KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A hacker-for-hire group called Void Balaur has been stealing emails and highly-sensitive information for more than five years, selling it to customers with both financial and espionage goals.
With more than 3,500 targets spread across almost all continents, this prolific threat actor is advertising its services on Russian underground forums.
Security researchers at Trend Micro profiling Void Balaur’s activity say that the business model of this actor is to steal “the most private and personal data of businesses and individuals” and sell it to interested customers.
Targets include individuals as well as organizations in various sectors (telecommunications, retail, financial, medical, biotechnology), especially if they have access to troves of private data.
Also Read: Data Protection Policy: 8 GDPR Compliance Tips
“Void Balaur is not only into hacking email mailboxes but is also in the business of selling the sensitive private information of its targets. This includes cell tower log data, passport details, SMS messages, and more. In addition, Void Balaur appears to target many organizations and individuals that are likely to have access to highly sensitive data on people” – Trend Micro
The hacking activity of Void Balaur is believed to go as far back as 2015, although the earliest references about this actor date from September 2017, in the form of complaints about the group spam advertising its services.
Paid ads from Void Balaur started to appear in 2018 on Russian-speaking forums Darkmoney (carding), Probiv, Tenec (stolen credentials), and Dublikat.
The services included access to free webmail (Gmail, Protonmail, Mail.ru, Yandex, VK), social media (Telegram), and corporate email accounts. The hackers would offer customers copies of the breached mailboxes.
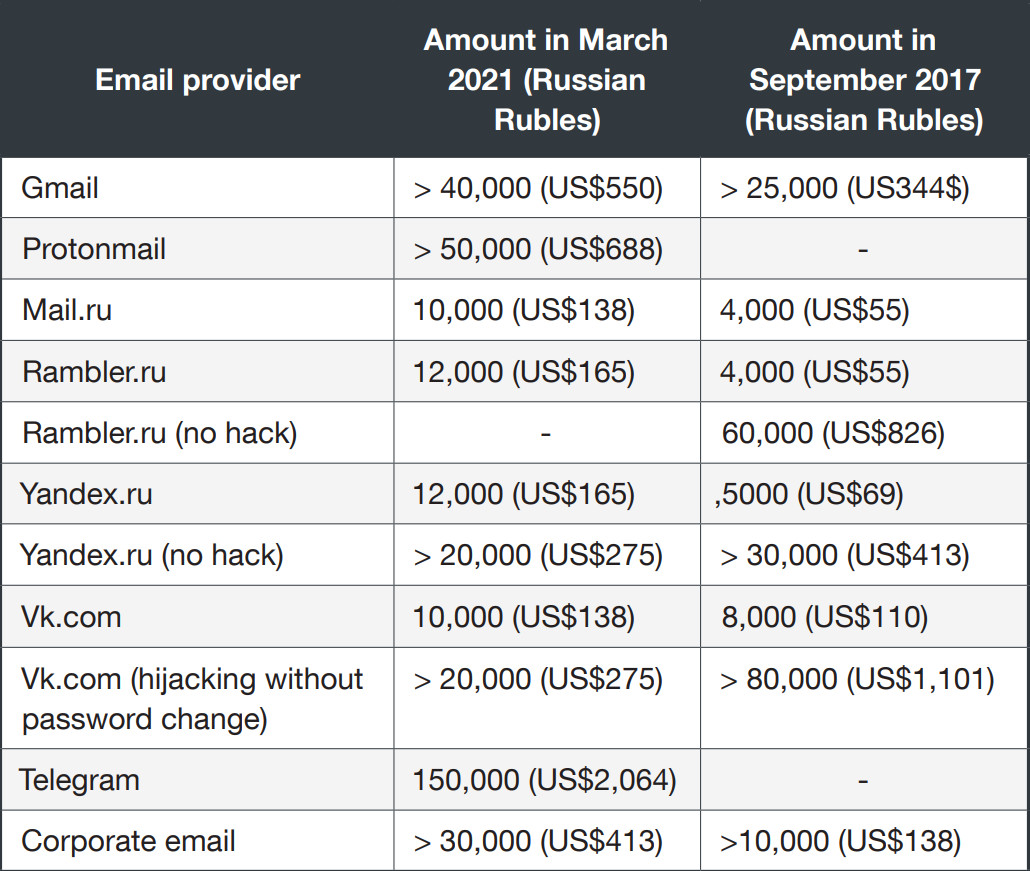
In 2019, the group’s services diversified as they began to sell sensitive private data of Russian individuals for starting prices between $21 and $124. The info included:
The new services also provided data from cellular services, such as phone numbers, phone call and SMS records (with or without cell tower location), mapping the calls, phone or SIM card location, printouts of text messages.
