KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Yesterday, GitHub announced rolling out a mysterious HTTP header on all GitHub Pages sites.
GitHub Pages enables users to create websites right from within their GitHub repository.
And it turns out, this header, now being returned by GitHub sites, is actually meant for website owners to opt-out of Google FLoC tracking.
BleepingComputer also noticed the entire github.com domain had this header set, indicating GitHub did not want its visitors to be included in Google FLoC’s “cohorts” when visiting any GitHub page.
As previously reported by BleepingComputer, Google FLoC is a newer technology to replace the traditional third-party cookie tracking used by ad networks and analytics platforms to track users around the web.
The privacy-centric FLoC, on the other hand, aims to replace tracking technologies like third-party cookies and localStorage with what is being called “cohorts.”
As opposed to servers (or ad networks) tracking users across the world wide web and recording their browsing history, FLoC hands off this responsibility to the user’s individual web browser.
That is, every Google Chrome web browser instance selected as a part of the FLoC trial would be lumped with specific “cohorts,” or groups that most closely represent their recent web browsing habits.
Thousands of browsers with identical browsing history (belonging to the same “cohort”) stored locally will have a shared “cohort” identifier assigned, which will be shared with a site when requested.
Also Read: In Case You Didn’t Know, ISO 27001 Requires Penetration Testing
As Google explains it:
“FLoC doesn’t share your browsing history with Google or anyone.”
“This is different from third-party cookies, which allow companies to follow you individually across different sites.”
“FLoC works on your device without your browsing history being shared. Importantly, everyone in the ads ecosystem, including Google’s own advertising products, will have the same access to FLoC,” explained Google in a blog post.
However, Google’s proposal to replace third-party tracking cookies with FLoC has been met with resistance from many industry players including EFF, Microsoft, Mozilla Firefox, Vivaldi, Brave, and DuckDuckGo, who are against any kind of user tracking.
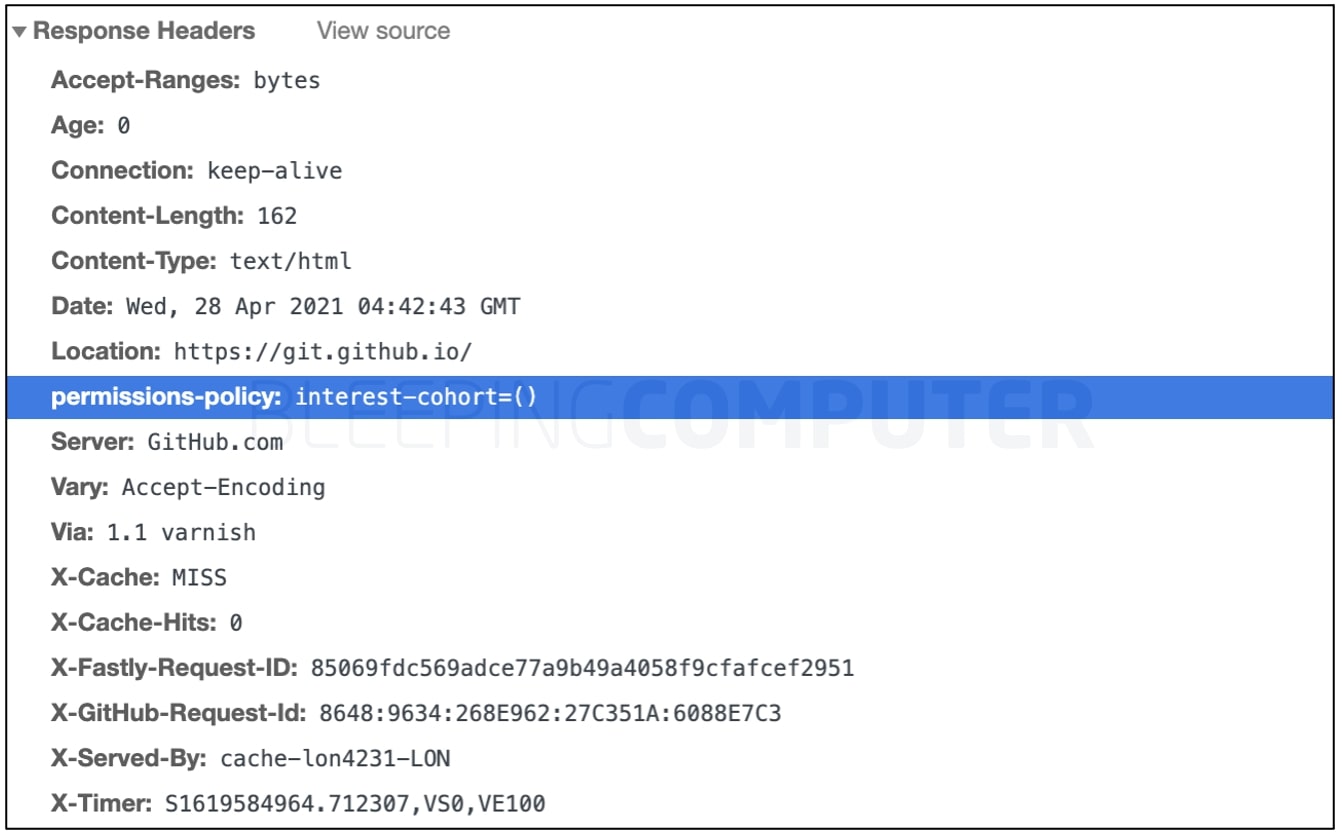
As reported by BleepingComputer earlier, website owners that did not wish to take part in FLoC could block it by issuing the following HTTP request header to their visitors:Permissions-Policy: interest-cohort=()
This header allows sites to opt-out of FLoC, in the sense, visits to sites returning this HTTP header will be ignored by web browsers when generating cohort data for a user.
As seen by BleepingComputer, both the *.github.com domain and GitHub Pages sites hosted on *.github.io are returning this HTTP header at the time of writing:
Interestingly, GitHub’s announcement on the topic is rather succinct and has no mention of Google FLoC anywhere in it:
“All GitHub Pages sites served from the github.io domain will now have a Permissions-Policy: interest-cohort=() header set.”
“Pages sites using a custom domain will not be impacted,” concludes GitHub’s blog post released yesterday.
Users can check if their web browser has been selected to be a part of the FLoC pilot experiment by following the instructions provided at EFF’s AmIFloced.org.
Also Read: 4 Considerations In The PDPA Singapore Checklist: The Specifics
At this time, FLoC is expected to roll out among “a small percentage of users” based in Australia, Brazil, Canada, India, Indonesia, Japan, Mexico, New Zealand, the Philippines, and the U.S, according to Google.