KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A large-scale campaign involving over 800 compromised WordPress websites is spreading banking trojans that target the credentials of Brazilian e-banking users.
The trojan used in this campaign is called ‘Chaes,’ and according to researchers from Avast, its been actively spreading since late 2021.
Although the security firm notified the Brazilian CERT, the campaign is ongoing, with hundreds of websites still compromised with malicious scripts that push the malware.
Also Read: How To Anonymised The Data: What Are The Importance Of This?
When the victim visits one of the compromised websites, they are served with a pop-up that requests them to install a fake Java Runtime app.
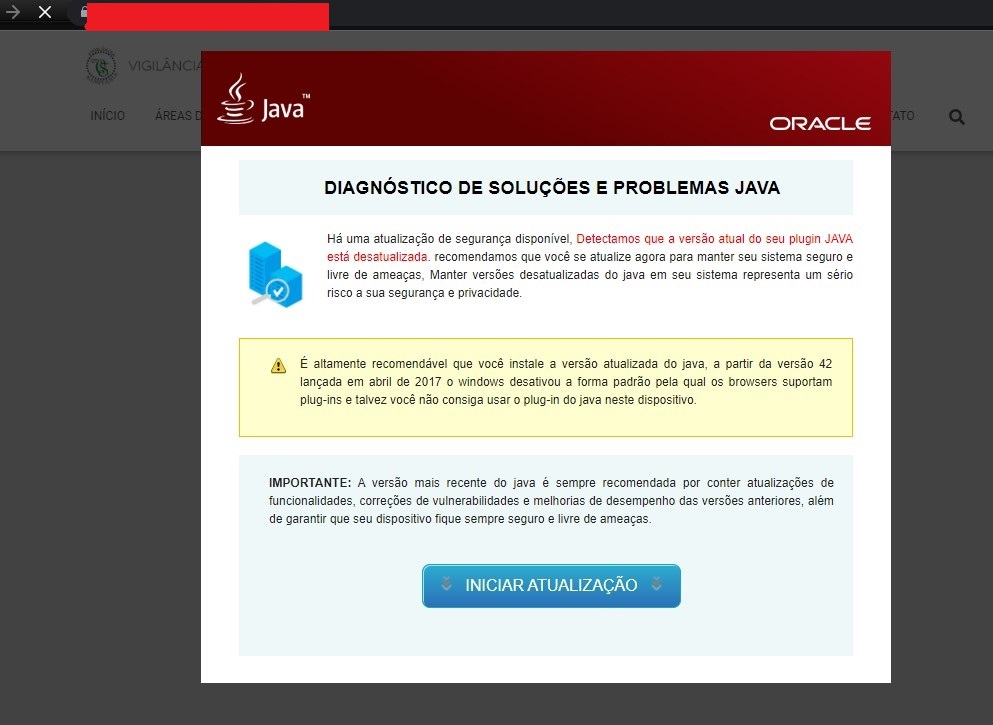
The MSI installer contains three malicious JavaScript files (install.js, sched.js, sucesso.js) that prepare the Python environment for the next stage loader.
The sched.js script adds persistence by creating a Scheduled Task and a Startup link, and sucesso.js is responsible for reporting the status to the C2.
