KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The number of offers for network access and their median prices on the public posts on hacker forums dropped in the final quarter of last year but the statistics fail to reflect the real size of the initial access market.
Data from threat intelligence firm Kela indicates that many of the deals actually closed behind closed doors, a trend shaped over the past months.
According to the company, over 240 offers to sell initial network access occurred in public conversations on three underground forums. A quarter of these came with no price tag, a clear indication of transactions being done in private conversations.
However, this number does not include an offer for access to more than 500 .gov and .edu networks (auctioned for 25 bitcoins) and another one for access to a Chinese electronics maker (asked 150 bitcoins). Neither of them appeared to have been closed due to the insanely high prices.
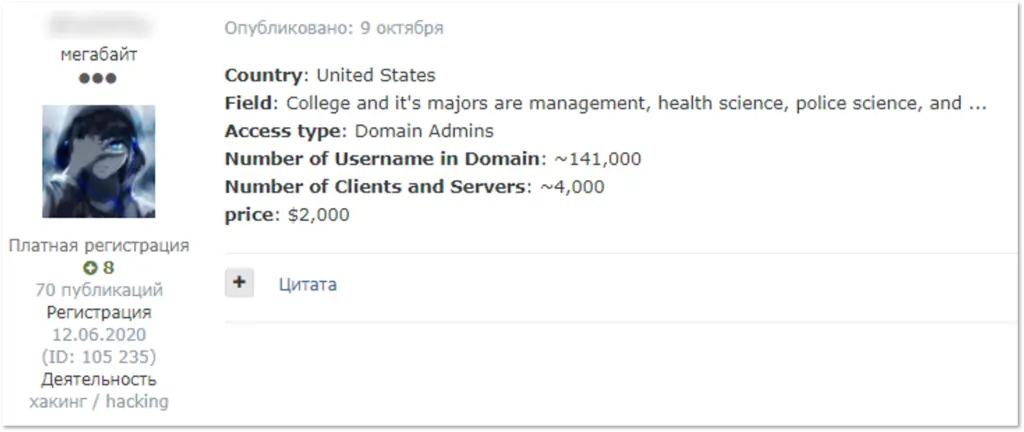
For $1,500-$2,000, a buyer could get domain admin to a medium-sized company with a few hundred employees. However, the average price in Q4 was $6,684, an increase from the $4,960 that Kela saw in September 2020.
The cumulative sum for all the offers that Kela observed during the period was $1,209,880. Of this, peddlers reported in open conversations closing deals worth just $133,900, which represents only 14% of the entire network offer seen by the company.
Also Read: What Do 4 Messaging Apps Get From You? Read The iOS Privacy App Labels
Compared to previous data collected in September, this is 23% lower. This does not paint an accurate picture of the scale of trading initial network access, though. As Kela mentions, getting a true sense of how large this market is “depends only on brokers and their will to specify sold accesses or not.”
Month over month, Q4 2020 saw around 80 network accesses while in the previous period the number was higher at 108, accounting for a 25% gap that was likely caused by brokers moving the talks with middlemen or buyers to private channels to avoid the eyes of researchers.
“This hypothesis is based on the fact that many initial access brokers commonly write to contact them privately in order to receive information about other accesses that they’re willing to sell. While such behavior always existed, there is a more recent trend that emerged these past couple of months – brokers often offer a bunch of accesses in one thread and request from potential buyers to contact them privately to get the whole list” – Kela
Alternatively, as is the case in the ransomware business, some initial access peddlers announce the type of access they had to attract partners and become affiliates working for a percentage.
