KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Business software provider Zoho urged customers today to update their Desktop Central and Desktop Central MSP installations to the latest available version.
Zoho’s ManageEngine Desktop Central is a management platform that helps admins deploy patches and software automatically over the network and troubleshoot them remotely
The warning comes after the company patched a critical vulnerability (tracked as CVE-2021-44515) which could allow attackers to bypass authentication and execute arbitrary code on unpatched ManageEngine Desktop Central servers (Desktop Central Cloud is not affected).
“As we are noticing indications of exploitation of this vulnerability, we strongly advise customers to update their installations to the latest build as soon as possible,” Zoho explained in a notification issued today.
To detect if your installation was compromised using this security flaw, you can use Zoho’s Exploit Detection Tool and go through the procedure detailed here.
Also Read: Top 10 Best Freelance Testing Websites That Will Pay You
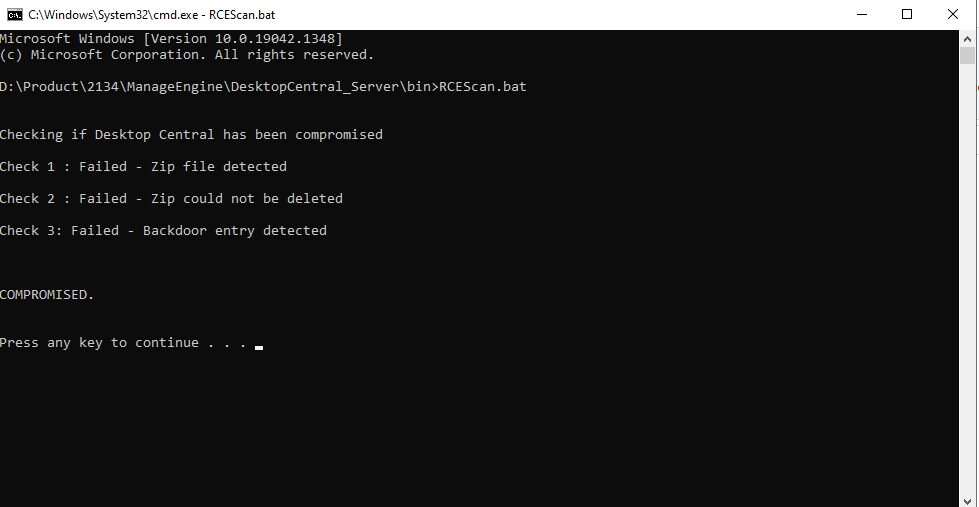
If impacted, the company recommends disconnecting and backing up all critical business data on affected systems from the network, formatting the compromised servers, restoring Desktop Central, and updating it to the latest build once the installation ends.
If signs of compromise have been found, Zoho also recommends initiating a “password reset for all services, accounts, Active Directory, etc. that has been accessed from the service installed machine” together with Active Directory administrator passwords.
A quick search using Shodan has revealed over 3,200 ManageEngine Desktop Central instances running on various ports and exposed to attacks.
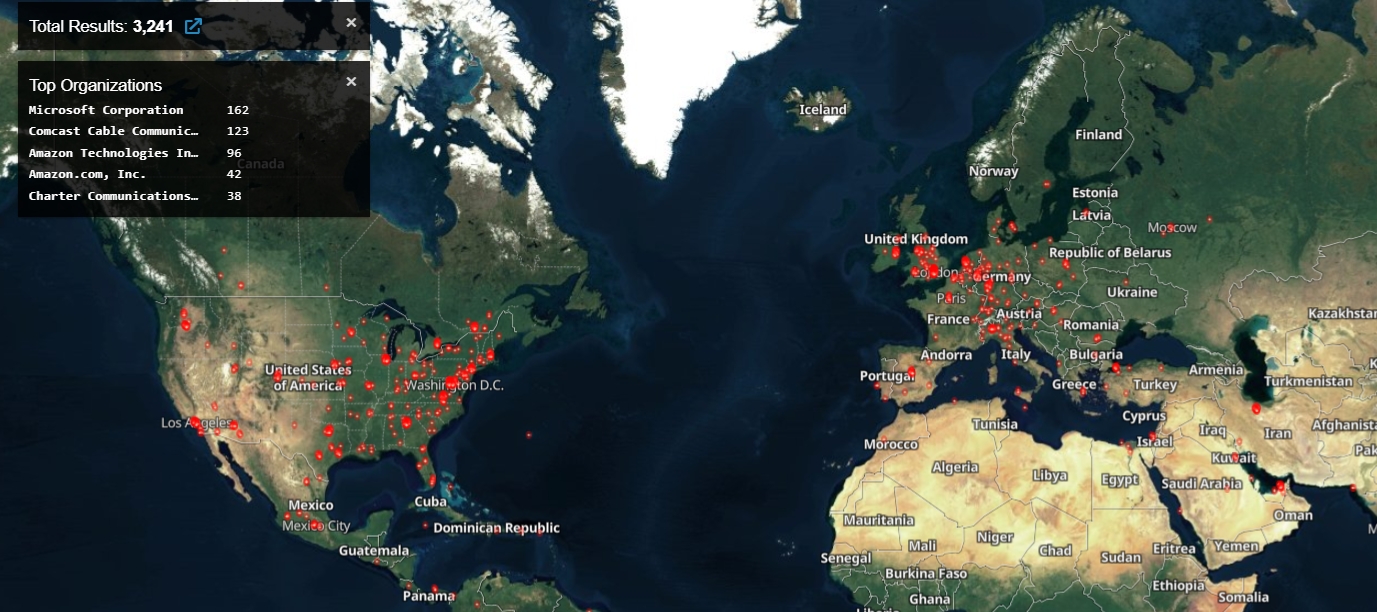
This is not the first time Zoho ManageEngine servers have been targeted in attacks recently. Desktop Central instances, in particular, have been hacked before and access to compromised networks sold on hacking forums since at least July 2020.
