KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Those using the Mozilla Firefox web browser are left unable to access microsoft.com and its subdomains this week.
Tests by BleepingComputer confirm the issue relates to SSL certificate validation errors. Below we explain what can you do to remedy the issue.
When using Firefox, accessing microsoft.comis not working quite as expected for many around the world.
To confirm, BleepingComputer conducted tests on both Firefox 93.0 and the latest version 95.0 (64-bit) on a macOS BigSur 11.6 device.
Also Read: How to Write an Effective Privacy Statement for Websites

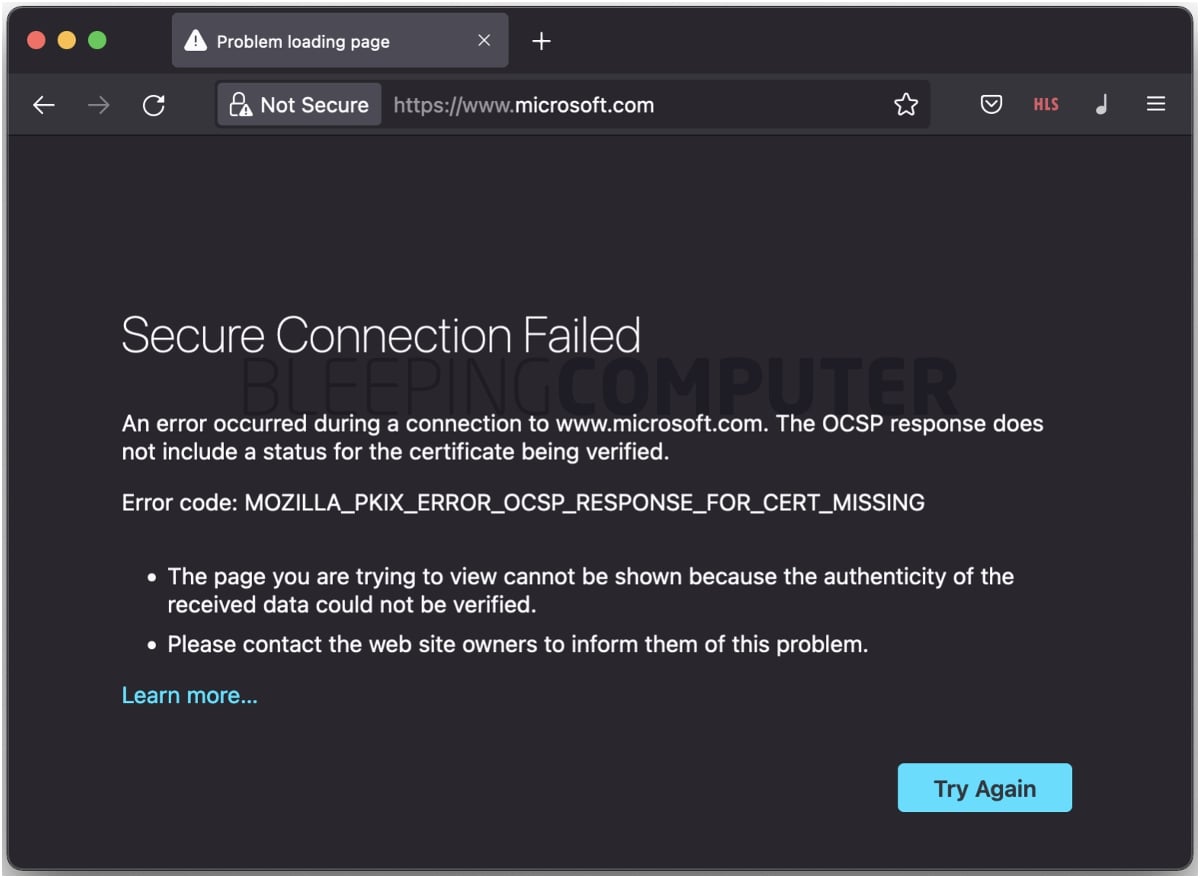
Surely enough, on both versions of Firefox, navigating to https://www.microsoft.com/ throws a ‘Secure Connection Failed’ error:
Earlier this week, reports of Firefox users unable to access select Microsoft subdomains also emerged. These included docs.microsoft.com, answers.microsoft.com, and visualstudio.microsoft.com, among others.
