KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Threat researchers investigating malware used to target companies in the aerospace and telecommunications sectors discovered a new threat actor that has been running cyber espionage campaigns since at least 2018.
Dubbed ShellClient, the malware is a previously undocumented remote access trojan (RAT) built with a focus on being stealthy and for “highly targeted cyber espionage operations.”
Researchers attributed ShellClient to MalKamak, a previously undisclosed threat actor that used it for reconnaissance operations and for stealing sensitive data from targets in the Middle East, the U.S., Russia, and Europe.
Also Read: PDP Act (Personal Data Protection Act) Laws and Regulation
The ShellClient RAT appeared on the radar of threat researchers in July during an incident response engagement that revealed cyber espionage activity now referred to as Operation GhostShell.
Cybereason Nocturnus and Incident Response Teams analyzed the malware and observed that it ran on infected machines disguised as “RuntimeBroker.exe,” a legitimate process that helps with permission management for apps from Microsoft Store.
The ShellClient variant used for Operation GhostShell shows a compilation date of May 22, 2021, and is referred to as version 4.0.1.
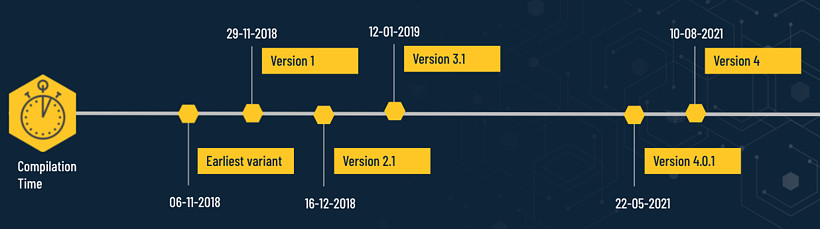
The researchers found that its evolution started since at least November 2018 “from a simple standalone reverse shell to a stealthy modular espionage tool.”
With each of the six iterations discovered, the malware increased its functionality and switched between several protocols and methods for data exfiltration (e.g. an FTP client, Dropbox account):
In its investigation, Cybereason looked for details that would link ShellClient to a known adversary but concluded that the malware is operated by a new nation-state group they named MalKamak, which is likely connected to Iranian hackers, as indicated by code style overlap, naming conventions, and techniques.
Also Read: What Does Resolution Of Data Really Means
“While some possible connections to known Iranian threat actors were observed, our conclusion is that MalKamak is a new and distinct activity group, with unique characteristics that distinguish it from the other known Iranian threat actors” – Cybereason
The researchers say that MalKamak focuses on highly targeted cyber espionage operations, a theory supported by the low number of samples discovered in the wild or telemetry data since 2018.
Furthermore, the path for debugging files available in some ShellClients samples suggests that the malware is part of a confidential project from a military or intelligence agency.
Cybereason created a brief summary of how MalKamak runs, its capabilities, infrastructure, and the types of victims it is interested in.
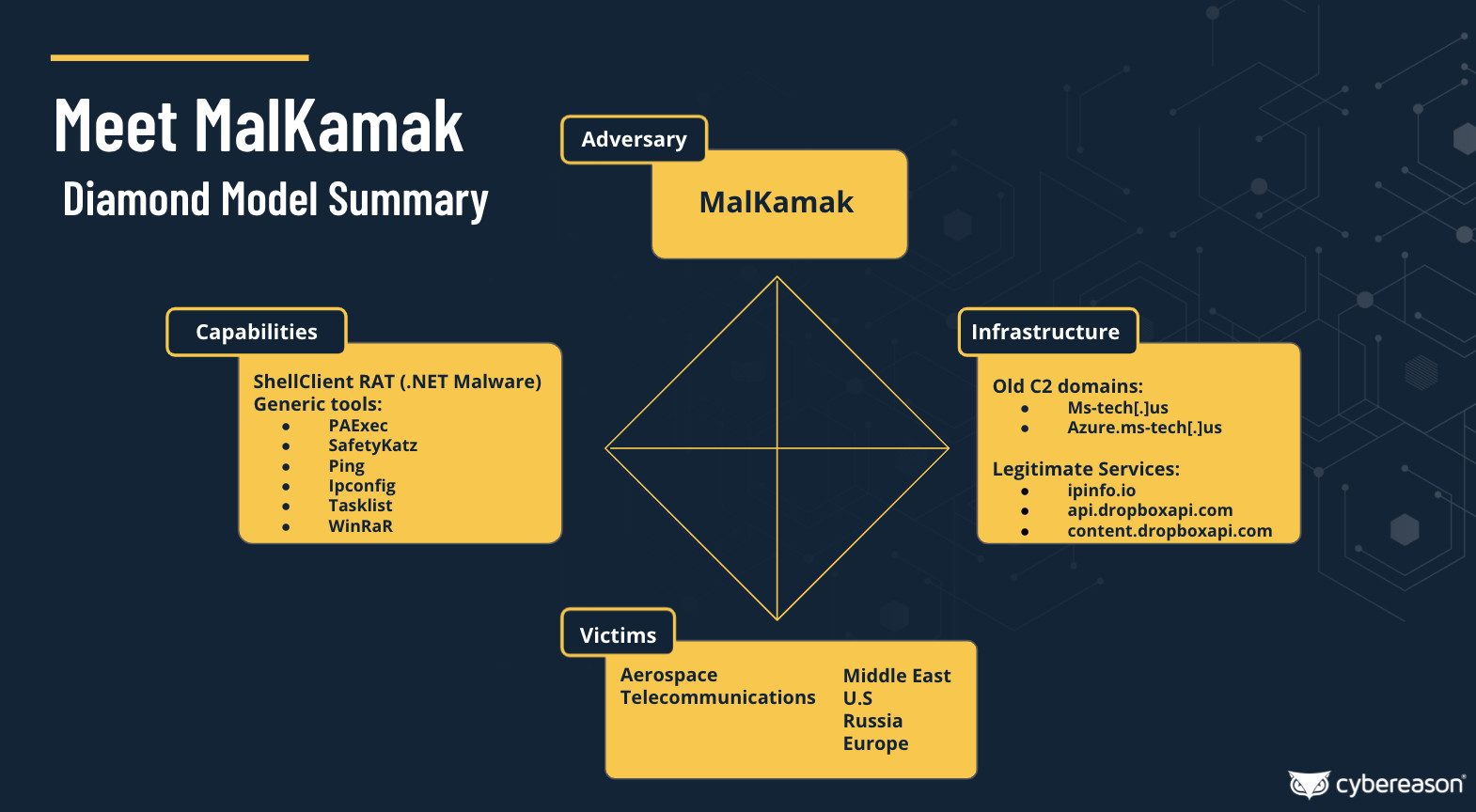
Cybereason makes available a set of indicators of compromise for all versions and samples of ShellClient they uncovered, command and control servers, user agents, encryption keys, and related files.
In a separate technical document, the researchers provide full analysis of all the variants they found during incident response engagements.