KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





Hackers who normally distributed malware via phishing attachments with malicious macros gradually changed tactics after Microsoft Office began blocking them by default, switching to new file types such as ISO, RAR, and Windows Shortcut (LNK) attachments.
VBA and XL4 Macros are small programs created to automate repetitive tasks in Microsoft Office applications, which threat actors abuse for loading, dropping, or installing malware via malicious Microsoft Office document attachments sent in phishing emails.
The reason for the switch is Microsoft announcing that they would end the massive abuse of the Office subsystem by automatically blocking macros by default and making it harder to activate them.
Although it took Microsoft a little longer to implement this Microsoft Office change, the block finally entered into effect last week.
However, the initial announcement alone convinced malware operators to move away from macros and begin experimenting with alternative methods to infect victims.
Also Read: Spam Control Act: 4 best practices organizations must consider
In a new report by Proofpoint, researchers looked at malicious campaign stats between October 2021 and June 2022 and identified a clear shift to other methods of payload distribution, recording a decrease of 66% in the use of macros.
At the same time, the use of container files such as ISOs, ZIPs, and RARs has grown steadily, rising by almost 175%.
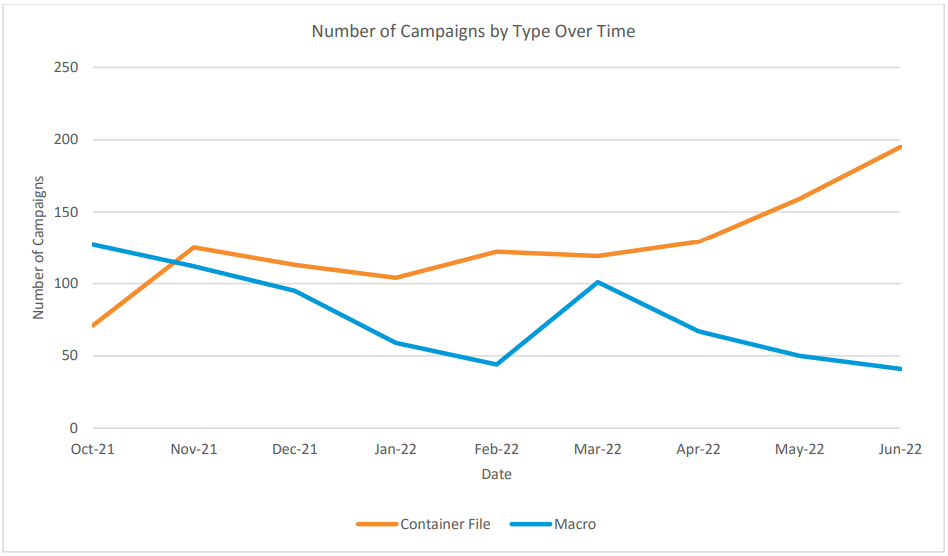
The use of LNK files exploded after February 2022, the time of Microsoft’s announcement, increasing by a whopping 1,675% compared to October 2021, and being the weapon of choice of ten individual threat groups tracked by Proofpoint.
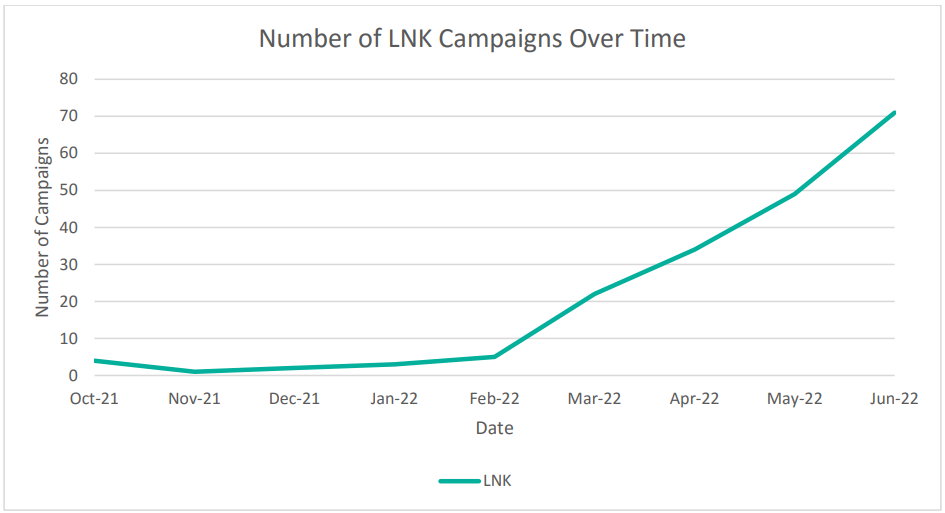
We have reported on the use of LNK files by Emotet, Qbot, and IcedID, in all cases masquerading as a Word document to trick the recipient into opening it.
Also Read: How do ransomware attacks happen?: Here are 7 ways to protect you from it
However, these link files can be used to execute almost any command the user has permission to use, including executing PowerShell scripts that download and execute malware from remote sources.
Finally, Proofpoint also observed a significant increase in the use of HTML attachments adopting the HTML smuggling technique to drop a malicious file on the host system. However, their distribution volumes continue to remain small.
While seeing macros becoming an obsolete method of payload distribution and initial infection is a positive development, the threat has merely shifted rather than being addressed or reduced.
The question that needs answers now is how that change impacts the effectiveness of the malware campaigns, as convincing recipients to open .docx and .xls files was a lot easier than asking them to unpack archives and open files whose names end with .lnk.
Furthermore, to bypass detection by security software, many phishing campaigns now password-protect archive attachments, adding another burdensome step a target must take to access the malicious files.
From that perspective, threat actors relying on phishing emails might be running out of good options, and their infection rates may have dropped as a result.
Finally, email security solutions now have a narrower spectrum of potential risks to evaluate, improving their chances of catching a risky file.