KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new phishing campaign uses a Coinbase-themed email to install an Office 365 consent app that gives attackers access to a victim’s email.
Over the past year, hackers have increasingly used Microsoft Office 365 OAuth apps, otherwise known as consent apps, as part of their attacks.
Consent apps are Office 365 OAuth applications that allow third-parties access to a consenting user’s email account to perform actions on their behalf. These apps are used for legitimate purposes, such as spam filtering, antivirus scanning, or calendaring purposes.
Unfortunately, when someone makes something helpful, threat actors always attempt to abuse them for malicious purposes.
Such is the case with a phishing campaign that pretends to be a “New terms of service” that Coinbase users must read and accept to continue using the service.
Also Read: EU GDPR Articles: Key For Business Security And Success

If a user clicks on the ‘Read and Accept Terms of Service FAQ” link, they will be brought to a legitimate Microsoft asking the user to log in to their Microsoft account. If you look at the URL below, you can also see that the URL asks for the User.Read, Mail.Read, and Mail.ReadWrite permissions on the target’s account.
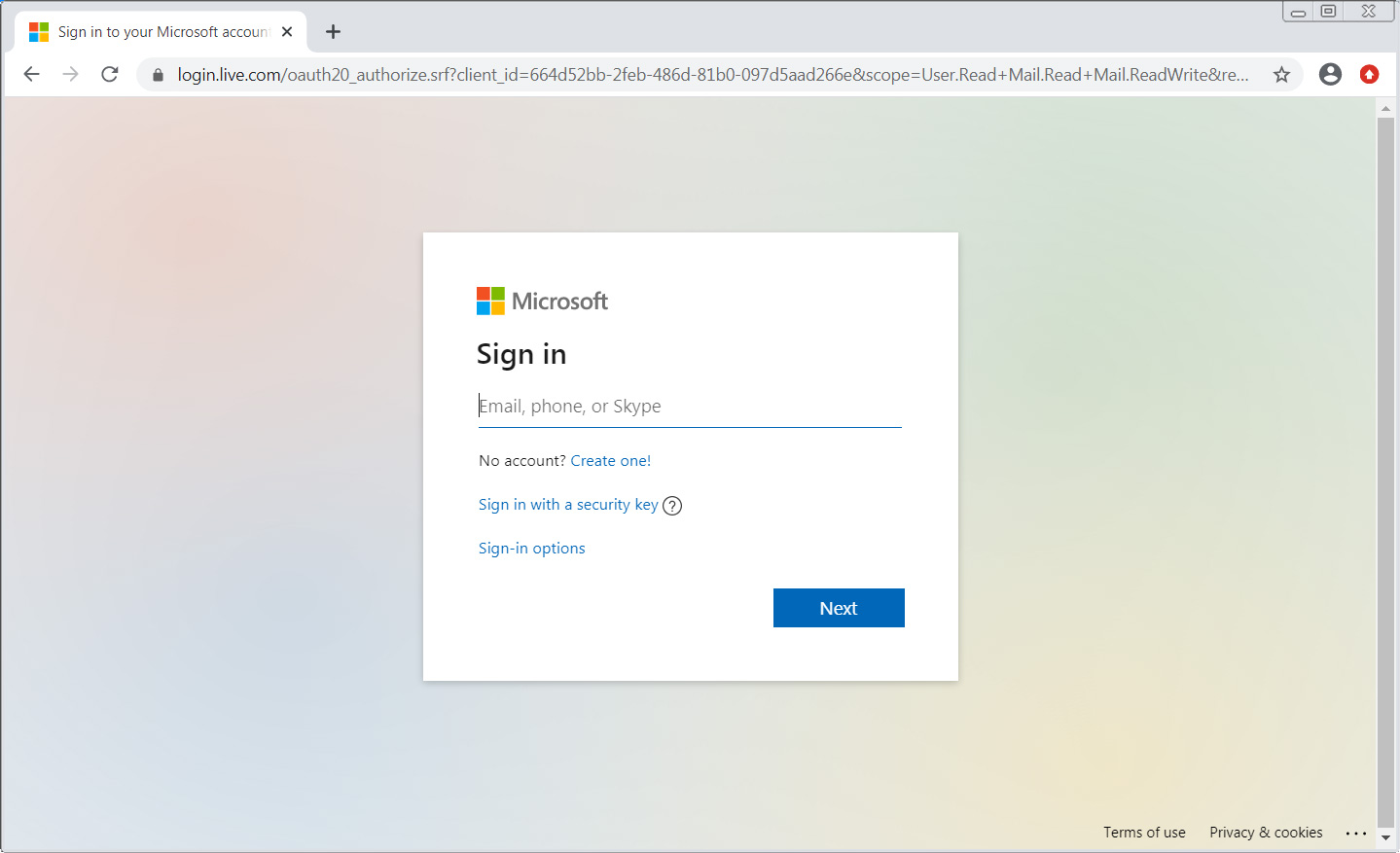
If a user logs in to their Microsoft account, they will be shown a prompt to allow an app from coinbaseterms.app to access their account.