Also Read: PDP Act (Personal Data Protection Act) Laws and Regulation
According to cyber intelligence company KELA who spotted the threat actors behind these offers, they had sold network access to companies worldwide and claimed to have access to others from the US, UK, Spain, and Brazil.
More recently, between August and October 2021, Zoho ManageEngine products have been targeted by state hackers using tactics and tooling similar to those used by Chinese-backed hacking group APT27.
The attackers focused on and compromised the networks of critical infrastructure organizations worldwide in three different campaigns using an ADSelfService zero-day exploit between early-August and mid-September, an n-day AdSelfService exploit until late October, and a ServiceDesk one starting with October 25.
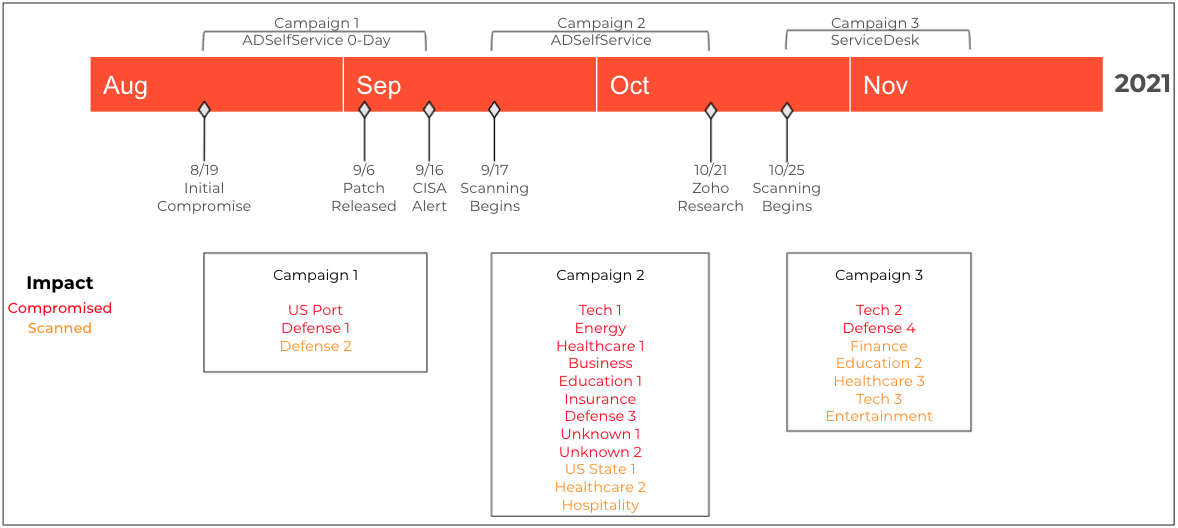
After these campaigns, the FBI and CISA also issued joint advisories (1, 2) warning of APT actors exploiting the ManageEngine vulnerabilities to drop webshells on the networks of targeted critical infrastructure orgs, including the healthcare, financial services, electronics, and IT consulting industries.
Additionally, the two US federal agencies said that confirming a successful compromise in these attacks may be difficult since “the attackers are known to run clean-up scripts designed to remove traces of the initial point of compromise and hide any relationship between exploitation of the vulnerability and the webshell.”
A Zoho spokesperson was not immediately available for comment when contacted by BleepingComputer earlier today about the CVE-2021-44515 vulnerability being exploited in the wild.