





US-based ski and golf resort operator Boyne Resorts has suffered a cyberattack by the WastedLocker operation that has impacted company-wide reservation systems.
Boyne Resorts owns and operates eleven properties located in the USA and Canada and has 11,000 employees. Many of these properties are situated on well-known ski mountains, including Big Sky, Montana, Sugarloaf, Maine, and Brighton, Utah.
Today, BleepingComputer received an anonymous tip from an alleged Boyne Resorts employee who stated that the company suffered an undisclosed ransomware attack last weekend.
Also Read: The Top 10 Best And Trusted List Of Lawyers In Singapore
We were told that the attack affected their corporate offices and then spread to IT systems of the resorts they operate, forcing them to shut down portions of their network to prevent the ransomware spread.
BleepingComputer has since confirmed with a second source that Boyne Resorts was attacked using the WastedLocker ransomware, the same one used in the attack on Garmin in July.
Due to this attack, it is not possible to book lodging at the resort as the company-wide reservation systems are impacted by the attack, including the online reservation systems at each hotel’s website.
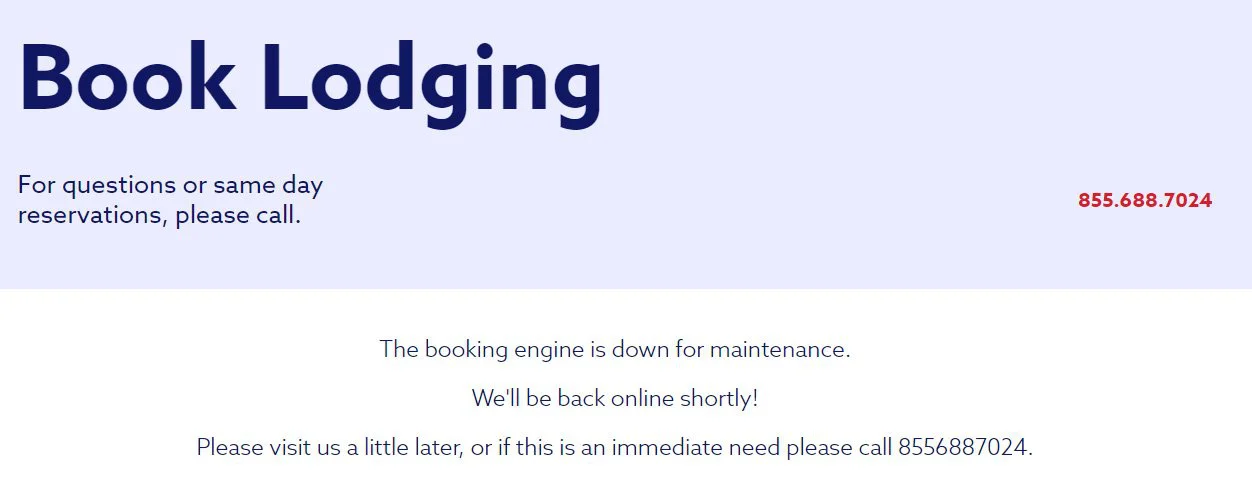
BleepingComputer was told that the reservation systems are expected to be down for another couple of days. This attack comes at a bad time for Boyne as people begin to plan potential ski trips for the winter.
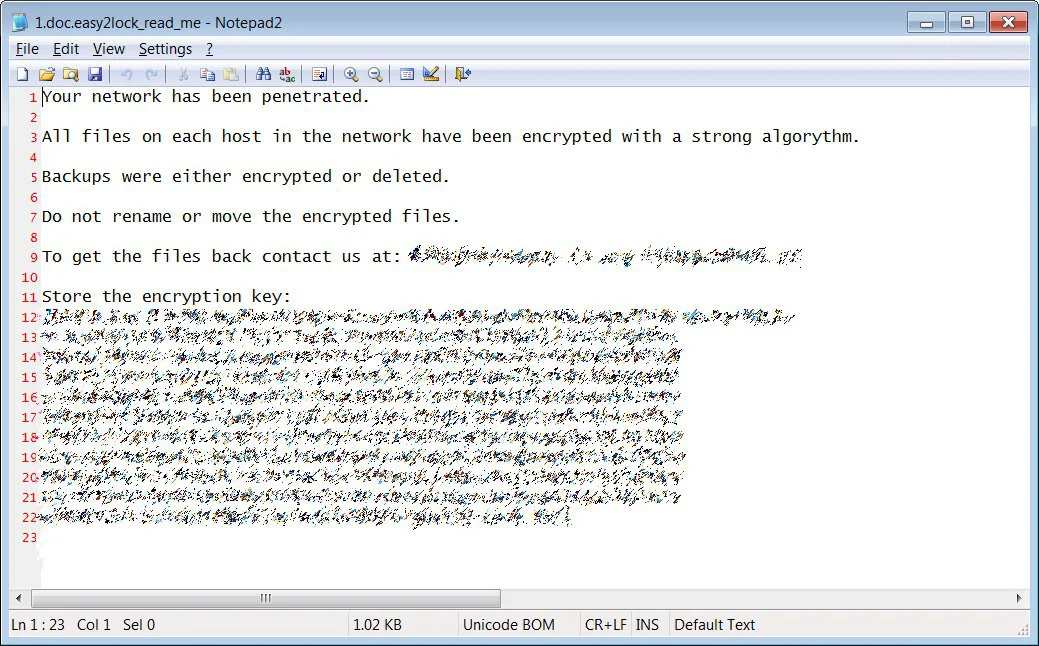
As part of this attack, we are told that encrypted files were renamed so that the .easy2lock extension was appended to each file’s name.
BleepingComputer has been able to find a sample of the WastedLocker ransomware uploaded to VirusTotal on October 14th, 2020, that utilizes the .easy2lock extension. Due to its earlier date, we do not believe this is the exact sample used in the attack on Boyne Resorts.
Below is an example ransom note created by this WastedLocker Ransomware variant. This ransom note may not be the same as the one used during Boyne Resort’s attack.
BleepingComputer has contacted Boyne Resorts with further questions about this attack but has not received a reply.
Also Read: The Importance Of Knowing Personal Data Protection Regulations
Security firms attribute WastedLocker to a Russian-based hacking group known as Evil Corp (aka the Dridex gang).
This group has been active since at least 2007 and is known for developing the Dridex malware and a ransomware strain known as BitPaymer.
In December 2019, The U.S. Treasury Department sanctioned Evil Corp for causing more than $100 million in financial damages.
Due to this, it is a tricky situation if Boyne Resorts wanted to pay the ransom as they would potentially violate United States sanctions.
Ransom payments to WastedLocker have become riskier this month, as the U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) issued a warning that organizations making ransom payments face sanctions risks if their actions violate OFAC regulations.