BleepingComputer is unable to reproduce the connection issues on all of these subdomains, but we could not connect to developer.microsoft.com, and partner.microsoft.com, at the time of writing.
It is also possible the error only appears on some but not all attempts due to multiple nameservers associated with each domain.
Apparently, the SSL certificate presented by microsoft.com and its subdomains is not good enough for Firefox—we had no issues accessing the tech giant’s websites on Google Chrome and Safari.
Specifically, the error code ‘MOZILLA_PKIX_ERROR_OCSP_RESPONSE_FOR_CERT_MISSING‘ and the message “The OCSP response does not include a status for the certificate being verified,” help trace down the cause of the issue.
Also Read: Cross Border Data Privacy- A Guide for Singapore Businesses
The Online Certificate Status Protocol (OCSP) is a way for browsers and other client-side applications to check if an SSL certificate has been revoked, as an alternative to relying on traditional revocation lists.
When presented with an SSL certificate, client-side applications can connect to the certificate authority (CA) to verify its revocation status.
The error, however, stems from a concept known as OCSP stapling.
OCSP stapling is a means to improve on the original OCSP standard by eliminating the need for client-side applications to query CA servers for checking a certificate’s status. This reduces the cost associated with making an extra lookup and improving the overall performance and security.
Instead of the client-side application having to make one more request to the CA server to validate the X.509 certificate presented by a website, the website itself makes periodic requests to the CA and retrieves an ephemerally valid signed ‘proof’ of the certificate’s validity.
The certificates presented to client-side apps come appended with this signed time-stamped response that can be trivially verified by the client-side application to ascertain the certificate’s status.
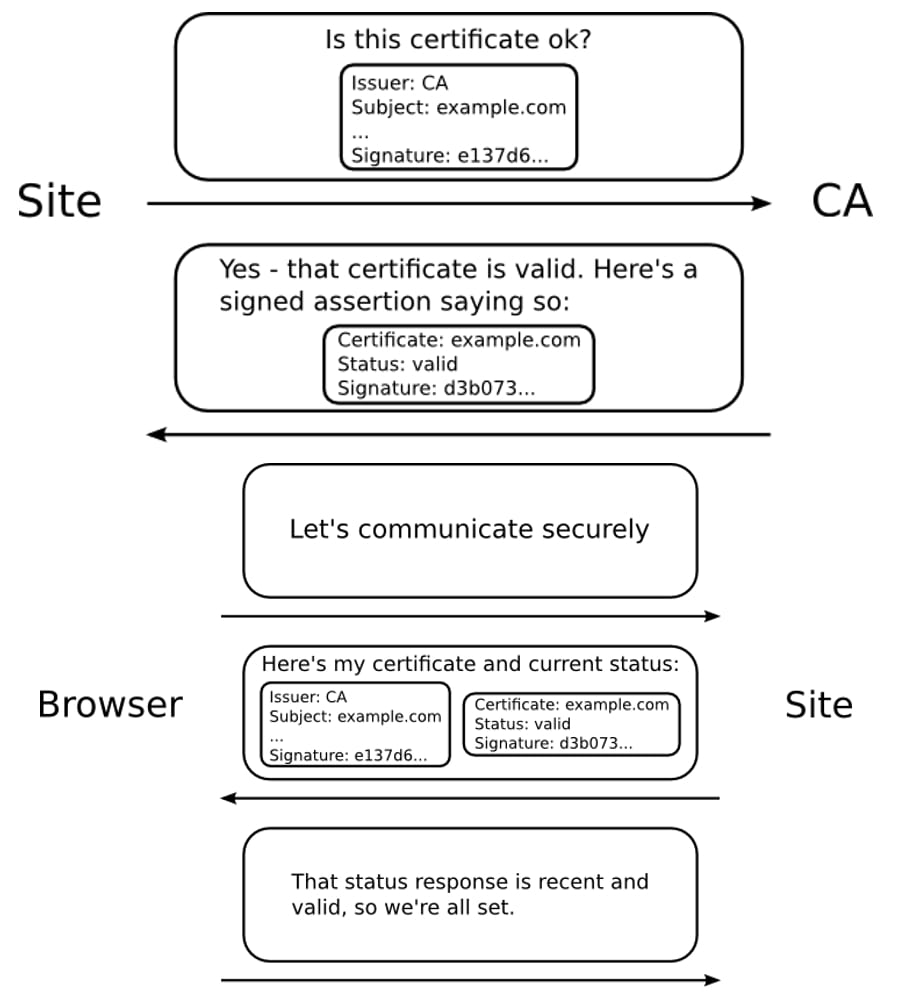
If ‘OCSP stapling’ is enabled on an application, such as a web browser, the application can decide whether terminate the secure connection for certificates deemed invalid, based on the response attached to the certificate.
