KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Threat actors are abusing Google’s free productivity tools and services to create convincing phishing campaigns that steal your credentials or trick you into installing malware.
Google offers a wide array of free software and services that allow users to create documents, spreadsheets, online forms, and free websites. These tools are used by students, teachers, consumers, and the enterprise as an easy way to share documents, conduct surveys, or even create sites for free.
Unfortunately, if a service is free for us, it is also free for threat actors to abuse them as they see fit.
In a new report by email security firm Armorblox, researchers illustrate how threat actors are creating elaborate phishing campaigns using Google services that not only look convincing but also evade detection.
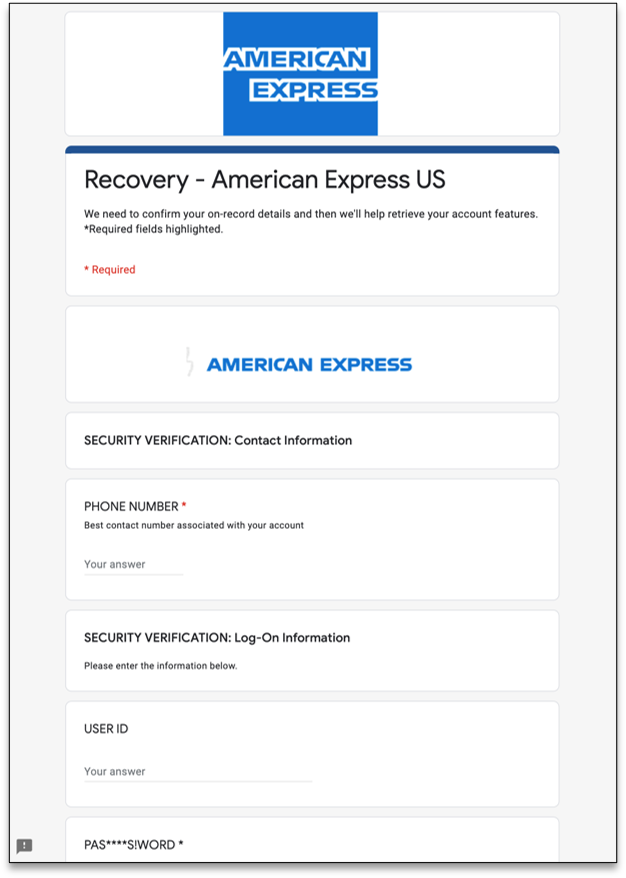
The first Google tool we will look at is the free form creation service called Google Forms that lets anyone create free online surveys that can then be sent to other users.
Threat actors, though, are abusing Google Forms to create elaborate forms that attempt to steal your credentials, like the fake American Express account recovery form below. Threat actors can then collect any submitted information at a later date.
Also Read: A Look at the Risk Assessment Form Singapore Government Requires
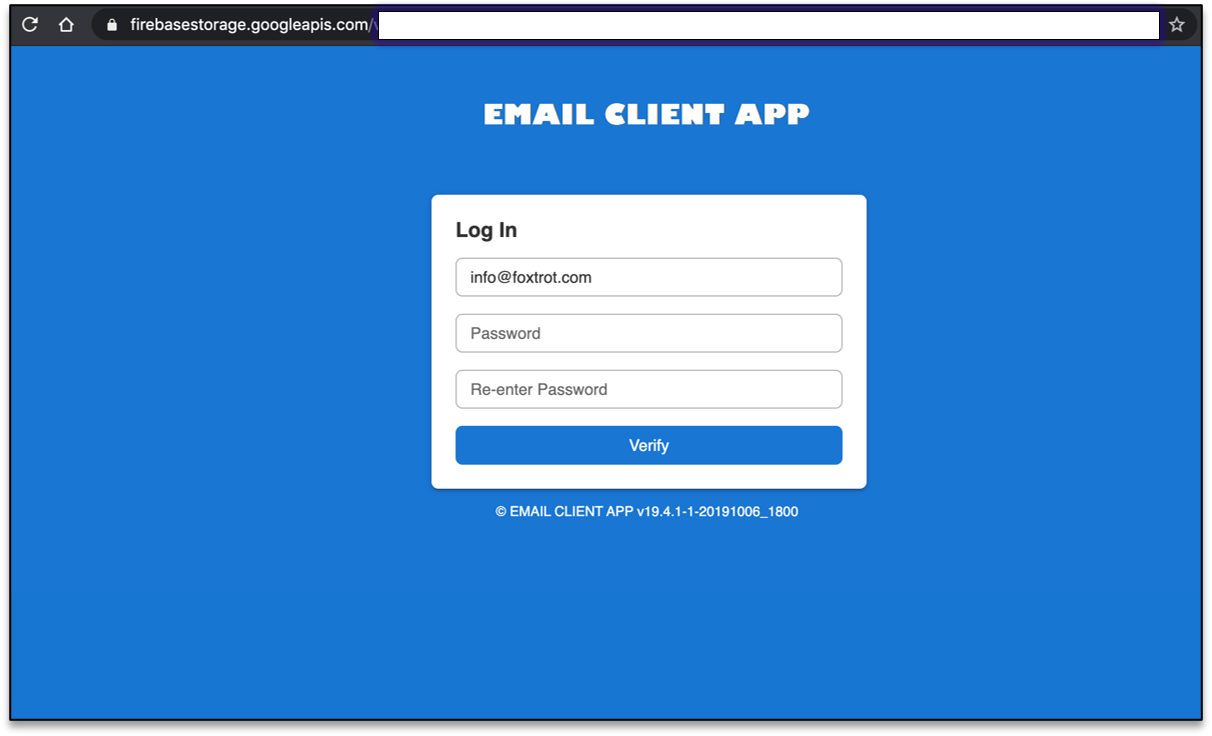
Google Firebase is a developer platform used to create mobile and web applications hosted in the cloud.
