KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Low-skilled hackers likely from Iran have joined the ransomware business targeting companies in Russia, India, China, and Japan. They are going after easy hits, using publicly available tools in their activity.
The new group is deploying Dharma ransomware. Based on forensic artifacts, this is a non-sophisticated, financially-motivated gang that is new to cybercrime.
The threat actor is not greedy. Their demand is between 1-5 Bitcoin (currently $11,700 – $59,000), which is on the lower range of ransom demand compared to other ransomware operations.
They find victims by scanning IP address ranges on the internet for exposed remote desktop connections (RDP); their tool of choice for this stage is Masscan, an open-source port scanner.
Next, they launch a brute-force with NLBrute, a utility that tries a list of RDP passwords in an attempt to find a combo that works. Once in, they sometimes try to elevate privileges by exploiting an old vulnerability (CVE-2017-0213) in Windows 7 through 10.
Researchers at cybersecurity company Group-IB learned about this new group in June during an incident response engagement at a company in Russia. Based on forensic artifacts, they determined the attacker to be “Persian-speaking newbie hackers.”
Supporting this conclusion are clues from the next steps of the attack, which seem to lack the confidence of an actor that knows what to do once after breaching a network.
“Interestingly, the threat actors likely didn’t have a clear plan on what to do with the compromised networks. Once they established the RDP connection, they decide on which tools to deploy to move laterally,” Group-IB
“For instance, to disable built-in antivirus software, the attackers used Defender Control and Your Uninstaller,” the researchers explain.
Also read: 6 Ways to Protect Your Business From Employee Data Theft
Further evidence that the operation is the work of a script kiddie from Iran comes from search queries in Persian to find other tools necessary for the attack and from the Persian-language Telegram channels providing them.
Group-IB has compiled the following set of tactics, techniques, and procedures observed with this particular threat actor:
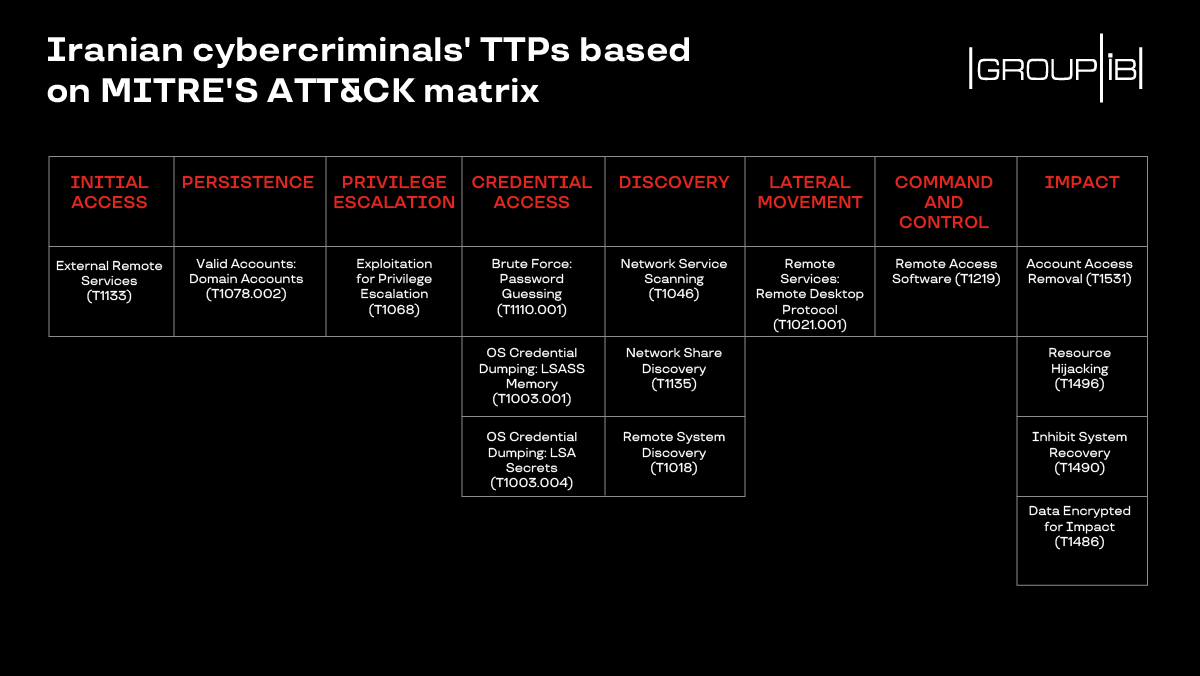
The number of victims compromised by this threat actor remains unknown, just like the path that led the threat actor to Dharma ransomware-as-a-service (RaaS) operation.
However, given that Dharma operators provide a toolkit that makes it easy for anyone to become a cybercriminal, it should not come as a surprise that inexperienced individuals are deploying this file-encrypting malware.
Oleg Skulkin, senior DFIR analyst at Group-IB, says that Dharma ransomware source code being leaked in March also explains the wider use of this malware strain.
What’s surprising, though, is the use of the malware for financial gain by an Iranian threat group. Historically, cyber activity hailing from this region has been related to state-backed espionage and sabotage operations.
“It’s surprising that Dharma landed in the hands of Iranian script kiddies who used it for financial gain, as Iran has traditionally been a land of state-sponsored attackers engaged in espionage and sabotage” – Oleg Skulkin
Also read: Top 5 Impact of Data Loss on Business