



Phishing actors abuse Google’s SMTP relay service to bypass email security products and successfully deliver malicious emails to targeted users.
According to a report from email security firm Avanan, there has been a sudden uptick in threat actors abusing Google’s SMTP relay service starting in April 2022.
The company has detected at least 30,000 emails in the first two weeks of April being distributed through this method.
Google offers an SMTP (Simple Mail Transfer Protocol) relay service that can be used by Gmail and Google Workspace users to route outgoing emails.
Businesses use this service for various reasons, ranging from not having to manage an external mail server to using it for marketing emails, so their mail server does not get added to a block list.
Avanan states that threat actors can utilize Google’s SMTP relay service to spoof other Gmail tenants without being detected, as long as those domains do not have a DMARC policy configured with the ‘reject’ directive.
Also Read: 7 Client Data Protection Tips to Keep Customers Safe
Domain-based Message Authentication, Reporting & Conformance, or DMARC, is an email authentication protocol that allows domain owners to specify what should happen if an email is spoofing their domain.
To do this, domain owners create a special DMARC DNS record that includes a directive telling a mail server what to do. These directives are ‘none’ (do nothing with the spoofed email), ‘quarantine’ (place email in the spam folder), or ‘reject’ (do not accept email at all).
The new phishing campaigns use the ‘smtp-relay.gmail.com’ SMTP server, which is a trusted server and is thus commonly placed on allow lists by email gateways and spam filtering services.
For example, the following email, spotted by Avanan, appears as if it comes from Trello.com, but it’s in reality from jigokar.com and passed through Google’s relay service.
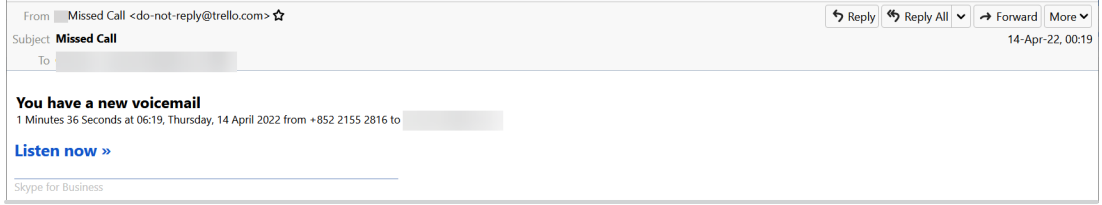
As previously stated, these attacks only work if the impersonated entity has set its DMARC policy to “none,” which is not as uncommon as you may think. For example, dell.com, wikipedia.org, yandex.ru, pornhub.com, bit.ly, and live.com have DMARC policies set to ‘none.’
Setting strict DMARC policies is a recommended security practice as it helps prevent threat actors from spoofing domains.
In Trello’s case, DMARC policy has been disabled due to using other security tools, making the impersonation possible.
The emails are likely bypassing spam detections because all Gmail tenants who use this relay likely set up SPF records that place Google’s SMTP relay service on the trusted sender list for their domain.
Also Read: 9 Policies for security procedures examples
When a threat actor spoofs a Gmail tenant’s domain, it passes the SPF record, and as DMARC is not set to ‘reject,’ it will be successfully delivered to the targeted user’s inbox.
While these threat actors are abusing Google’s relay service, Avanan says that any other relay service is succeptible to the same type of abuse.
Avanan says they reported this abuse to the Gmail team on April 23, 2022.
Bleeping Computer has contacted Google with further questions and if it’s planning to take additional measures against this abuse, and a spokesperson has told us the following:
We have built-in protections to stop this type of attack. This research speaks to why we recommend users across the ecosystem use the Domain-based Message Authentication, Reporting & Conformance (DMARC) protocol. Doing so will defend against this attack method, which is a well-known industry issue.
Details on how users can configure their environments appropriately can be found here: https://support.google.com/a/answer/2956491?hl=en and here: https://support.google.com/a/answer/10583557
There’s nothing unique to Workspace here, it speaks to how email standards operate across the industry. This research doesn’t reflect many of the layered defenses which keep customers safe, such as DMARC and email abuse filtering.
Checking the sender’s address to spot a malicious spoofing attempt isn’t enough against this type of attack, so checking the full headers when you’re unsure would be an excellent place to start.
Additionally, when links are embedded in the message body, hover over them to check the destination instead of clicking. Sometimes, merely visiting harmful sites is enough for malware to be dropped on your system.
Finally, if the message contains any attachments, especially if these are of risky formats, do not download and do not open them.