KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A recently discovered malware framework known as MATA and linked to the North Korean-backed hacking group known as Lazarus was used in attacks targeting corporate entities from multiple countries since April 2018 for ransomware deployment and data theft.
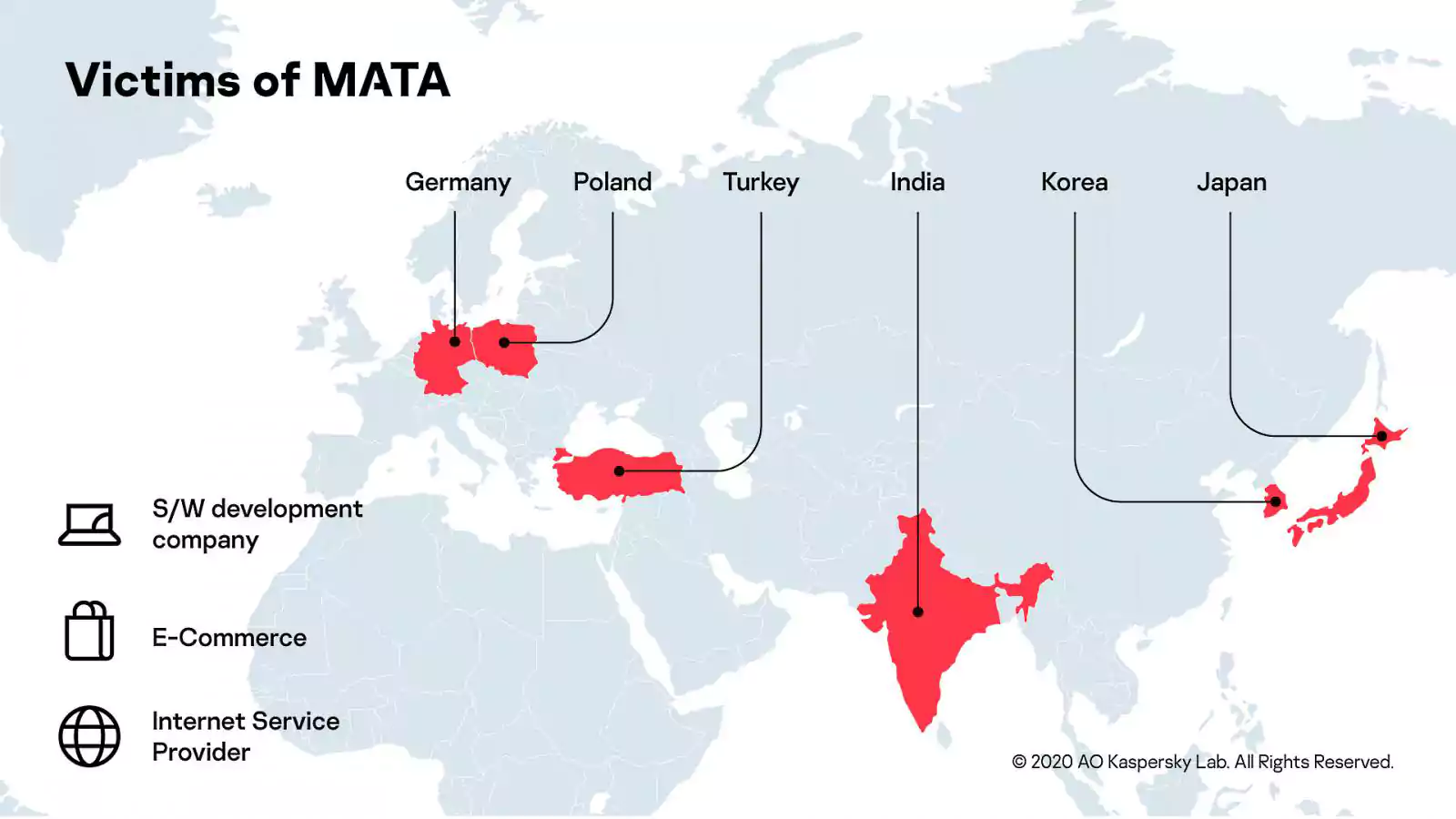
Among the targeted countries, security researchers with Kaspersky Lab’s Global Research and Analysis Team (GReAT) who spotted MATA mentioned Poland, Germany, Turkey, Korea, Japan, and India.
Lazarus (also tracked as HIDDEN COBRA by the United States Intelligence Community and Zinc by Microsoft) used MATA to compromise and infect machines of companies with activities in various industries, including but not limited to a software development company, an internet service provider, and an e-commerce company.
While Kaspersky’s report doesn’t mention the attackers’ motivation, the North Korean hackers are well-known for being financially motivated as shown by their campaigns — they hacked Sony Films in 2014 as part of Operation Blockbuster and were behind the 2017 global WannaCry ransomware epidemic.
Since they were first spotted in 2007, Lazarus launched attacks against financial organizations from India, Mexico, Pakistan, Philippines, South Korea, Taiwan, Turkey, Chile, and Vietnam, as well as on BitCoin exchanges and targets in the aerospace, engineering, government, media, and technology industry sectors.
Also read: 4 easy guides to data breach assessment
MATA is a modular framework with several components including a loader, orchestrator, and multiple plugins, and it can be used to infect Windows, Linux, and macOS systems.
During their attacks, the hackers can use MATA to load several plugins into the infected system’s memory running commands, manipulating files and processes, injecting DLLs, creating HTTP proxies and tunnels on Windows devices.
