KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The team behind a popular WordPress plugin has disclosed a critical file upload vulnerability and issued a patch.
The vulnerable plugin, Contact Form 7, has over 5 million active installs making this urgent upgrade a necessity for WordPress site owners out there.
This week, Contact Form 7 project has disclosed an unrestricted file upload vulnerability (CVE pending) in the WordPress plugin that can allow an attacker to bypass Contact Form 7’s filename sanitization protections when uploading files.
An attacker can upload a crafted file with arbitrary code on the vulnerable server using the plugin.
Then, by exploiting this severe vulnerability, the file can be executed as a script by the attacker to run the code within.
“Contact Form 7 5.3.2 has been released. This is an urgent security and maintenance release. We strongly encourage you to update to it immediately,” reads the project’s security advisory.
The vulnerability has been discovered and reported by Jinson Varghese Behanan, an information security analyst with Astra Security.
“The vulnerability was found while we were doing a security audit for a client,” said the analyst.
Also Read: The Scope Of Singapore Privacy: How We Use It In A Right Way
“Seeing the criticality of the vulnerability and the number of WordPress websites using this popular plugin, we quickly reported the vulnerability. The developer was even quicker in issuing a fix. Kudos to the Contact Form 7 team for leading by example,” Behanan told BleepingComputer.
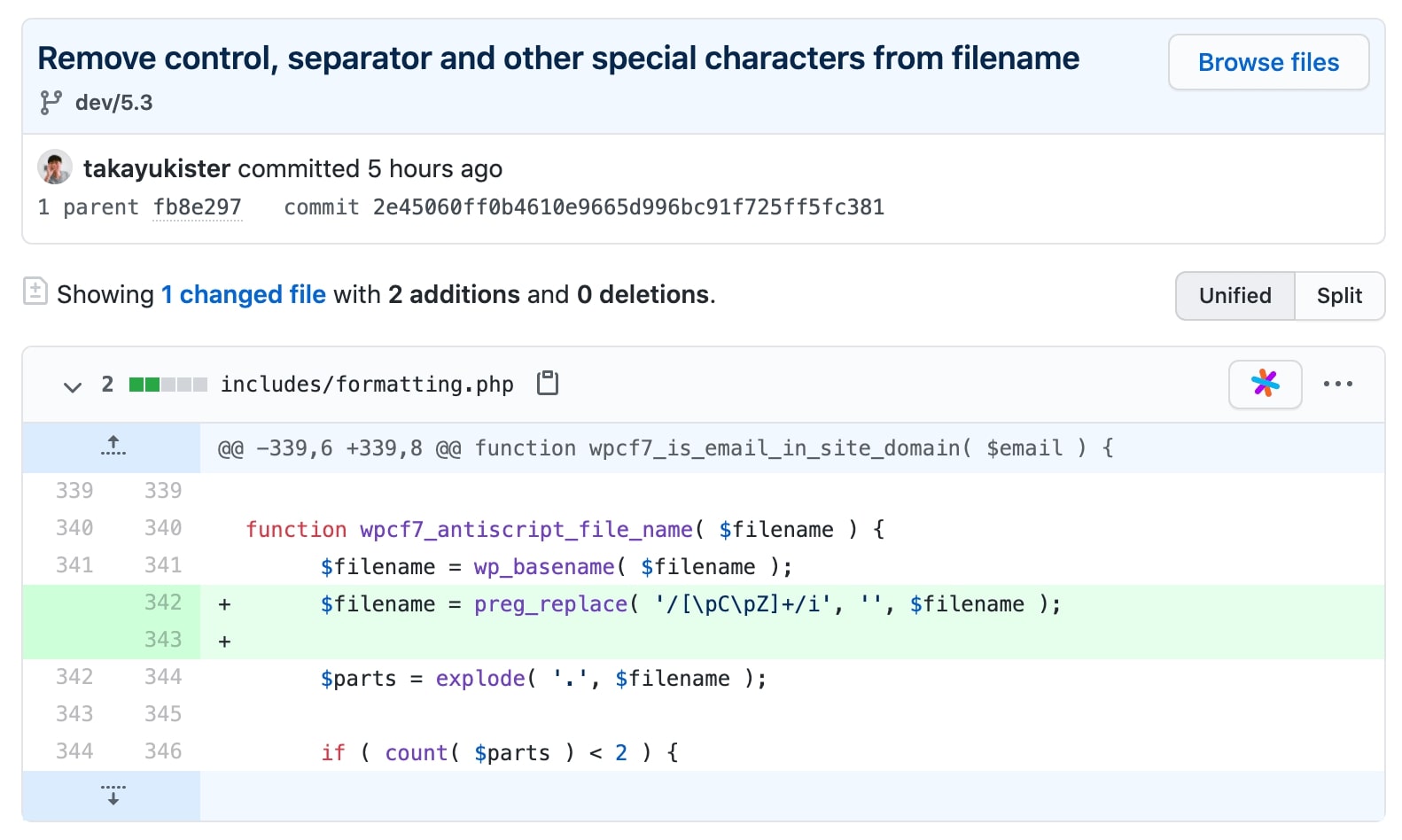
As observed by BleepingComputer, the issue occurs in the includes/formatting.php file which is part of the Contact Form 7 plugin code.
In the vulnerable versions, the plugin does not remove special characters from the uploaded filename, including the control character and separators.
This could potentially allow an attacker to upload a filename containing double-extensions, separated by a non-printable or special character, such as a file called “abc.php .jpg.”
The separator between the two extensions, in this example, is a tab (\t) character.
To the client-side interface of Contact Form 7, this may appear to be an image file (*.jpg).
When uploaded to the server, however, Contact Form 7 will likely parse the filename up until the first extension and discard the second one due to a separator.
The new filename would therefore become “abc.php,” a PHP script, which the attacker can now access, to execute arbitrary code on the server.
The fix made by the project, shown below, contains a regex-based validation to catch cases like this:
Also Read: Deemed Consent PDPA: How Do Businesses Comply?
This is not the first instance of a serious double-extension vulnerability lurking in blogging and CMS platforms.
Last month, Drupal sites were found to have a double extension file upload vulnerability.
April this year, a NodeJS module could be exploited to achieve remote code execution via file uploads.
The patched version 5.3.2 of the plugin can be downloaded from WordPress. Users of Contact Form 7 are advised to apply this urgent update immediately.