Threat actors are using Firebase to create phishing landing pages that can include images, dynamic content, and process forms. As Firebase pages utilize a generic https://firebasestorage.googleapis.com URL, Armorblox states they will not be “blocked by any security filters due to its inherent legitimacy.”
Below you can see a phishing email login form created on Firebase.
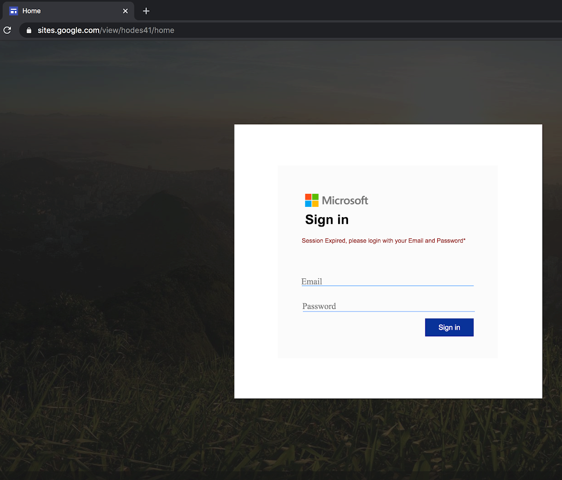
Google offers a free web hosting platform called Google Sites that allows users to create simplistic web sites that are served from the sites.google.com domain.
In an example shared by Armorblox, we can see a Google Sites page that hosts a fake Microsoft sign-in form to steal a user’s Microsoft account credentials.
Finally, the most common Google service being used in phishing scams is Google Docs. Not only is this service used to redirect recipients to credential theft and accounting scams, but also to deliver malware.
As Google Docs is so heavily used, almost all new documents will bypass secure email gateways until they have been identified as malicious.
“Since Google Docs is ever present in our daily lives, the average recipient wouldn’t be surprised to see a Google Docs link in an email from a colleague. It won’t be blocked by any email security filter either – not on Day 0, at any rate. Using a Google Doc in this email is meant to trick both the recipient’s eye test and traditional security layers,” Armorblox explains in their report.
