KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







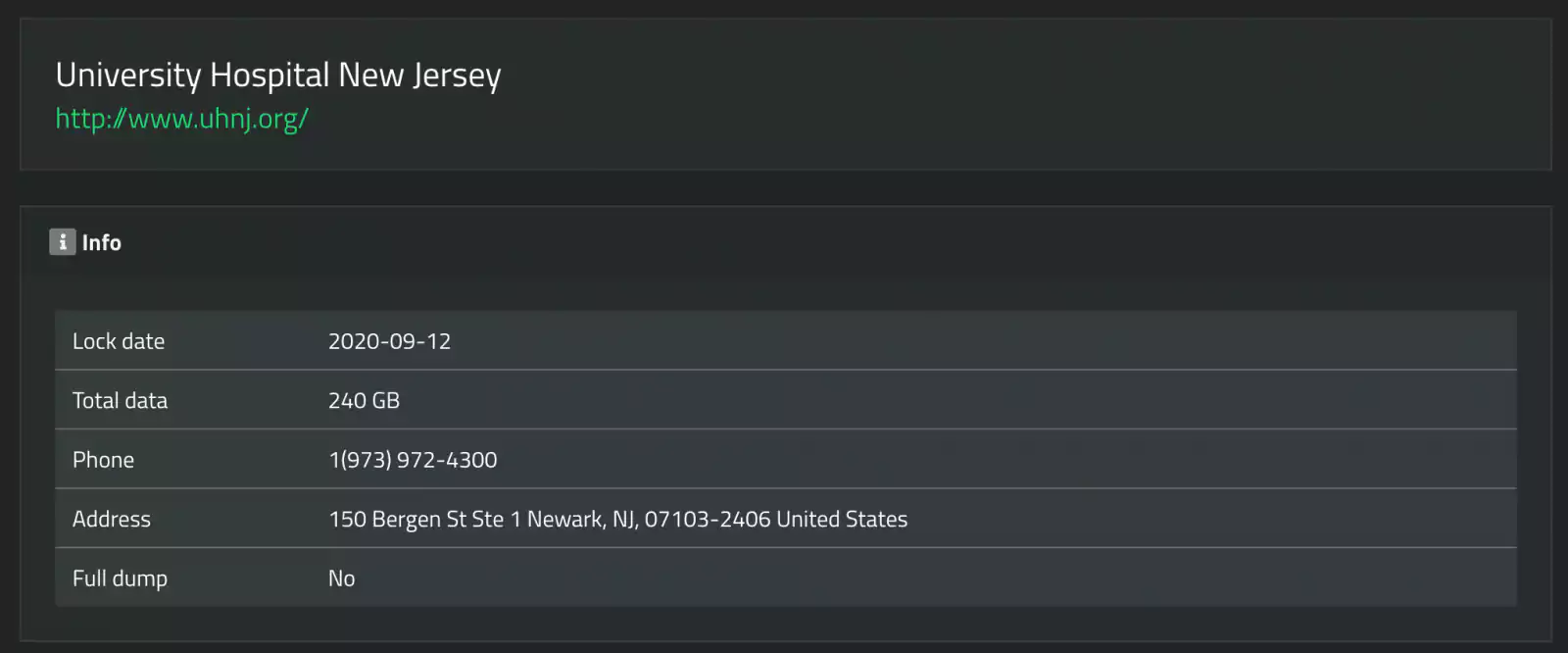
University Hospital New Jersey (UHNJ) has suffered a massive 48,000 document data breach after a ransomware operation leaked their stolen data.
Established in 1994, the University Hospital is a New Jersey state-owned teaching hospital that provides medical care to residents.
The hospital runs on a $626 million budget and has over 3,500 employees, 519 licensed beds, and over 172,000 annual outpatient visits.
The SunCrypt ransomware operation has leaked data allegedly stolen from UHNJ in a September ransomware attack.
SunCrypt is a ransomware operation that began its activities in October 2019 but was not very active. Over the past few months, they have become much more active since releasing a dedicated leak site.
While BleepingComputer has not corroborated all of the attacker’s claims, the data seen by BleepingComputer does appear to belong to UHNJ.
Of the 240 GB of data allegedly stolen from University Hospital New Jersey, the attackers have leaked a 1.7 GB archive containing over 48,000 documents.
Also Read: 7 Client Data Protection Tips to Keep Customers Safe
This data leak includes patient information release authorization forms, copies of driving licenses, Social Security Numbers (SSNs), date of birth (DOB), and records about the Board of Directors.
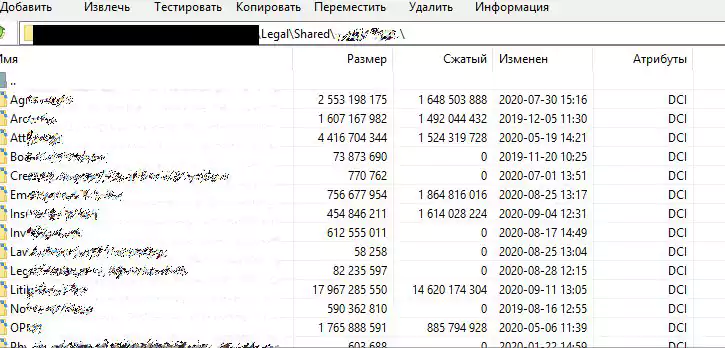
Shown below is a partial image of one such record leaked in the dump, with PII redacted:

When a computer is infected with TrickBot, it usually leads to a full compromise of the network with ransomware eventually being deployed.
TrickBot has historically been known to lead to Ryuk ransomware attacks and an occasional Maze ransomware attack. Now TrickBot is predominately pushing the Conti ransomware.
While Maze denies any affiliation with SunCrypt, the SunCrypt ransomware operators have told BleepingComputer that they are part of the Maze Cartel.
Furthermore, when infecting a victim, SunCrypt will connect to an IP address previously associated with Maze infections.
The SunCrypt operators may have also partnered with TrickBot to provide access to compromised networks, such as the network of UHNJ.
Also Read: 12 Damaging Consequences of Data Breach