KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







GO SMS Pro, an Android instant messaging app with more than 100 million installs, is still exposing the privately shared messages of millions of users even though the developer has been working on a fix for the flaw behind the data leak for almost two weeks.
The flaw, discovered by Trustwave researchers three months ago and publicly disclosed on November 19, enabled unauthenticated attackers to gain unrestricted access to voice messages, videos, and photos privately shared by GO SMS Pro users.
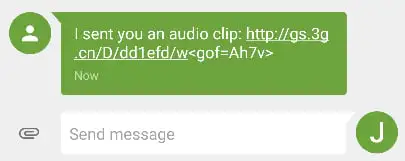
Private files sent by users to contacts who don’t have GO SMS Pro installed can be accessed from the app’s servers via a shortened URL which redirects to a content delivery network (CDN) server used to store all shared messages.
However, the shortened URLs sent to contacts without the app were sequentially generated each time files were shared between users and the media stored on the CDN server.
That made it very easy to go through all these privately shared files, even without knowing the full list of shared URLs.
Also Read: What Is A Governance Framework? The Importance And How It Works
As the researchers found and BleepingComputer was able to verify, the shared files include photos of users’ cars, screenshots of other private messages and Facebook posts, videos and audio recordings, photos of sensitive documents, and even nude photos.
“By taking the generated URLs and pasting them into the multi-tab extension on Chrome or Firefox, it is trivial to access private (and potentially sensitive) media files sent by users of this application,” the researchers explained.
“A new version of the app was uploaded to the Play Store the day before we released our advisory and Google then removed the app from the Play Store sometime on Friday, November 20th, the day after we released our advisory,” the researchers said today in a report shared with BleepingComputer earlier this week.
“However, as of Monday, November 23rd, Google has reinstated the Play Store app with an updated version that same day.”
Despite this, after releasing new versions to address the flaw, the fix partially addresses the flaw exposing users’ private files since all media previously shared is still accessible — even though the sharing feature is no longer working in the latest version.
Sadly for those who have already shared sensitive files using GO SMS Pro there is no way to delete them from the app’s storage server.
Thus anyone can batch download them using a script that generates a list of addresses linking to photos and videos shared using vulnerable app versions.
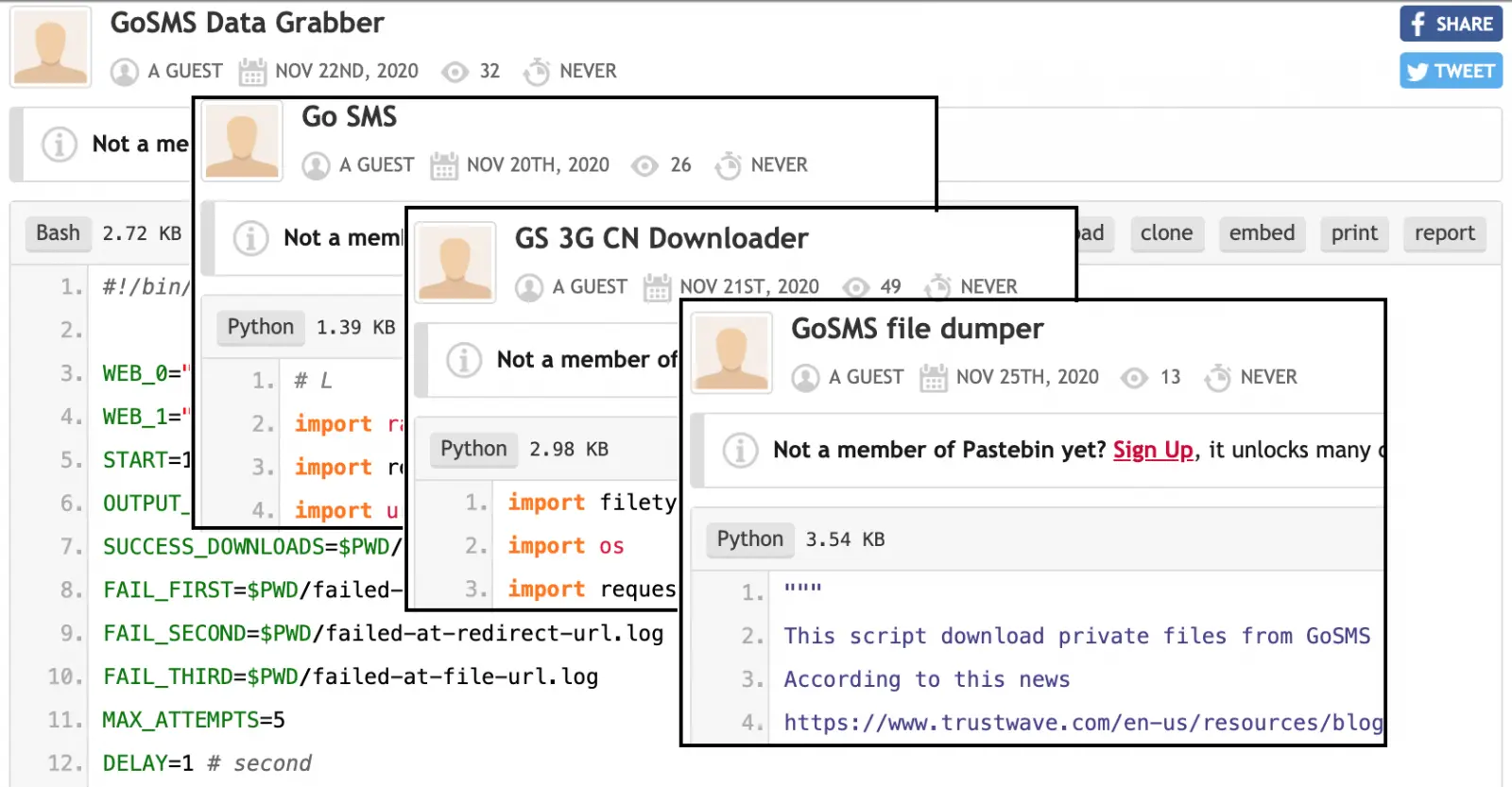
“Unfortunately, we’ve seen a lot of activity around this vulnerability. There have been more tools and scripts released to exploit this on sites like Pastebin and Github than you can shake a stick at,” the researchers added.
To make things even worse, images downloaded from GO SMS Pro’s servers are already being shared on underground forums, and developers of several scripts used to list and download such private messages are updating them daily.
Until now, despite their attempts, the app’s developers haven’t been able to block access to millions of users’ private photos, videos, and voice messages uploaded before this flaw was partially addressed.
Also Read: Website Ownership Laws: Your Rights And What These Protect
Therefore the users’ sensitive messages can be accessed by anyone using publicly available tools an issue which, unfortunately, cannot be fixed even if Google decides to take down the app from the Play Store.
On top of it all, even though Trustwave shared the details of the vulnerability with the app’s developer on August 18 they haven’t received any reply to any of their emails. BleepingComputer has also reached out to the developer team but our messages also went unanswered.