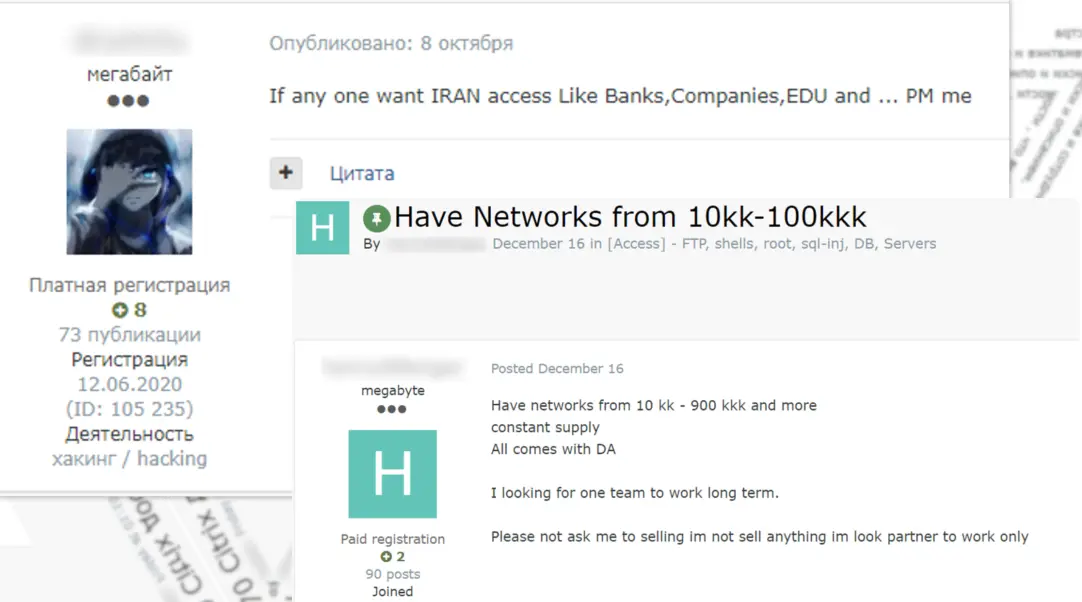
Offers like the one above are not rare. In another one, a broker said they had had “70 Citrix accesses from Tier 1 countries,” to suggest profitable targets.
While both new and old initial access brokers posted their offers in Q4 2020, Kela says that some prominent actors switched to private dealings, and announced a valuable, expensive offer only occasionally.
One of these actors that were very active over the summer, listed only two offers in October and December: $35,000 for access to a government entity and $20,000 for a school district in the U.S.
This behavior is common with brokers that found regular buyers that passed on some offers. Therefore, they turned to the public side of the forum to close the deal.
As for the access provided, at the top of the list are remote desktop (RDP), VPN-based, remote code execution exploits, and Citrix products. These make more than 45% of all types.
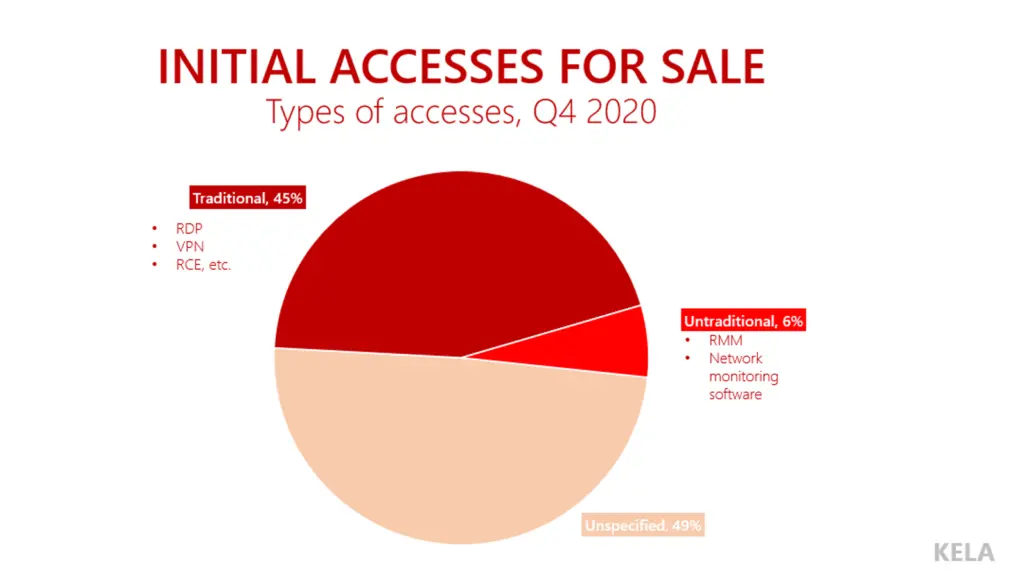
Among the less common access types, Kela threat intelligence analyst Victoria Kivilevich found DX NetOps and DX Spectrum network monitoring and fault management software belonging to a company that operated an airport.
Also Read: Key PDPA Amendments 2019/2020 You Should Know
Since it can manage the entire IT infrastructure, it could be used for lateral movement to compromise the entire network. Access through this software was sold within four days.
The most expensive accesses (going to over $100,000) that Kela saw in Q4 2020 referred to both public and private entities in the U.S., Australia, Mexico, India, and Europe.
Victims included IT companies – most likely managed services providers that enabled access to their clients, telecommunications companies, ISPs, government entities, and a large oil and gas company.
Some of the victims were compromised some time after the initial access offer, as is the case of Mexico’s National Insurance and Surety Commission, advertised on two forums for at least $70,000. In early December, LockBit ransomware encrypted their computers.
Network access peddlers continue to fuel cyberattacks of all sorts, with ransomware being at the top of the list. Among the most active of them are: