KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Phishing actors are actively abusing Calendly to kick off a clever sequence to trick targets into entering their email account credentials on the phishing page.
Calendly is a very popular free calendar app with Zoom integration, used for scheduling meetings and appointments, and is commonly used by organizations to send out invitations for upcoming events.
As such, using it to send out malicious links blends very well with the daily work background of most victims, so it’s unlikely for these attempts to raise suspicions.
Also, emails generated and sent by legitimate platforms are commonly considered trustworthy by email security tools, so they tend to reach targetted inboxes rather than the spam folder.
Finally, Calendly allows new users to register on the platform without entering credit card information or any other identification proof, making it an easy platform to abuse.
Also Read: AI Auditing Framework: Draft Guidance for Organizations
The first signs of Calendly abuse started towards the end of February, as reported by analysts at INKY, who have shared their report with Bleeping Computer before publication.
The phishing attack begins with phishing emails generated on the Calendly platform that inform the recipient they received new Fax documents.
To create these emails, the threat actors abused a Calendly feature that allows users to create customized invite emails and an “Add Custom Link” function to insert a malicious link on the event page.
That link is embedded on a “View Documents” button and injected into the calendar screen, so if clicked, it takes the recipient to the actual phishing landing page used to steal login credentials.
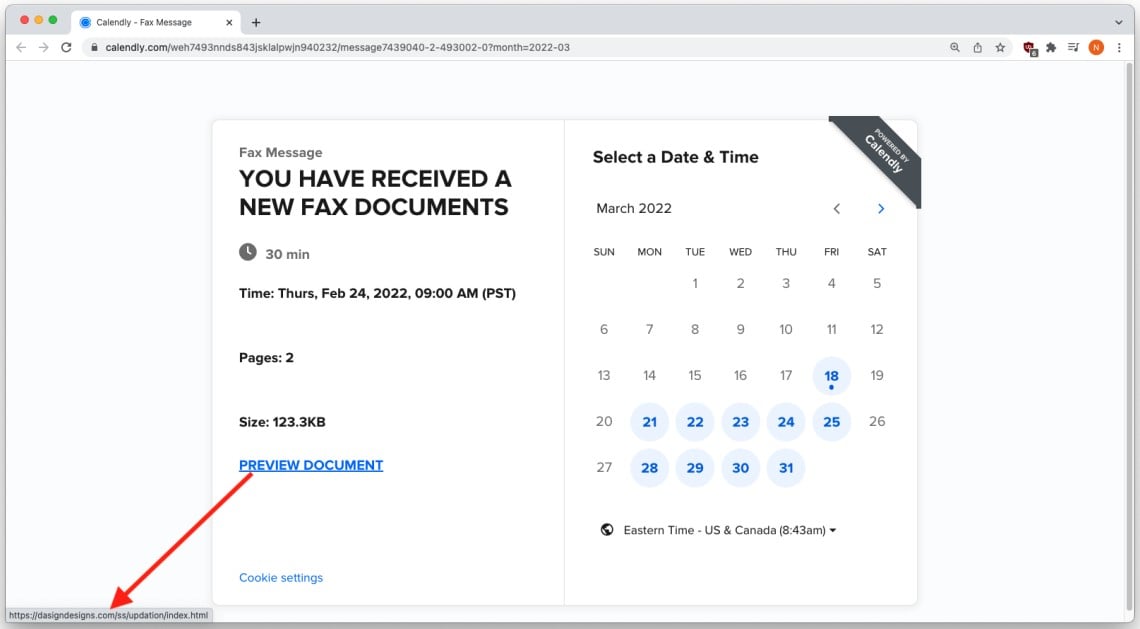
INKY discovered that no matter the lures in this phishing campaign, the landing page always impersonated a Microsoft login form with the document supposedly blurred in the background.
Any credentials entered in the dialog will go straight to the threat actors, while the victim will be prompted to enter them again due to supposedly entering a wrong password.
