KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Hackers are always evolving their tactics to stay one step ahead of security companies. A perfect example of this is the hiding of malicious credit card stealing scripts in the EXIF data of a favicon image to evade detection.
A common attack used to steal credit cards is to hack the website and inject malicious JavaScript scripts that steal submitted payment information when a customer makes a purchase.
These stolen credit cards are then sent back to a server under the control of the threat actors where they are collected and used for fraudulent purchases or to sell on dark web criminal markets.
These types of attacks are called Magecart and have been used on websites for well-known companies such as Claire’s, Tupperware, Smith & Wesson, Macy’s, and British Airways.
Also read: 7 Client Data Protection Tips to Keep Customers Safe
In a new report by Malwarebytes, an online store using the WordPress WooCommerce plugin was found to be infected with a Magecart script to steal customer’s credit cards.
What made this attack stand out was that the scripts used to capture data from payment forms were not added directly to the site but were contained in the EXIF data for a remote site’s favicon image.
“The abuse of image headers to hide malicious code is not new, but this is the first time we witnessed it with a credit card skimmer,” Malwarebytes’ Jérôme Segura stated in the report.
When images are created, the developer can embed information such as the artist who created it, information about the camera, copyright info, and even the location of the picture.
This information is called the Exchangeable Image File Format (EXIF) data.
In this attack, the threat actors hacked a website and added what appears to be a simple script that inserts a remote favicon image and does some processing.
After further investigation, Malwarebytes discovered that this favicon, while appearing harmless, actually contained malicious JavaScript scripts embedded in its EXIF data, as shown in the image below.
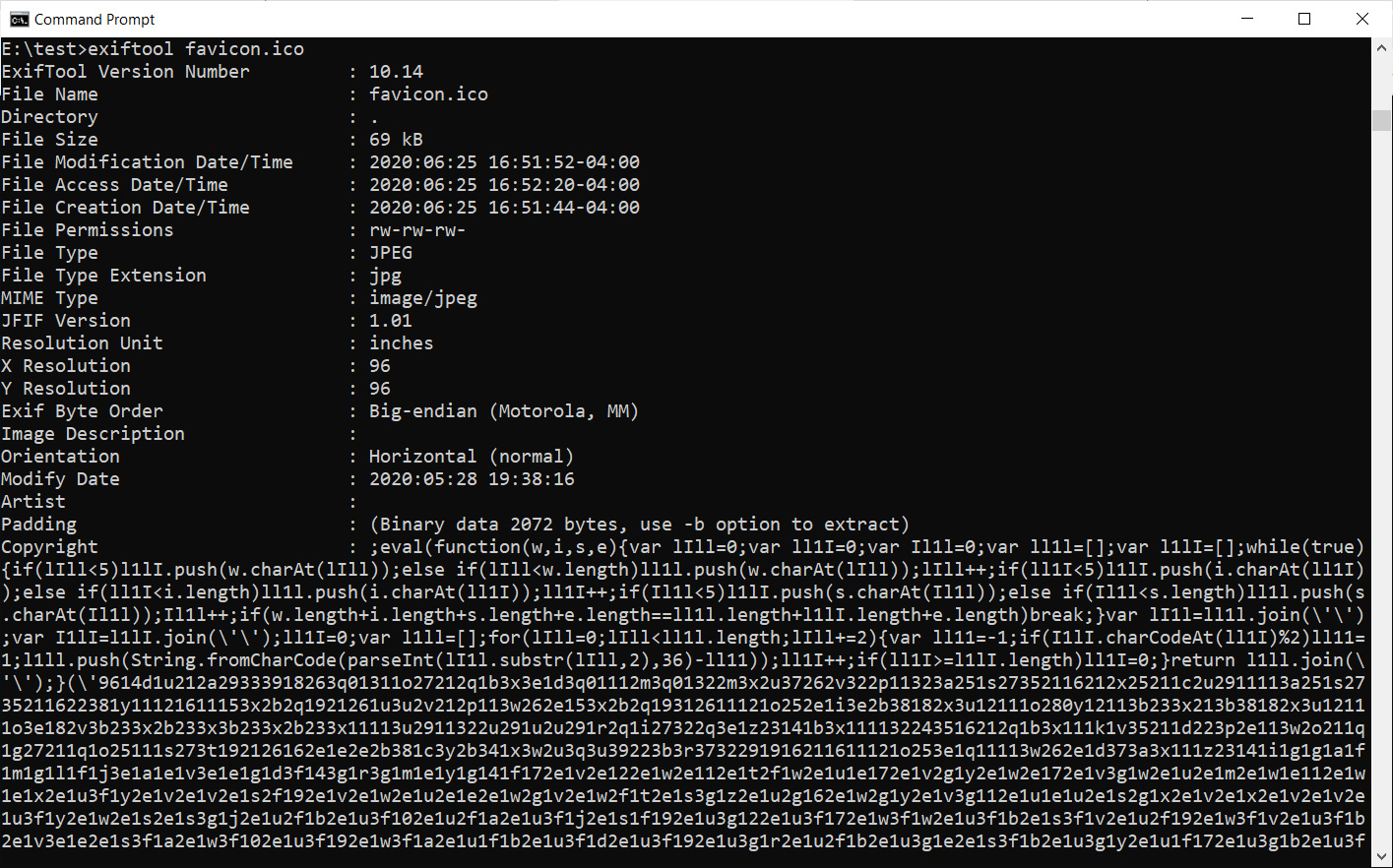
Once the favicon image was loaded into the page, the scripts added to the site by the hackers would load the image’s embedded malicious skimmer scripts.
Once these scripts were loaded, any credit card information submitted on checkout pages was sent back to the attackers where they could be collected at their leisure.
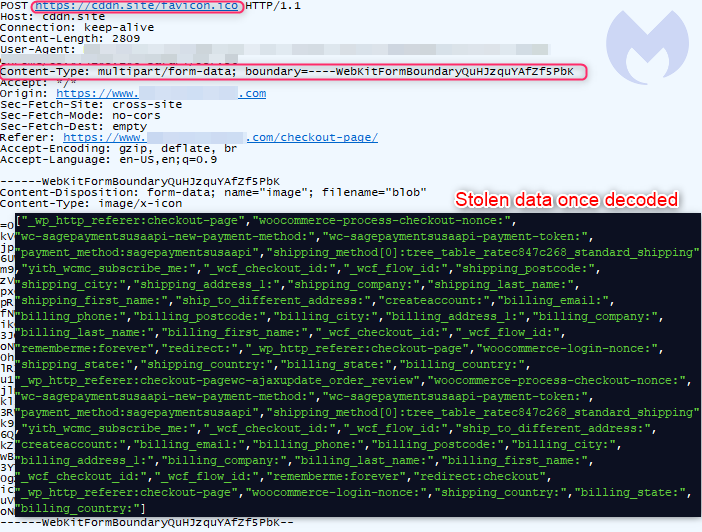
As these malicious card stealing scripts are not contained on the hacked site itself, it is more difficult for security software or even web developers to notice that something may be wrong.
Malwarebytes was able to find the kit that was used to create and perform this magecart attack. After further analysis, it was determined that this attack might be linked to a threat actor group known as ‘Magecart 9’.
This group has been linked to other clever techniques in the past, such as the use of web sockets to evade detection.
Also read: Privacy policy template important tips for your business