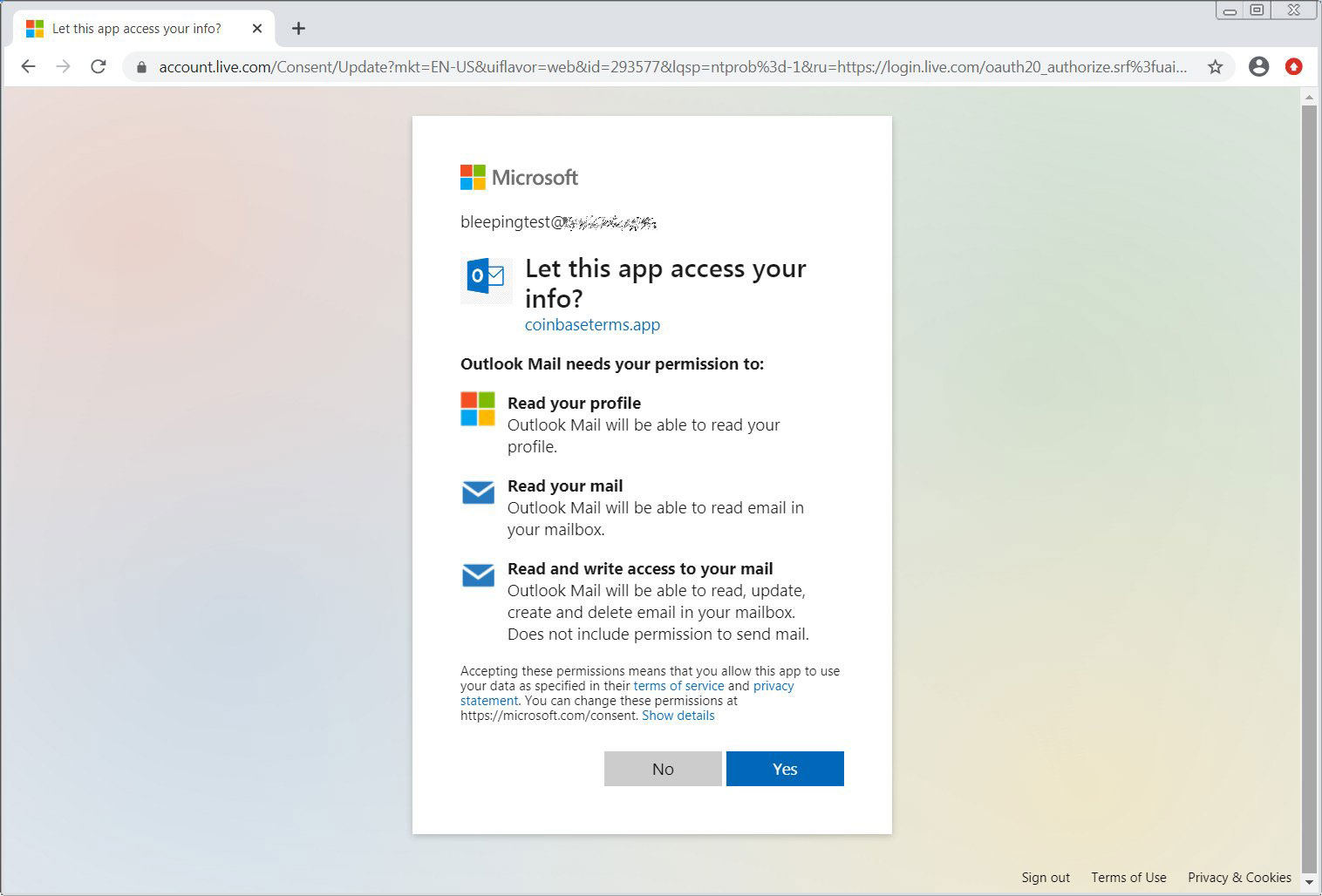
If the user accepts the app’s request, a security token associated with the user will be sent to the app developer. This token allows the attackers to access the user’s Office 365 account from their servers and applications.
Also Read: How Bank Disclosure Of Customer Information Work For Security
When accepting the account, they can perform actions or see data based on the corresponding permissions of the app, which in this case are:
Once the Office 365 user clicks on the ‘Yes’ button, the threat actors will have full access to read the accounts profile and their email.
The Consent app’s permissions do not allow the attackers to send an email on a victim’s behalf, but the Mail.ReadWrite permission does allow an attacker to update a draft message created by the user.
This ability would allow them to search for email drafts and change their contents to perform BEC attacks or further phishing attacks.
If you are an Office 365 user, you can check if there are any user consent apps or services tied to your accounts by going here.
To remove a listed consent, click on its entry, and when that page opens, click on the ‘Remove these permissions’ button to remove it.
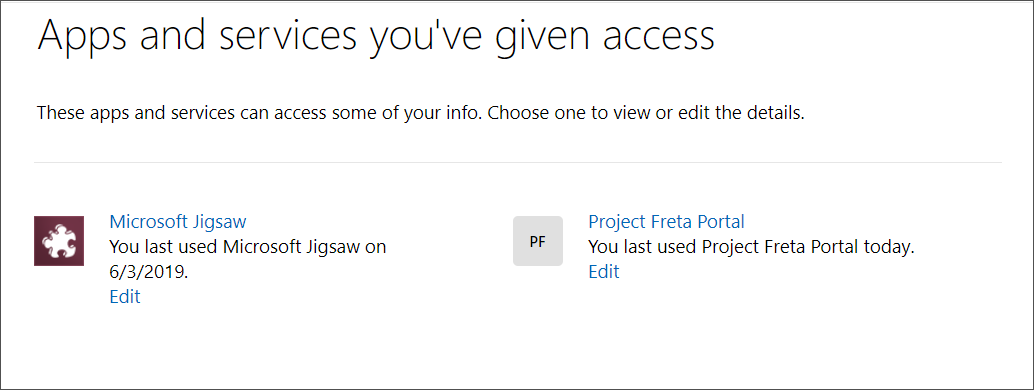
Microsoft Office 365 administrators can also check their organization for users who have OAuth ‘Consent’ addons.
Organizations can also take several measures that should help them further protect their remote workforce from such attacks.
These steps include educating employees to spot consent phishing tactics, requiring the use of publisher verified apps, and only allow employees to OAuth apps trusted by the organization or provided by verified publishers.