Or, as Mozilla’s Dana Keeler explains it:
OCSP stapling solves these problems by having the site itself periodically ask the CA for a signed assertion of status and sending that statement in the handshake at the beginning of new HTTPS connections. The browser takes that signed, stapled response, verifies it, and uses it to determine if the site’s certificate is still trustworthy. If not, it knows that something is wrong and it must terminate the connection. Otherwise, the certificate is fine and the user can connect to the site.
But, if Microsoft.com’s SSL certificate is otherwise valid, according to Chrome and Safari, why won’t Firefox accept it?
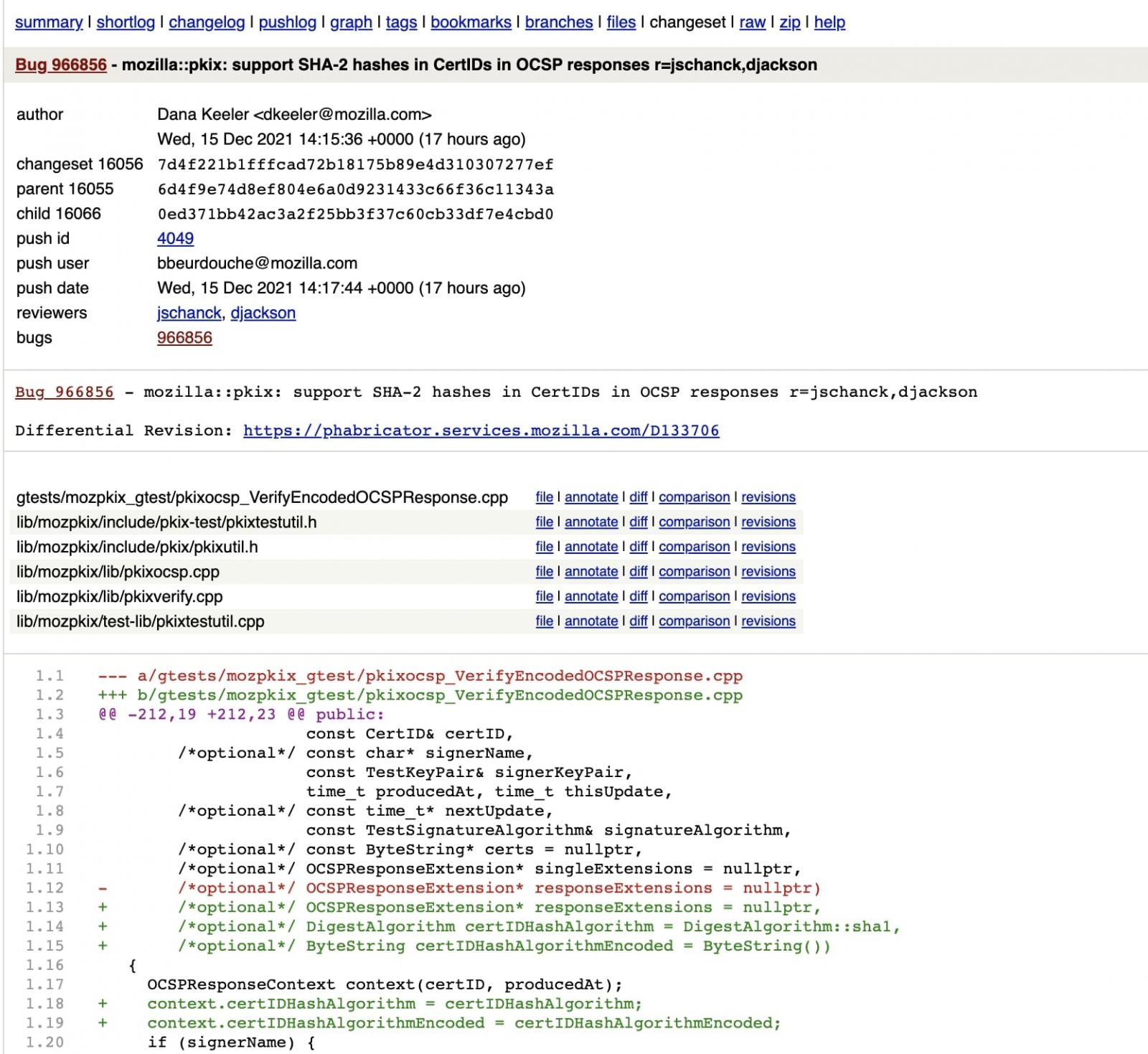
It seems that an 8-year bug in Firefox, or a missing feature, is to blame for the issue.
