KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







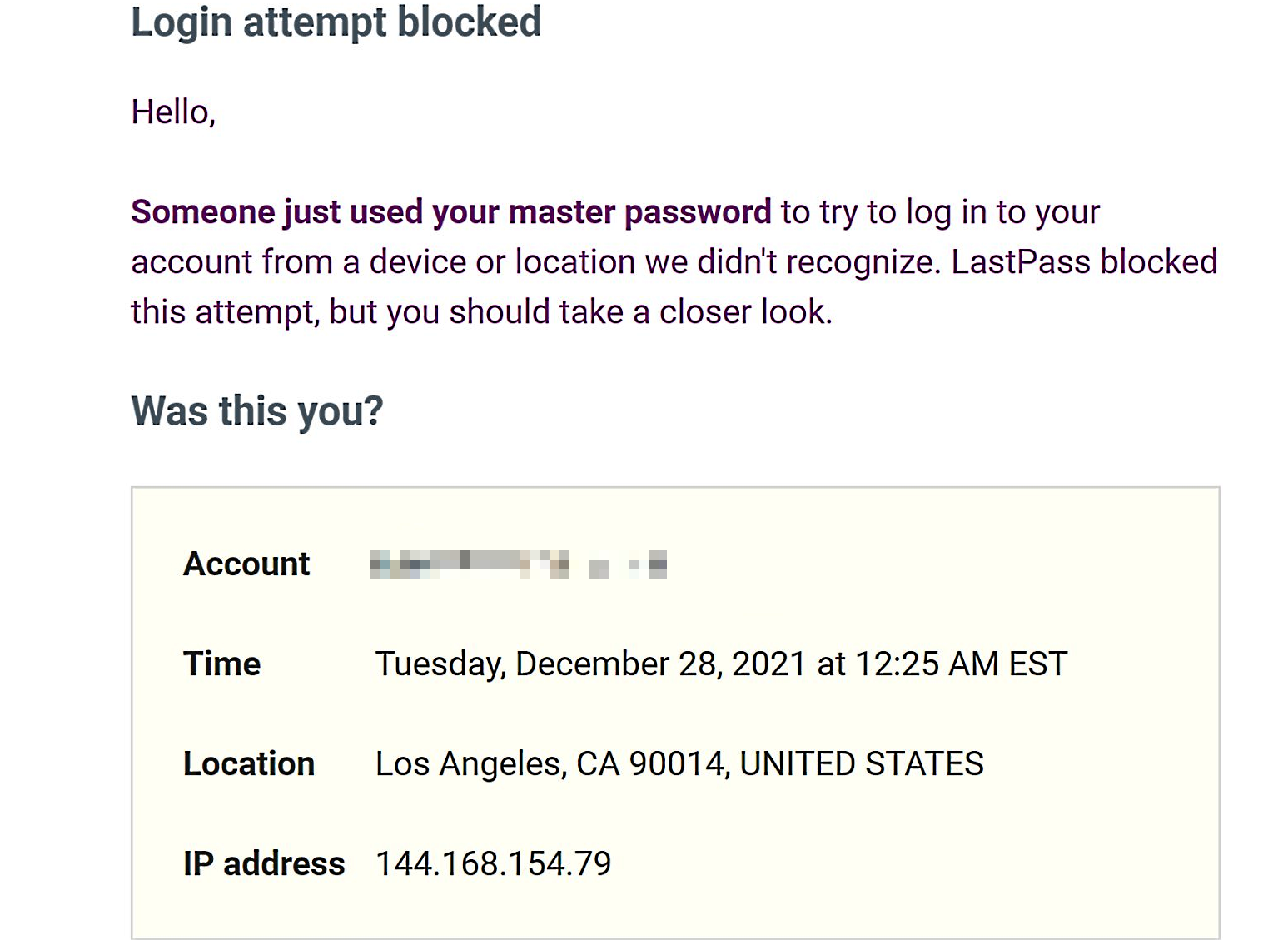
Many LastPass users report that their master passwords have been compromised after receiving email warnings that someone tried to use them to log into their accounts from unknown locations.
The email notifications also mention that the login attempts have been blocked because they were made from unfamiliar locations worldwide.
“Someone just used your master password to try to log in to your account from a device or location we didn’t recognize,” the login alerts warn.
“LastPass blocked this attempt, but you should take a closer look. Was this you?”
Also Read: The DNC Registry Singapore: 5 Things You Must Know
Reports of compromised LastPass master passwords are streaming in via multiple social media sites and online platforms, including Twitter, Reddit, and Hacker News (original report from Greg Sadetsky).
LogMeIn Global PR/AR Senior Director Nikolett Bacso-Albaum told BleepingComputer that “LastPass investigated recent reports of blocked login attempts and determined the activity is related to fairly common bot-related activity, in which a malicious or bad actor attempts to access user accounts (in this case, LastPass) using email addresses and passwords obtained from third-party breaches related to other unaffiliated services.”
“It’s important to note that we do not have any indication that accounts were successfully accessed or that the LastPass service was otherwise compromised by an unauthorized party. We regularly monitor for this type of activity and will continue to take steps designed to ensure that LastPass, its users, and their data remain protected and secure,” Bacso-Albaum added.
However, users receiving these warnings have stated that their passwords are unique to LastPass and not used elsewhere. BleepingComputer has asked LastPass about these concerns but has not received a reply as of yet.
While LastPass didn’t share any details regarding how the threat actors behind these credential stuffing attempts, security researchers Bob Diachenko said he recently found thousands of LastPass credentials while going through Redline Stealer malware logs.
Also Read: How To Comply With PDPA: A Checklist For Businesses
BleepingComputer was also told by LastPass customers who received such login alerts that their emails were not in the list of login pairs harvested by RedLine Stealer found by Diachenko.
This means that, at least in the case of some of these reports, the threat actors behind the takeover attempts used some other means to steal their targets’ master passwords.
Some customers have also reported changing their master passwords since they received the login warning, only to receive another alert after the password was changed.
To make things even worse, customers who tried disabling and deleting their LastPass accounts after receiving these warnings also report [1, 2] receiving “Something went wrong: A” errors after clicking the “Delete” button.
Two years ago, in September 2019, LastPass fixed a security vulnerability in the password manager’s Chrome extension that could have allowed threat actors to steal the credentials last used for logging into a site.
LastPass users are advised to enable multifactor authentication to protect their accounts even if their master password was compromised.
Update December 28, 12:36 EST: Added LastPass statement.
Update December 28, 15:08 EST: Added info on LastPass login pairs stolen by RedLine Stealer malware.