Meanwhile, the install.js script performs the following tasks:
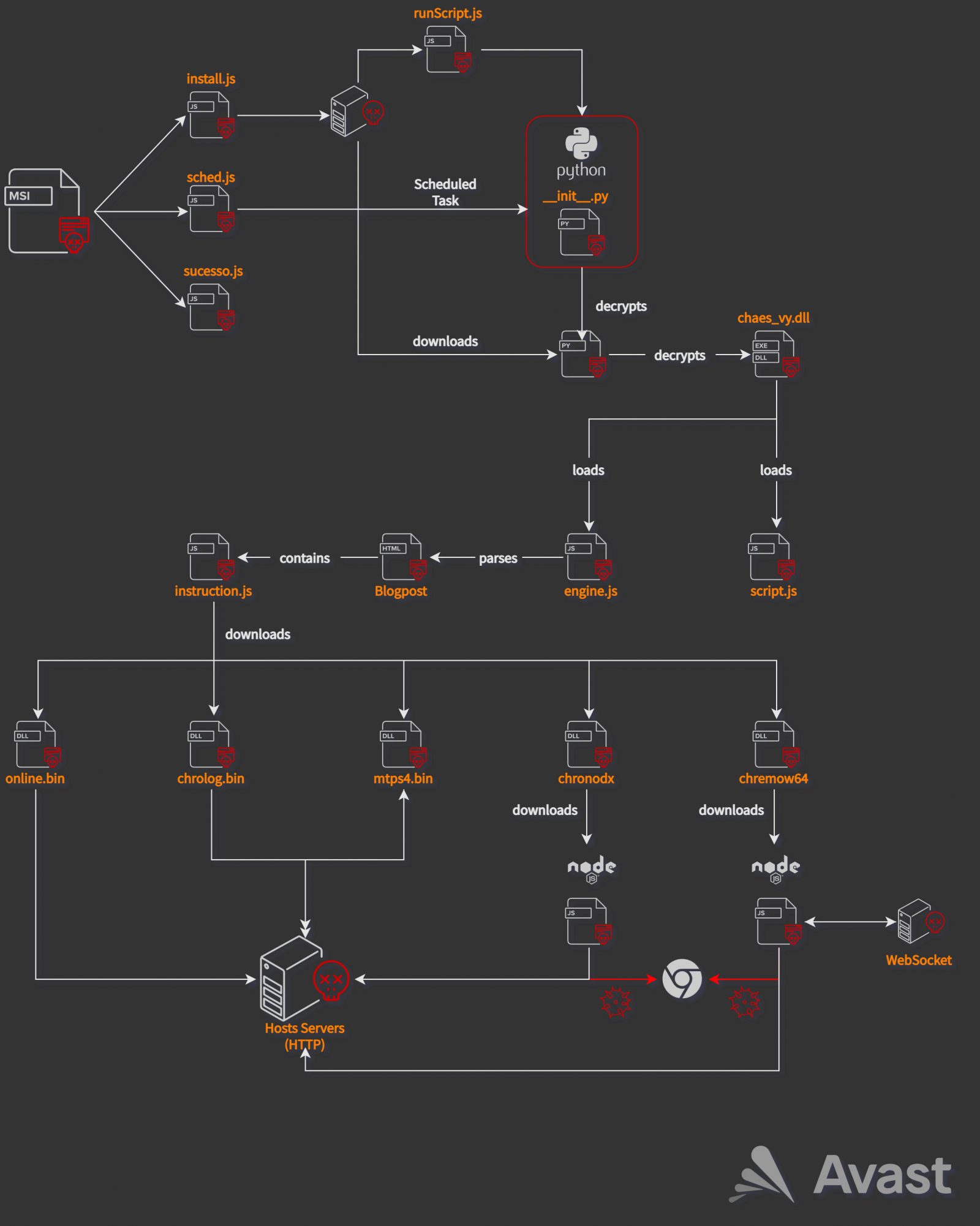
The Python loader chain unfolds in memory and involves loading multiple scripts, shellcode, and Delphi DLLs until everything is in place for executing the final payload within a Python process.
Also Read: Trusted Data Sharing Framework IMDA Announced In Singapore
The final stage is undertaken by instructions.js, which fetches the Chrome extensions and installs them on the victim’s system. Finally, all extensions are launched with the proper arguments.
Avast says they have seen five different malicious Chrome browser extensions installed on victim’s devices, including:
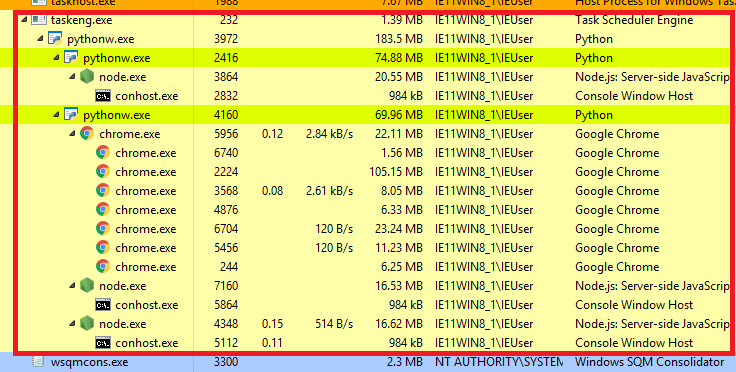
At this time, the Chaes campaign is still ongoing, and those who have been compromised will remain at risk even if the websites are cleaned.
Avast claims that some of the compromised websites abused for dropping the payloads are very popular in Brazil, so the number of infected systems is likely large.