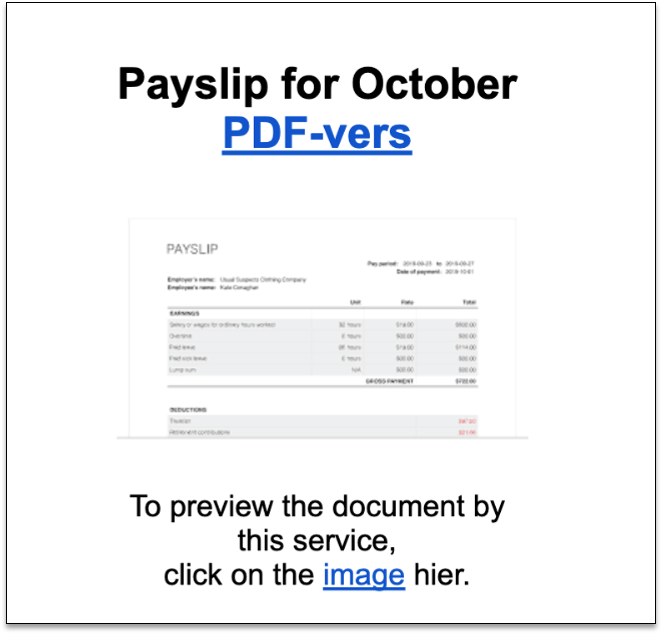
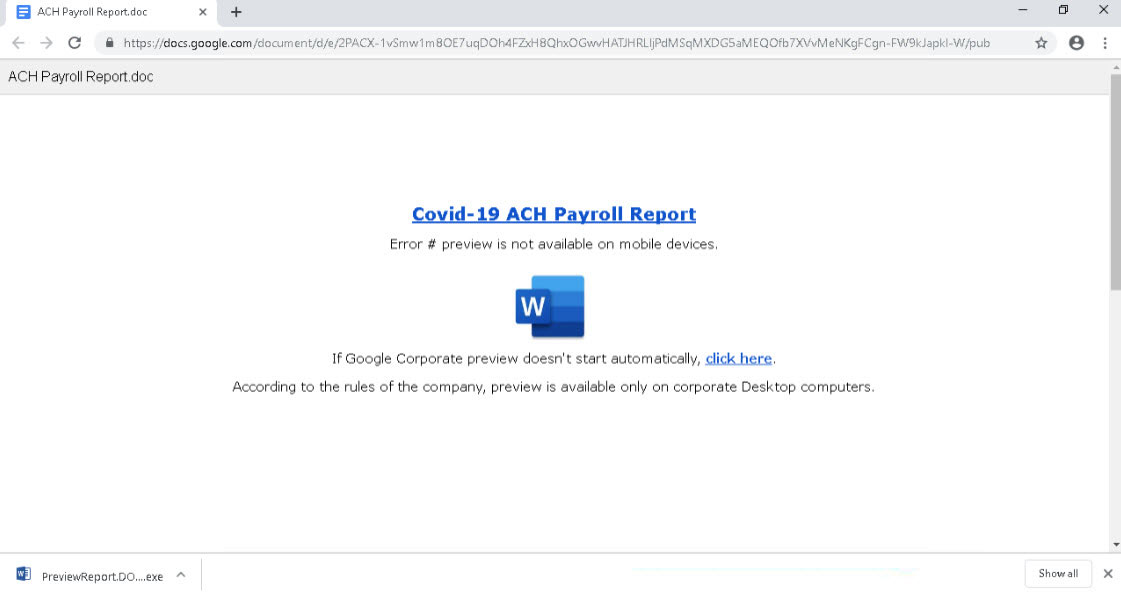
For example, you can see a fake ‘payslip’ download page that redirects users to a page that steals credentials.
Google docs is also heavily used in BazarLoader malware campaigns as an intermediary page to download malware disguised as invoices, COVID-19 information, and other types of documents.
Also Read: How to Send Mass Email Without Showing Addresses: 2 Great Workarounds
While this report focused on the abuse of Google services, threat actors also utilize free services from other companies, including Dropbox, Canva, and Azure.
To protect yourself from phishing scams like these, Armorblox recommends that you:
Even if you follow all of these recommendations, it is critical to treat all emails with links and attachments as suspicious.
Don’t simply click on links or open attachments, instead scan them first or check with your network administrator if you’re not sure. It is also always good to call the sender by phone to confirm if they sent the email.
Just be sure not to use the phone number listed in the email, as it could be the threat actor’s number instead.