It is unclear how Void Balaur obtained this information. Bribing insiders at telecom companies is one explanation.
Another one, for which Trend Micro has supporting evidence, is hacking key engineers and individuals in management positions at various telcos in Russia.
Also Read: Don’t Be Baited! 5 Signs of Phishing in Email
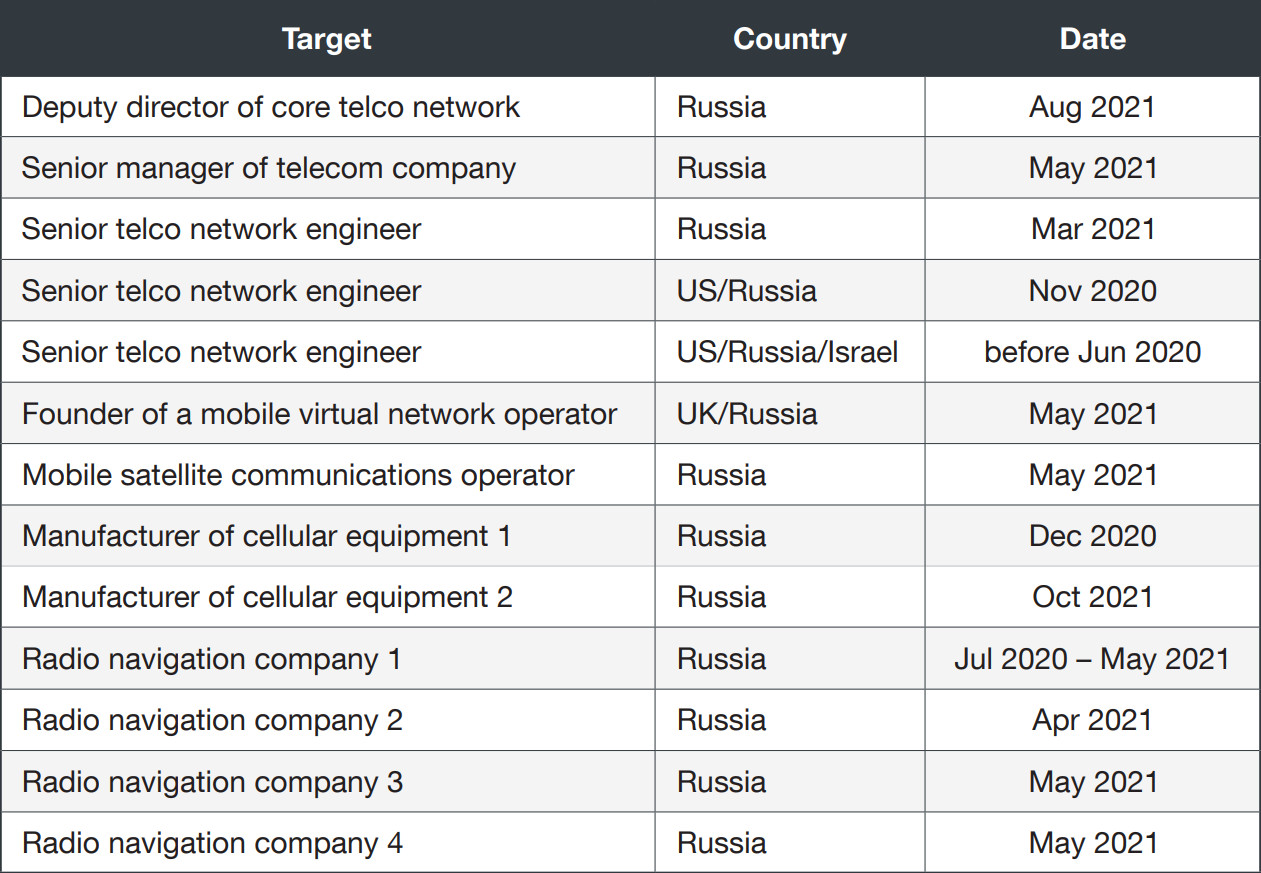
Void Balaur’s targets are more diverse than this and attacks on them date far back as Trend Micro found more than 3,500 email addresses for individuals and companies in attacks attributed to this threat actor.
Based on reports from Canadian non-profit eQualitie and Amnesty International, the researchers could connect Void Balaur activity to attacks that started in 2016 against human rights activists and journalists in Uzbekistan.
More recent activity from the group in September 2020 targeted political personalities in Belarus, presidential candidates, and a member of the opposition party.
