations on Microsoft Teams communication platform.
Also Read: EU GDPR Articles: Key For Business Security And Success
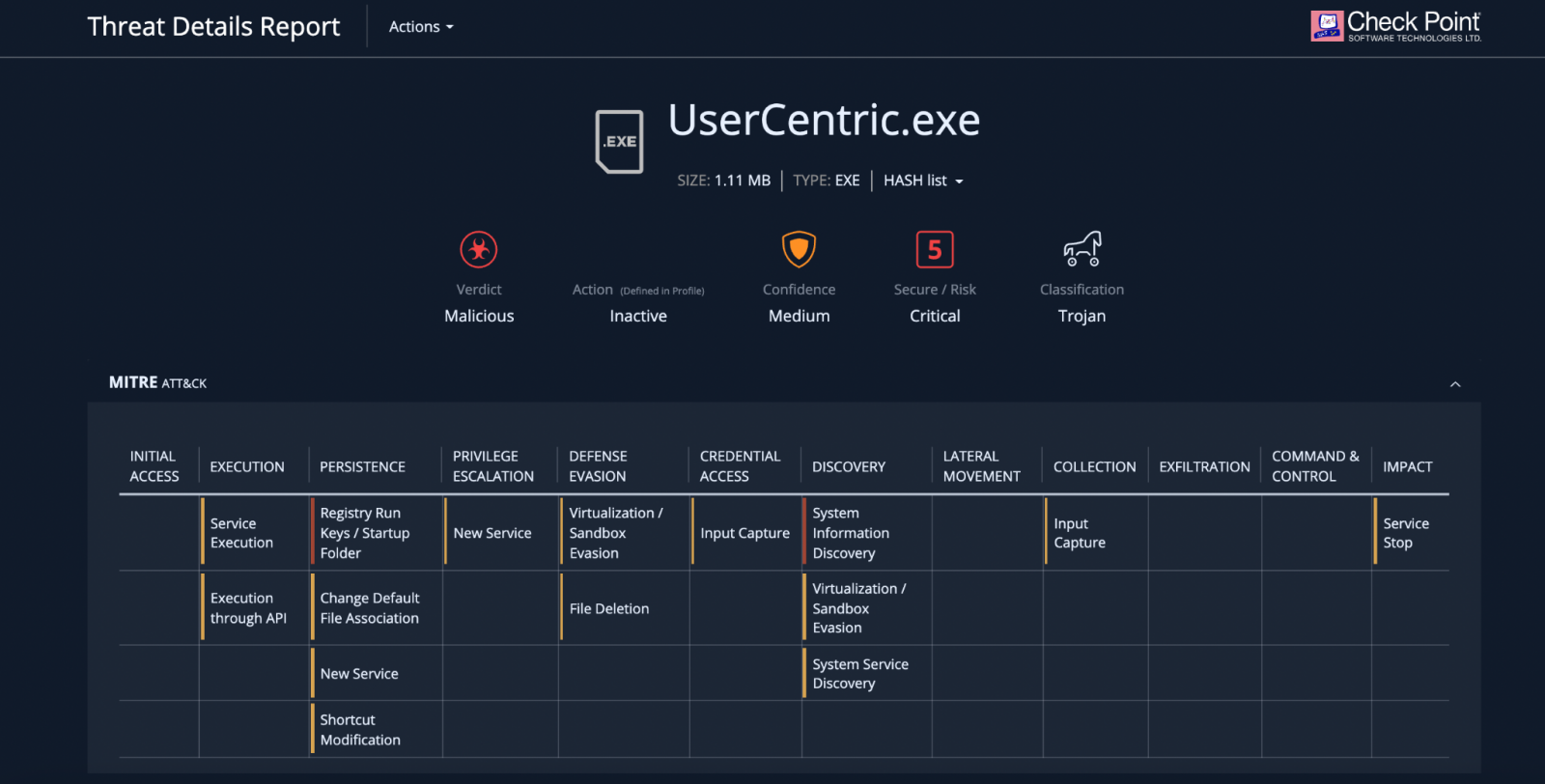
The attacks started in January, the company says in a report today, and the threat actor inserts in a chat an executable file called “User Centric” to trick the user into running it.
Once executed, the malware writes data into the system registry installs DLLs and establishes persistence on the Windows machine.
“In this Teams attack, hackers have attached a malicious Trojan document to a chat thread. When clicked on, the file will eventually take over the user’s computer” – Avanan
The method used to gain access to Teams accounts remains unclear but some possibilities include stealing credentials for email or Microsoft 365 via phishing or compromising a partner organization.
Automatic analysis of the malware distributed this way shows that the trojan can establish persistence through Windows Registry Run keys or by creating an entry in the startup folder.
It also collects detailed information about the operating system and the hardware it runs on, along with the security state of the machine based on the OS version and the patches installed.
Although the attack is quite simple, it may also be very efficient because many users trust files received over Teams, Avanan researchers say.
Also Read: 7 Simple Tips On How To Create A Good Business Card Data
The company analyzed data from hospitals that use Teams and found that doctors use the platform to share medical information unrestricted.
While individuals are typically suspicious of information received over email, due to email phishing awareness training, they exhibit no caution with files received over Teams.
Moreover, Teams provides guest and external access capabilities that allow collaboration with people outside the company. Avanan says that these invitations are usually met by minimal oversight.
“Because of the unfamiliarity with the Teams platform, many will just trust and approve the requests. Within an organization, a user can very easily pretend to be someone else, whether it’s the CEO, CFO or IT help desk” – Avanan
The researchers say that the issue is aggravated by “the fact that default Teams protections are lacking, as scanning for malicious links and files is limited” and “many email security solutions do not offer robust protection for Teams.”
To defend against such attacks, Avanan recommends the following:
• Implement protection that downloads all files in a sandbox and inspects them for malicious content
• Deploy robust, full-suite security that secures all lines of business communication, including Teams
• Encourage end-users to reach out to IT when seeing an unfamiliar file