KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Ragnar Locker ransomware gang have published download links for more than 700GB of archived data stolen from Taiwanese memory and storage chip maker ADATA.
A set of 13 archives, allegedly containing sensitive ADATA files, have been publicly available at a cloud-based storage service, at least for some time.
On Saturday, the ransomware actor published on their leak site the download links to a new set of ADATA corporate documents, warning interested parties that the links would not survive for long.
Ragnar Locker’s premonition proved true as MEGA storage service, where the gang chose to host the illegally obtained data, reacted and closed the threat actor’s account, denying access to any files they had shared publicly.
Two of the leaked archives are quite large, weighing over 100GB, but several of them that could have been easily downloaded are less than 1.1GB large.
Per the file metadata published by the threat actor, the largest archive is close to 300GB and its name gives no clue about what it might contain. Another large one is 117GB in size and its name is just as nondescript as in the case of the first one (Archive#2).
Also Read: The 5 Phases of Penetration Testing You Should Know
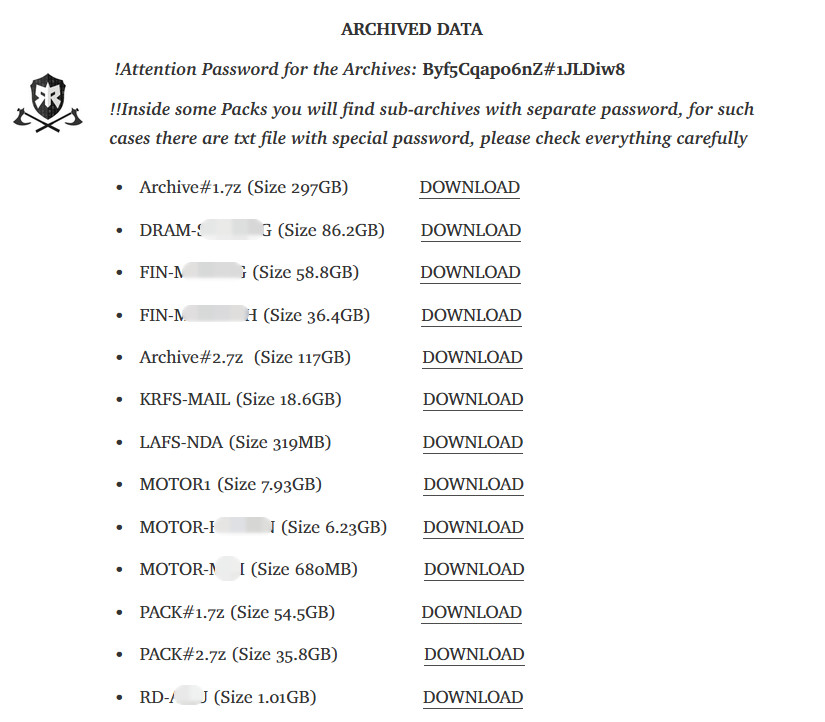
Judging by the names of the archives, Ragnar Locker likely stole from ADATA documents containing financial information, non-disclosure agreements, among other type of details.
The ransomware attack on ADATA happened on May 23rd, 2021, forcing them to take systems offline, the company told BleepingComputer. As the Ragnar Locker leak clearly shows, ADATA did not pay the ransom and restored the affected systems on its own.
The ransomware actor claims stealing 1.5TB of sensitive files before deploying the encryption routine, saying that they took their time in the process because of the poor network defenses.
“So then, as usual, we did offer to cooperate to fix the vulnerabilities and to restore their system and of course, avoid any publication regarding this issue, however, they didn’t value much their own private information, as well as partners/clients/employees/customers information” – Ragnar Locker
Also Read: Got Hacked? Here Are 5 Ways to Handle Data Breaches
The recently leaked batch of archives is the second one that Ragnar Locker ransomware publishes for ADATA. The previous one was posted earlier this month and includes four small 7-zip archives (less than 250MB together) that can still be downloaded.