Also Read: How to Make Data Protection Addendum Template in Simple Way
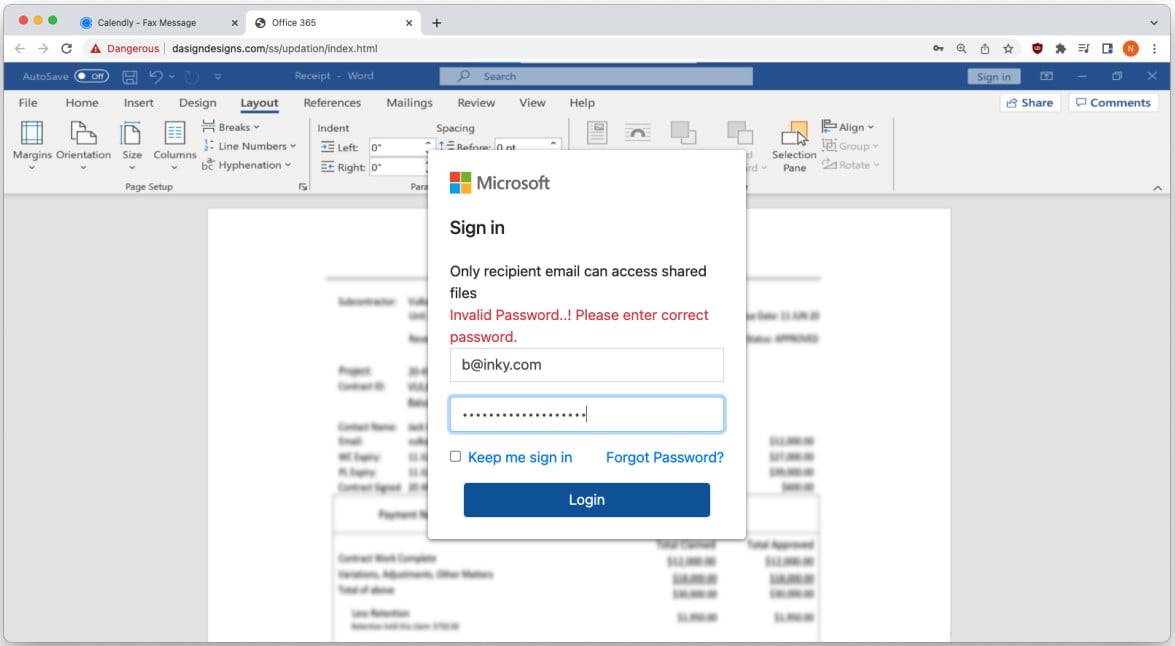
This is a widespread trick in phishing campaigns today, as forcing the user to enter their credentials twice minimizes the chances of stealing passwords with typo errors and sometimes even helps in snatching two account credentials.
After the second attempt, the victim is automatically redirected to the domain of the email account they entered to minimize the chances of the victim realizing the compromise.
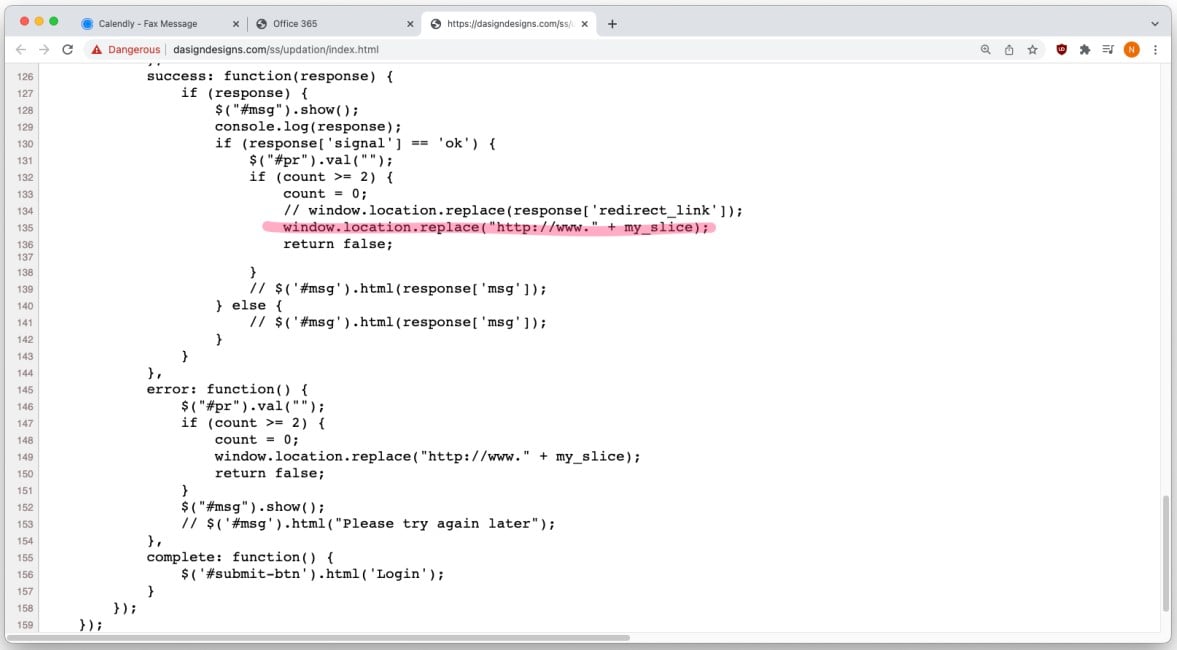
Although this is the first time phishing actors have abused the Calendly platform, all other tricks employed in this campaign are pretty standard.
These include generating malicious messages sent from a legitimate online service, asking the user to log in to view a blurred document in the background, forcing the victims to enter their credentials twice, and redirecting them to a trustworthy website at the end.
Two obvious signs of fraud in this campaign are the requirement to use Microsoft SharePoint credentials to view Calendly-hosted content and the URL on the phishing page, which is neither on the Microsoft nor on the Calendly domains.
Finally, using a password manager is an easy way around all these tricks, particularly beneficial to careless users, as if the URL on the login page doesn’t match the one stored in the vault, the credentials won’t be filled out.