Firefox did not yet recognize the SHA-2 family of hashes, such as SHA-256, in the CertID fields that are present in OCSP responses it receives.
As such, any certificate containing the SHA-256 hashes, as opposed to the older SHA-1, is deemed invalid and causes Firefox to terminate the connection with the website.
Over the last few hours, Firefox developers have managed to work on a fix that should land in an upcoming version.
A quick workaround to remediate the connection issues is to temporarily disable OCSP stapling in Firefox, as confirmed by BleepingComputer.
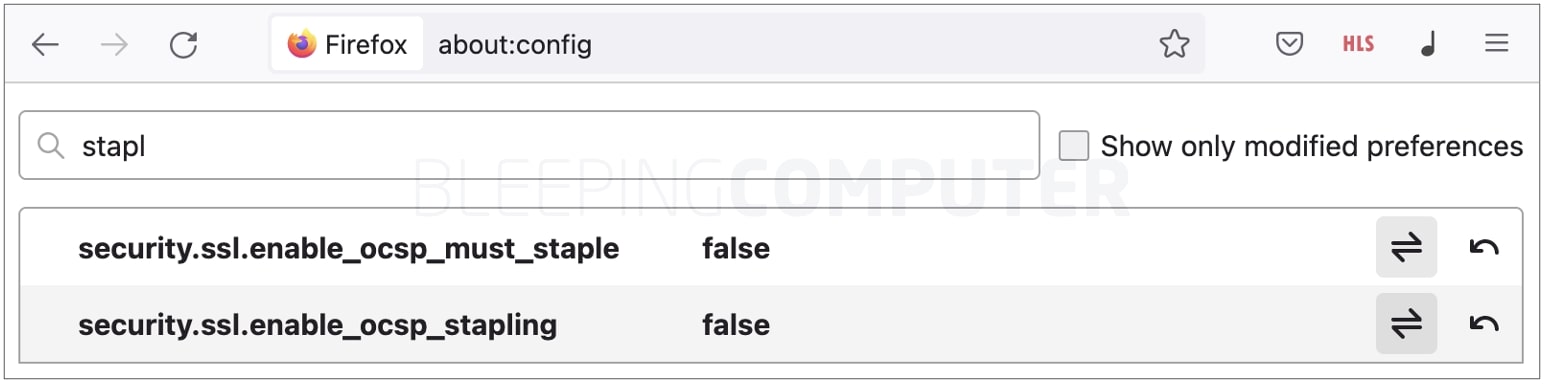
The change takes effect almost instantaneously (so no need to look for a ‘save’ button).
You should now be able to browse microsoft.com and its subdomains without any issues.
Once Firefox does release an update to address the cause, navigate to about:config following the aforementioned steps to set OCSP stapling to ‘true’ once again for a secure browsing experience.
Update 6:01 AM ET: Upcoming Firefox 95.0.1, 96.0b6, and 91.4.1esr releases are expected to become available later today and resolve the issue.