KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







US bank and mortgage lender Flagstar has disclosed a data breach after the Clop ransomware gang hacked their Accellion file transfer server in January.
In December, threat actors affiliated with the Clop ransomware gang began exploiting vulnerabilities in Accellion FTA servers used by organizations to share sensitive files with people outside of their organization.
On Friday, Flagstar Bank issued a security disclosure on their website and began emailing customers about a breach of their Accellion FTA server.
“Accellion, a vendor that Flagstar uses for its file sharing platform, informed Flagstar on January 22, 2021, that the platform had a vulnerability that was exploited by an unauthorized party. After Accellion informed us of the incident, Flagstar permanently discontinued use of this file sharing platform.
“Unfortunately, we have learned that the unauthorized party was able to access some of Flagstar’s information on the Accellion platform and that we are one of numerous Accellion clients who were impacted,” Accellion warned in the security advisory.
When we contacted Flagstar Bank on Friday with questions about the data breach, the bank directed us to their already published advisory.
However, BleepingComputer has learned that Flagstar was breached not by the original December zero-day vulnerability, which they had patched, but for a new vulnerability utilized by threat actors in January.
Also Read: The 5 Benefits Of Outsourcing Data Protection Officer Service
After threat actors stole their data, BleepingComputer was told Flagstar received a ransom note demanding a bitcoin payment or the data would be released. Below is an example of a ransom note received by Accellion victims.
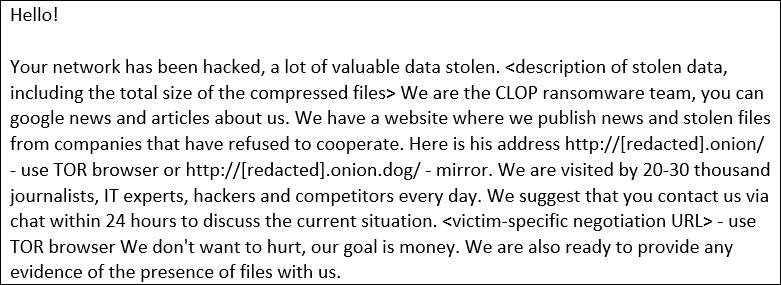
Ransom demands associated with Accellion attacks have ranged as high as $10 million in bitcoin.
Flagstar utilized their Accellion FTA server to send and receive sensitive documents with their partners and customers.
Today, after Flagstar began notifying victims of the data breach, the Clop ransomware gang released screenshots of stolen data with a warning that it had stolen a lot more personal data.
The shared screenshots illustrate the types of sensitive customer and employee information stolen, including social security numbers, names, addresses, phone numbers, and tax records.
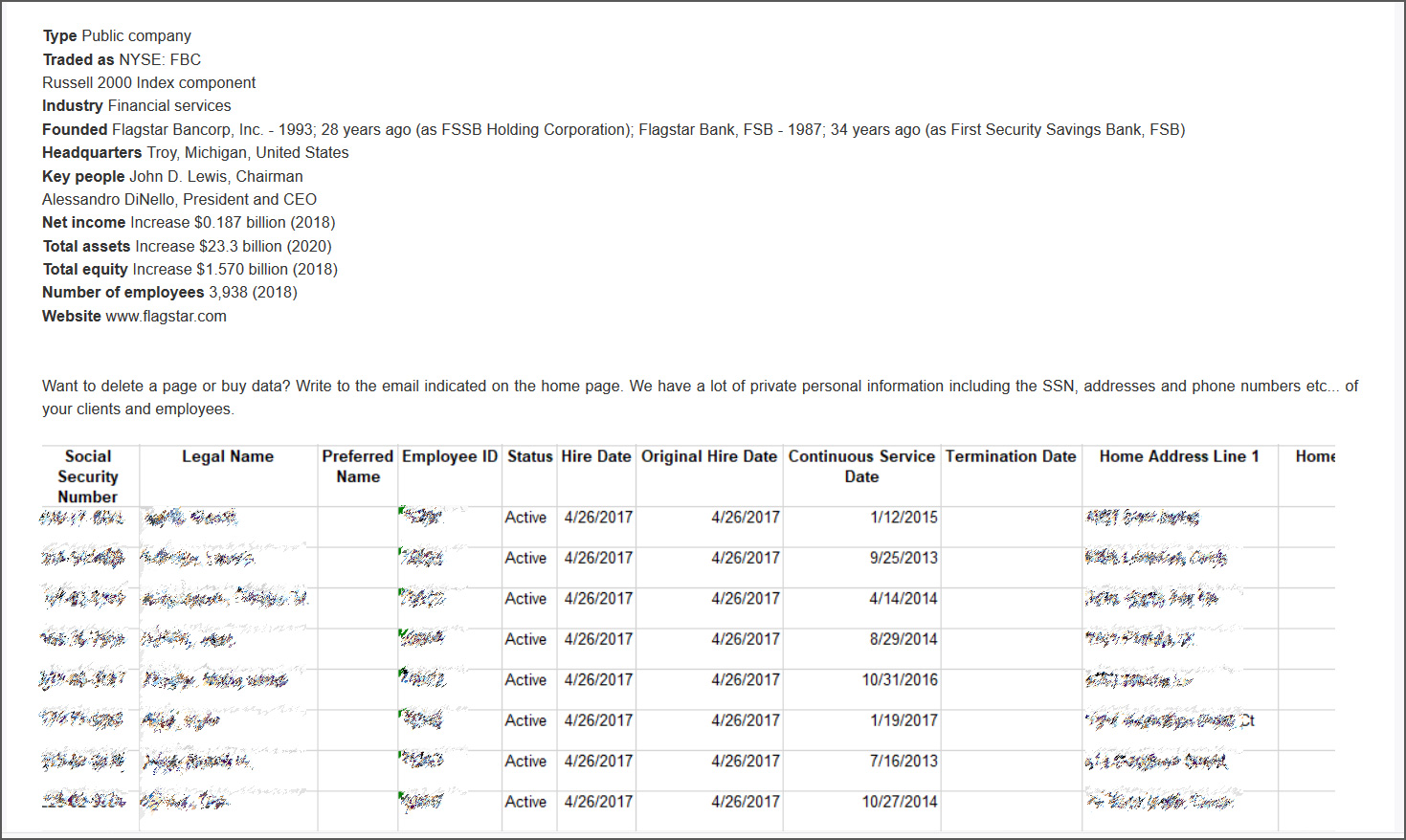
While the ransomware gang has only shared a few screenshots of stolen data, as Flagstar is a bank and mortgage lender, it should be assumed that the threat actors stole further documents containing sensitive information.
Based on the numerous Accellion data leaks published by the Clop gang, it is clear that they are behind all of these attacks and will continue to publish stolen data as victim’s disclose their attacks.
Unfortunately, this means we will likely see further data breaches associated with Accellion FTA hacks soon.
Also Read: How To Prevent WhatsApp Hack: 7 Best Practices
Other victims associated with Accellion FTA attacks are Singtel, Bombardier, QIMR Berghofer, Washington’s State Auditor office, New Zealand Reserve Bank, NSW for Transport, Fugro, Jones Day, Danaher, and the ABS Group.