KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







An advanced hackers-for-hire group has compromised computers of an architecture firm involved in luxury real-estate projects worth billions of US dollars.
The group carries out espionage operations, the attack vector being a malicious plugin for the Autodesk 3ds Max software for creating professional 3D computer graphics.
According to an investigation from Bitdefender, the unnamed victim is an important company working with luxury real-estate developers in the U.S., the U.K., Australia, and Oman that contract services of top architects and interior designers.
For this operation, the threat actor relied on command and control (C2) infrastructure in South Korea, which recorded traffic from malware samples in multiple countries (U.S., South Korea, Japan, South Africa), suggesting select victims in these regions as well.
Evidence discovered by security researchers points to a group that provides sophisticated hacking services to various customers looking for inside financial details and negotiations about high-value contracts.
“The sophistication of the attack reveals an APT-style group that had prior knowledge of the company’s security systems and used software applications, carefully planning their attack to infiltrate the company and exfiltrate data undetected” – Bitdefender
Also read: 5 Simple Instructions on How to Access Request Form PDF
In this case, the attack vector was a vulnerability affecting several Autodesk 3ds Max versions that allows code execution on a windows system.
Earlier this month, Autodesk warned that an exploit for the MAXScript scripting utility exists in the form of a malicious plugin called “PhysXPluginMfx.” When loaded in 3ds Max, the plugin can infect other MAX files, thus spreading to other users on the network.
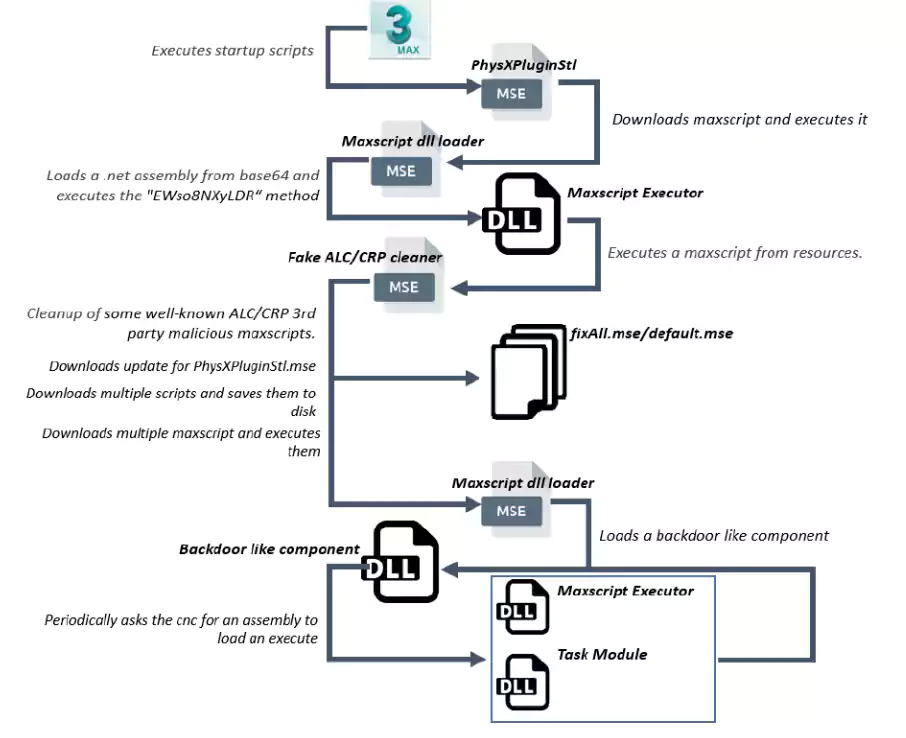
Unlike cybercriminal groups that seek immediate financial gains, this threat actor uses malware that collects details about the compromised host (computer name, username) and steals sensitive information.
Apart from using tools that take screenshots and extract passwords and history data from Google Chrome, the actor also has malware that steals files with specific extensions.
Bitdefender researchers assess that the attacker compiles this file-stealing component for each victim to include the list of files they want to pilfer.
To remain under the radar on a compromised machine, the actor turned to an interesting trick that made the malicious binary sit dormant if Task Manager or Performance Monitor were running.
Depending on how much window area was visible for these two applications, a flag was set to instruct the malware to sleep, thus reducing CPU usage and placing it lower in the list of power-hungry processes.
On the same note, file compression was employed only to some files. Data that would attract unnecessary attention if archived, would be skipped from this operation
Bitdefender’s report today says that telemetry data shows that similar malware samples contacted the same C2 in South Korea less than a month ago.
While this may help connect the dots with other operations, it is by no means the beginning of the group’s activity timeline.
Also read: What is Pseudonymisation: 5 Techniques and Its Best Practices