KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







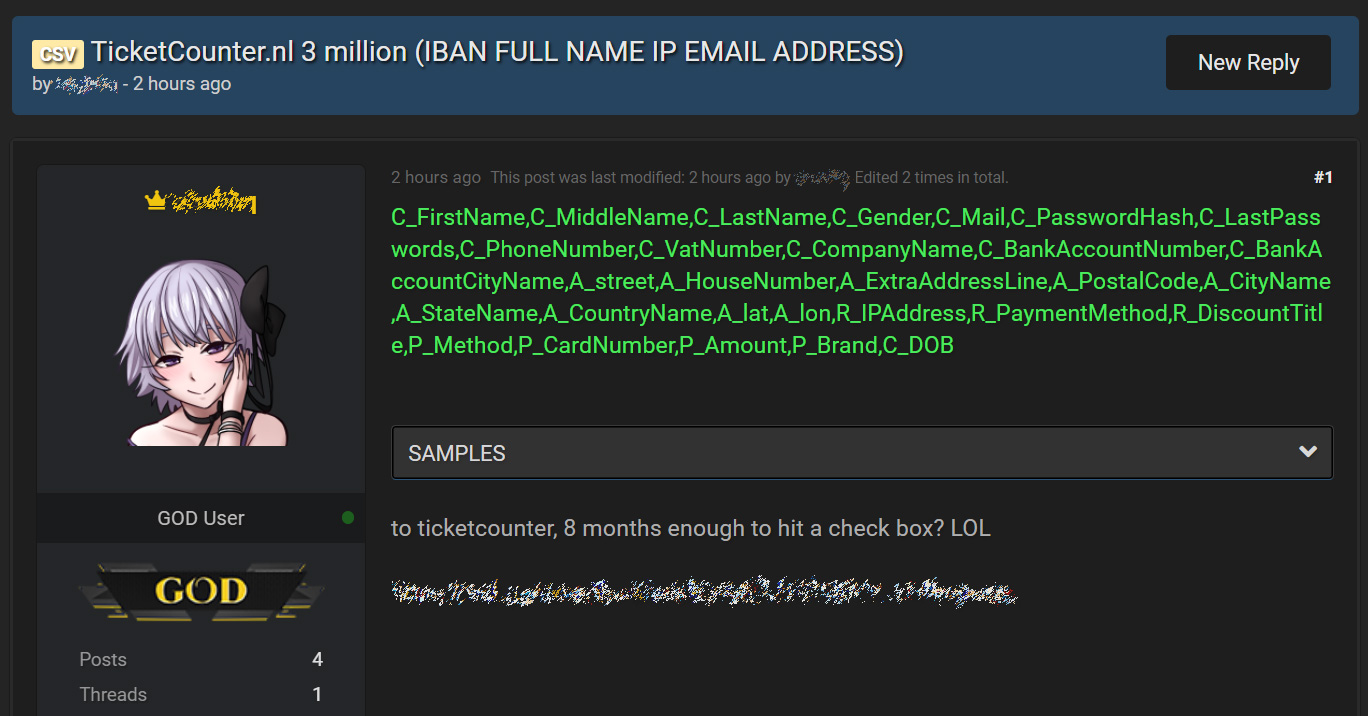
A Dutch e-Ticketing platform has suffered a data breach after a user database containing 1.9 million unique email addresses was stolen from an unsecured staging server.
Ticketcounter is a Dutch e-Ticketing platform that allows clients, such as zoos, parks, museums, and events, to provide online tickets to their venue.
On February 21st, a threat actor created a topic on a hacker forum to sell the stolen Ticketcounter database but quickly took the post down.
It was believed at first to be removed out of concern for the watchful eyes of the Netherlands Police. However, the threat actor told BleepingComputer that they have no fear of law enforcement, and they removed it as the database was sold privately.
From the samples of the database seen by BleepingComputer, the data exposed can include full names, email addresses, phone numbers, IP addresses, and hashed passwords.
Also Read: 15 Best Tools For Your Windows 10 Privacy Settings Setup
Ticketcounter has confirmed the data breach to both BleepingComputer and Troy Hunt of Have I Been Pwned, who spoke to the company’s owner after receiving the database.
In what should be a model of transparency, Ticketcounter CEO Sjoerd Bakker has told BleepingComputer that they copied a database to a Microsoft Azure server to test an ‘anonymization process’ that replaces personal data with fake data.
Unfortunately, after copying the database, it was not secured properly, and the threat actor was able to download it.
Bakker stated that shortly after the threat actor was selling the database, the hacker also contacted Ticketcounter and demanded seven bitcoins, or approximately $337,000, not to leak the data. The threat actor warned that if Ticketcounter did not make a payment, they would contact all of Ticketcounter’s partners to alert them of the breach.
Ticketcounter was one step ahead and had already contacted all of their clients and shared what information has been stolen. As the actual ticket buyers are Ticketcounter’s clients’ customers, the individual venues have been advised to perform their own data breach notifications to those affected.
Bakker told BleepingComputer that Ticketcounter is creating various resources for his clients to facilitate these data breach notifications. These include lookup widgets, FAQs, and email templates that clients can share with customers to learn about the breach.
After not receiving a payment, the threat actor released the database for free today on a hacker forum.
The stolen database has been provided to Have I Been Pwned’s Troy Hunt by the threat actor and added to the data breach lookup service.
For those who are concerned they may have been affected, you can submit your email to Have I Been Pwned to see if it was included in the leaked data.
Also Read: How Formidable is Singapore Cybersecurity Masterplan 2020?
If Have I Been Pwned states that you were affected by this data breach, it becomes a bit difficult to determine which specific venue/site you have an account.
As those affected are not customers of Ticketcounter directly, most users will have to wait until the particular venue discloses the data breach.
While you wait, we recommend changing your passwords at sites where you use the same password.
When changing your passwords, you should use a unique password so that a breach at one site does not affect you at other sites.
BleepingComputer suggests using a password manager to keep track of all your passwords to help you with this.
As the database has been released for free, those affected should also be careful of phishing emails that attempt to steal more sensitive information.