KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Researchers at ESET today published details about a threat actor that has been operating for at least nine years, yet their activity attracted almost no public attention.
Going largely unnoticed for this long is a rare occurrence these days as malicious campaigns from long-standing adversaries overlap at one point or give sufficient clues for researchers to determine that the same actor is behind them.
At the Virus Bulletin 2020 security conference today, ESET provided details about the victims and operations of a newly discovered advanced persistent threat (APT) named XDSpy, after the main malware downloader used in attacks.
ESET malware researchers Matthieu Faou and Francis Labelle say that the group has been running cyber-espionage campaigns since at least 2011.
XDSpy’s main interest is in the Eastern Europe and Balkans regions (Belarus, Moldova, Russia, Serbia, and Ukraine), targeting primarily government agencies (military, Ministries of Foreign Affairs), although private companies are also among its victims.
Before ESET’s report, the national cybersecurity incident response center (CERT) in Belarus published in February 2020 an advisory on an XDSpy spear phishing campaign spread to more than 100 targets, among them:
Based on the malicious code used in attacks, network infrastructure, and victimology, ESET researchers could not confidently link XDSpy activity to a known APT group. Provided the long-term activity and other factors, behind XDSpy is likely a professional actor.
“We believe that the developers might be working in the UTC+2 or UTC+3 time zone, which is also the time zone of most of the targets. We also noticed they were only working from Monday to Friday, suggesting a professional activity” – ESET
Spear phishing appears to be the main attack vector of the group, with emails that either contain a malicious file or link to one (typically a ZIP or RAR archive).
The archive contains a LNK file that downloads a script that installs XDDown, the main component used by the group to establish persistence and download malicious plugins from the command and control server (hardcoded).
Also Read: How To Check Data Breach And How Can We Prevent It
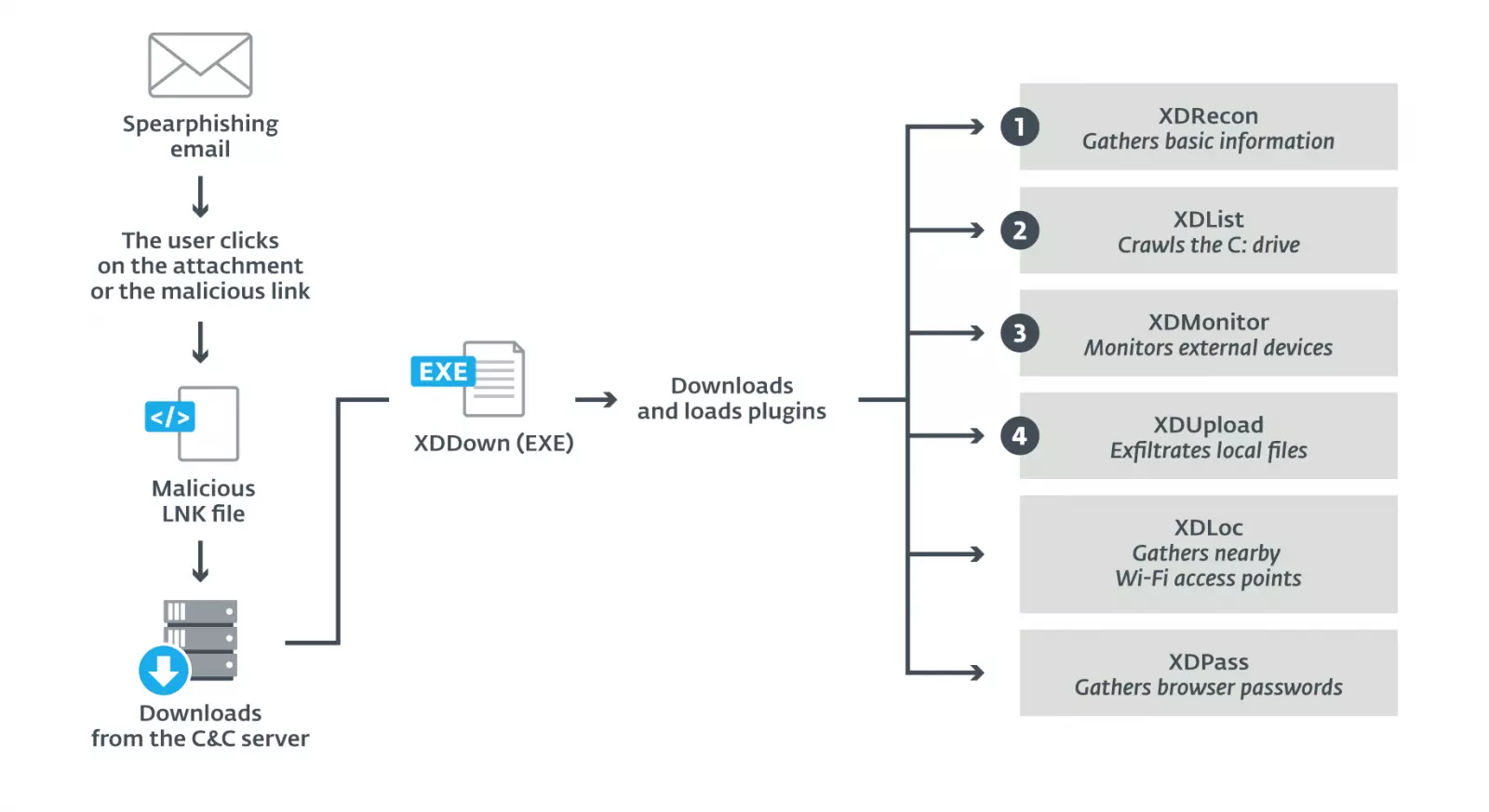
ESET discovered multiple plugins used by XDSpy for reconnaissance, gathering details, and stealing files of interest based on their extension:
In more recent operations (end of June), the actor exploited a vulnerability in Internet Explorer (CVE-2020-0968 – patched in April) on which little was known at the time and no proof-of-concept exploit code existed.
“We think that XDSpy either bought this exploit from a broker or developed a 1-day exploit themselves by looking at previous exploits for inspiration” – ESET
The exploit used in that attack, though, had similarities with other exploits used by DarkHotel APT. However, ESET believes there is no connection between the two groups and the common ground may be accounted for by the use of the same exploit broker.
ESET says that until moving to exploiting the IE vulnerability, the group relied on “the same basic malware architecture.” This switch shows technical evolution and may foretell increased activity from this actor.
On its GitHub page, ESET published a comprehensive list of indicators of compromise (IoCs) that includes hashes for known XDSpy components, details about their network infrastructure, and the activity on the infected system.
Also Read: How Bank Disclosure Of Customer Information Work For Security