In September 2021, the hackers focused on “the private email addresses of a former head of an intelligence agency, five active government ministers (including the minister of defense) and two members of the national parliament of an Eastern European country.”
Political figures and diplomats in other countries (Armenia, Ukraine, Kazakhstan, Russia, France, Italy, Norway, Slovakia), media organizations, dozens of journalists are also among the targets of Void Balaur’s phishing activity.
In another campaign that lasted between September 2020 and August 2021, Void Balaur targeted board members, directors, and executives (and their family members) of companies of a large Russian corporation.
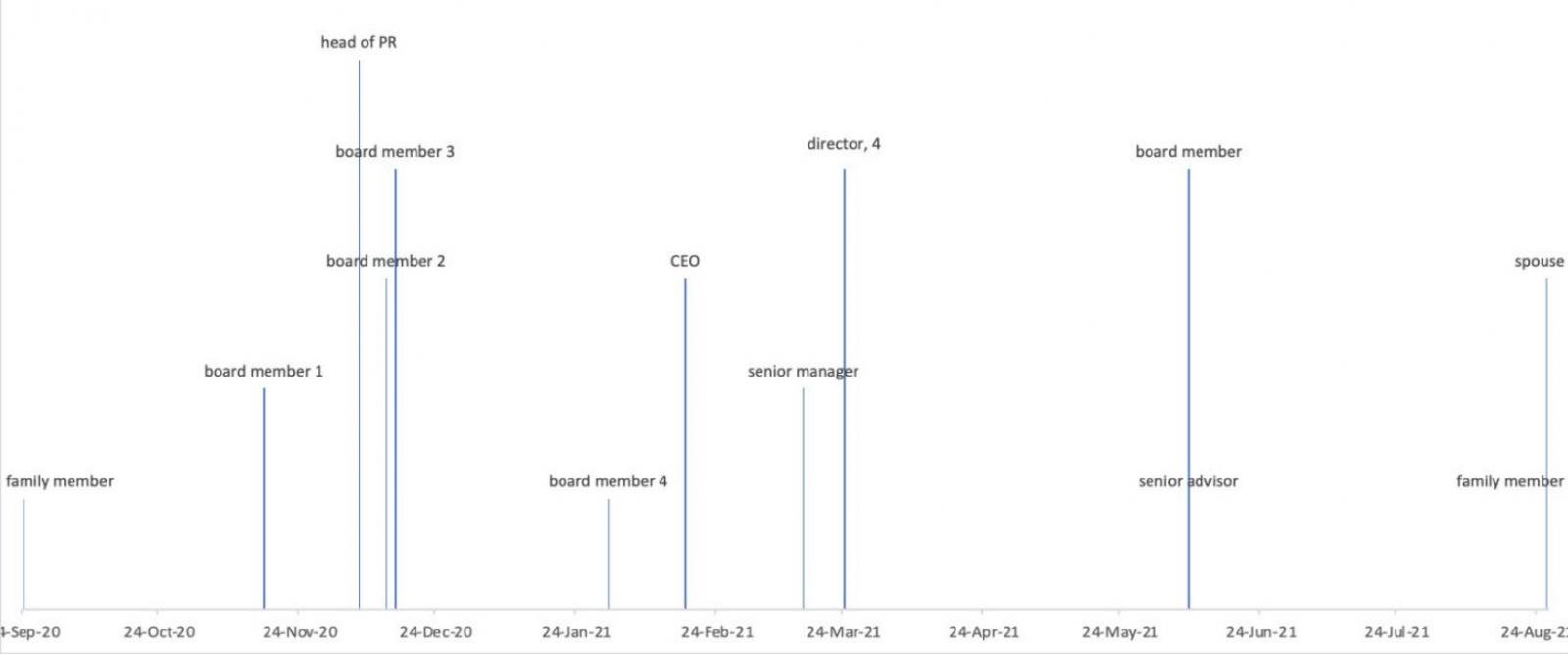
The beneficiaries of these attacks remain unknown, but long-term espionage campaigns typically serve nation-state, corporate, or political interests.
Another set of targets includes organizations that handle large amounts of individual sensitive data, which could be used to facilitate financially-motivated attacks:
Apart from these, Void Balaur has been constantly seeking access to cryptocurrency wallets of various exchange services (Binance, EXMO, BitPay, YoBit), using phishing sites to lure victims.
In the case of phishing EXMO users, although the threat actor had multiple domains, one of them was used for almost three years.