MATA plugins also allow the hackers to scan for new targets on macOS and Linux-based machines (routers, firewalls, or IoT devices). On the macOS platform, MATA can also load a plugin_socks module that can be used to configure proxy servers.
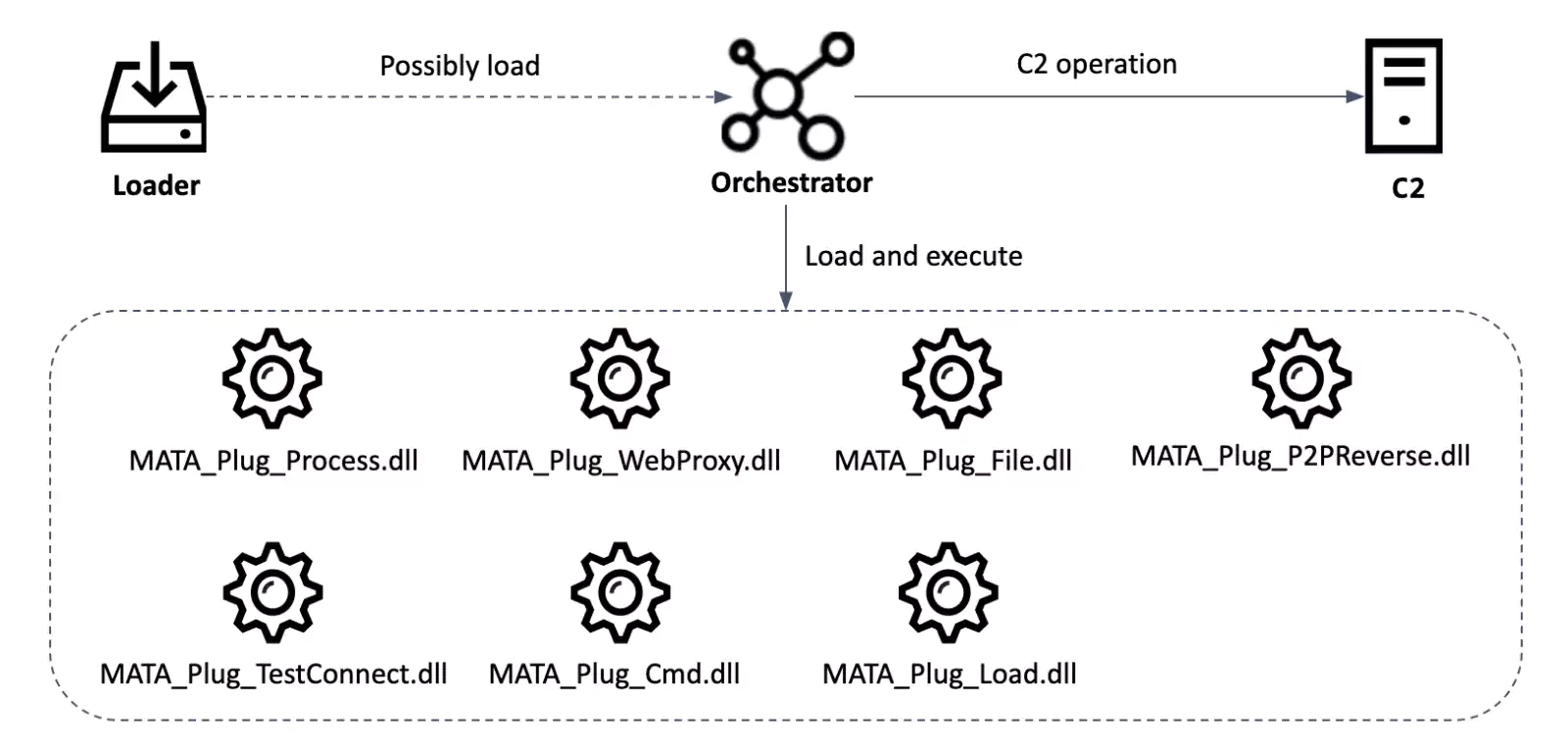
While analyzing their telemetry, Kaspersky’s researchers discovered that the hackers are using a malware loader to load an encrypted next-stage payload (which might be the framework’s orchestrator).
“We’re not sure that the loaded payload is the orchestrator malware, but almost all victims have the loader and orchestrator on the same machine,” the report explains.
Once the MATA malware framework is fully deployed, the operators try to find databases with sensitive customer or business information and will run database queries to collect and exfiltrate customer lists.
While the researchers had no conclusive indications that Lazarus was indeed able to steal the data they collected during attacks, exfiltrating such databases from their victims is certainly one of their goals, together with the VHD ransomware as seen in the case of one of the companies they compromised.
Qihoo 360 Netlab researchers also published an analysis of the Windows and Linux components of the MATA malware framework (which they named Dacls) in December 2019.
The MATA framework was linked to the Lazarus APT group by Kaspersky based on unique orchestrator filenames that were used in versions of the Manuscrypt trojan (also known as Volgmer).
Samples of Manuscrypt were publicly shared by the Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI) in 2017 via a US-CERT Malware Analysis Report.
Kaspersky’s report also mentions similar global configuration data that MATA shares with Lazarus’ Manuscrypt trojan, including “a randomly generated session ID, date-based version information, a sleep interval, and multiple C2s and C2 server addresses.”
“The MATA framework is significant in that it is able to target multiple platforms: Windows, Linux, and macOS,” Kaspersky concludes.
“In addition, the actor behind this advanced malware framework utilized it for a type of cybercrime attack that steals customer databases and distributes ransomware.”
Also read: Privacy policy template important tips for your business