KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A chat application for Android claiming to be a secure messaging platform comes with spying functionality and stores user data in an unsecured location that is publicly available.
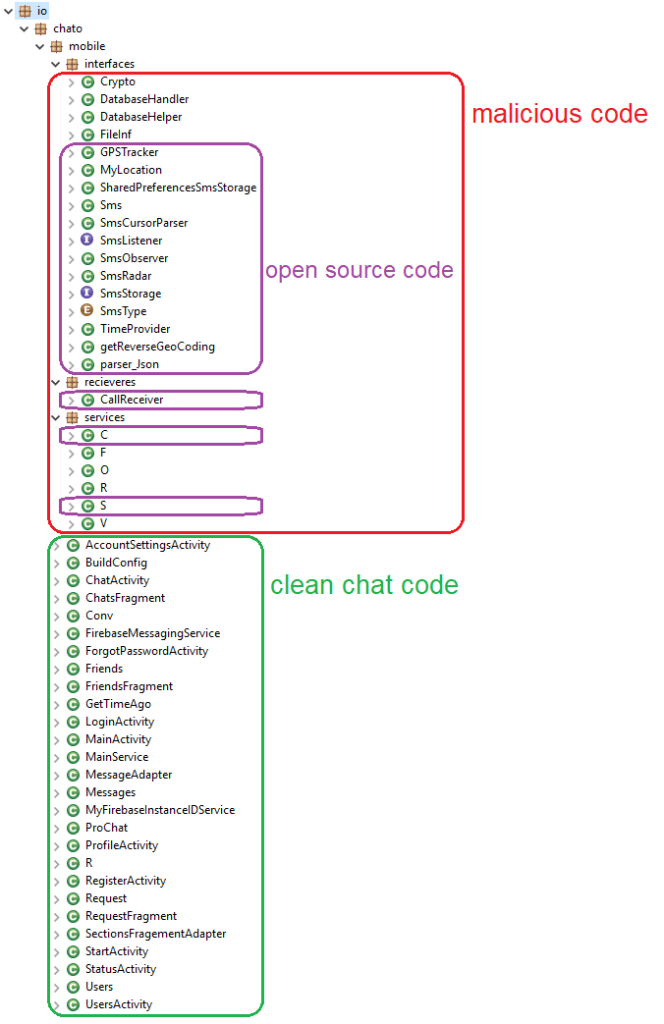
Welcome Chat targets users from a specific region of the world and relies on open source code for recording calls, stealing text messages, and tracking.
The developers of Welcome Chat promoted it as a secure communication solution that is available from the Google Play store. Its intended audience are Arabic-speaking users. It’s important to note that some countries in the Middle East ban this type of apps.
Researchers at cybersecurity company ESET found that the app delivers more than the advertised chat functions and it was never part of the official Android store.
Apps outside Play Store require users to allow installation from unknown sources, which happens in the case of Welcome Chat.
If users fail to heed this red flag, the app asks for permission to send and view SMS messages, access files, record audio, and access contacts and device location. These permissions are normal for a chat app.
nce it gets the consent from the user, Welcome Chat starts sending out information about the device and contacts its command and control (C2) server every five minutes for commands.
The researchers say that monitoring the communication with other Welcome Chat users is at the core of this malicious app, which is complemented by the following malicious actions:
The researchers discovered that much of the code used for spying comes from public sources, either from open-source projects or code snippets published as examples on various forums.
Whoever developed Welcome Chat did not spend much effort on it. They likely looked online for the desired espionage functionality and took the code from the first results.
This conclusion is supported by the age of the code for certain capabilities, which in some cases has been publicly available for at least five years. The call recording and geo-tracking functions, for instance, are eight years old.
A low-skilled attacker is also suggested by the fact that the app and its infrastructure lack basic security like encrypting the data in transit. The connection to the download website is also insecure.
Also read: Cost of GDPR Compliance for Singapore Companies
“Transmitted data is not encrypted and because of that, not only it is available to the attacker, it is freely accessible to anyone on the same network,” says ESET Android malware researcher Lukas Stefanko in a blog post today.
Included in the app’s database on the server is everything but the user account password; names, email addresses, phone numbers, device tokens, profile pictures, messages, and friends list.
Initially, the researchers believed that Welcome Chat is a legitimate app that had been trojanized and tried to warn the developers. They found a clean variant only on VirusTotal. It was uploaded in mid-February, a week after the malicious version was submitted to the scanning platform
This lead to the conclusion that the app was intended for spying from the beginning and that a benign variant from a legitimate developer does not exist.
Although there is no strong evidence, Welcome Chat may be the work of the same group behind BadPatch an espionage campaign identified in 2017 that targeted users in the Middle East.
The connection between the two is the C2 server (pal4u[.]net), used in both campaigns. The same C2 served another cyberespionage operation discovered by Fortinet in 2019, targeting Palestinian users.
Also read: How to Register Data Protection Officer (DPO) in ACRA Bizfile+