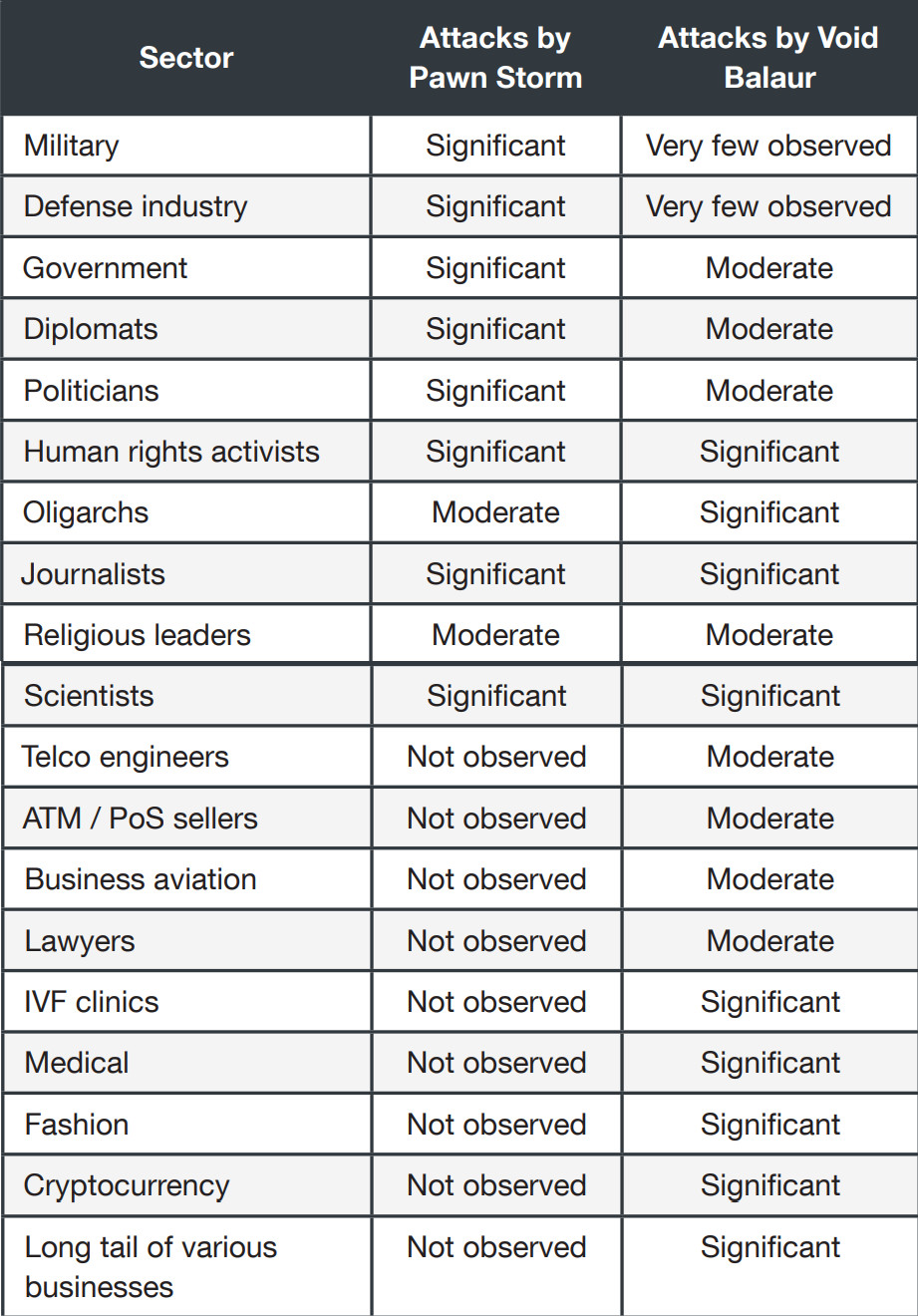
Void Balaur emerged on Trend Micro’s radar after a source provided multiple phishing emails that the researchers initially believed to be the work of Pawn Storm, a Russian threat actor also known by the names Fancy Bear, Sednit, Pawn Storm, and Strontium.
Although they ended up attributing the emails to Void Balaur, the researchers also found an overlap between the two groups, despite the hackers-for-hire showing more diverse customers and targets.
“In total, we have observed a dozen email addresses that were targeted by both Pawn Storm during the period of 2014 to 2015, and by Void Balaur from 2020 to 2021,” the researchers write in a report today.
“Besides the religious leaders, we also saw attacks on diplomats, politicians and a journalist from both Pawn Storm and Void Balaur,” Trend Micro added.
From the evidence that Trend Micro collected, it is clear that Void Balaur focuses on selling private data to anyone willing to pay the right money. It is a cyber-mercenary group that does not care what its customers do with the data they buy.