KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







US, UK, and Australian cybersecurity agencies warned today of ongoing exploitation of Microsoft Exchange ProxyShell and Fortinet vulnerabilities linked to an Iranian-backed hacking group.
The warning was issued as a joint advisory released by the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), the Australian Cyber Security Centre (ACSC), and the United Kingdom’s National Cyber Security Centre (NCSC).
“FBI and CISA have observed this Iranian government-sponsored APT group exploit Fortinet vulnerabilities since at least March 2021 and a Microsoft Exchange ProxyShell vulnerability since at least October 2021 to gain initial access to systems in advance of follow-on operations, which include deploying ransomware,” CISA said.
“ACSC is also aware this APT group has used the same Microsoft Exchange vulnerability in Australia,” the joint advisory adds.
Also Read: 10 Tips For Drafting Key Terms In A Service Agreement
The Iranian state hackers focus their attacks on US critical infrastructure sectors (e.g., transportation, healthcare) and Australian organizations.
They aim to gain initial access to targets from critical sectors that could later be used for other nefarious purposes, including data exfiltration, ransomware deployment, and extortion.
CISA and the FBI also shared info on multiple instances when the Iranian-sponsored hacking group was observed, including:
The information included in this joint advisory lines up with details shared in a Microsoft Threat Intelligence Center (MSTIC) report on Tuesday.
In the report, Microsoft provided information on the evolution of Iranian APTs and their capability to adapt as an always shape-shifting threat.
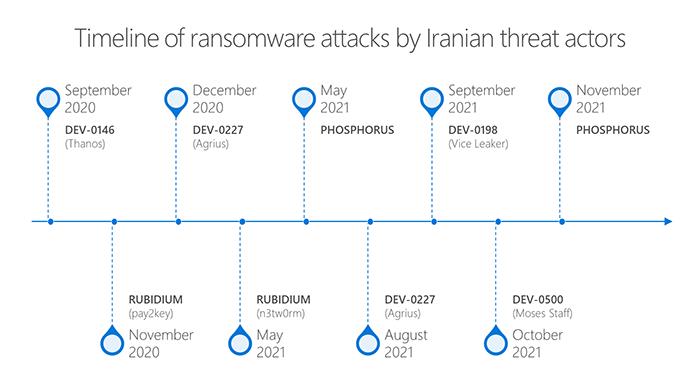
Microsoft said it has been tracking six Iranian threat groups who have been deploying ransomware and exfiltrating data in attacks that started in September 2020.
Also Read: How To Make A PDPC Complaint: With Its Importance And Impact
MSTIC observed them scanning and exploiting vulnerabilities in many products, including Fortinet’s FortiOS SSL VPN and Microsoft Exchange server vulnerable to ProxyShell bugs.
The FBI also warned private industry partners a week ago of an Iranian threat actor trying to buy stolen information associated with US and worldwide organizations from clear and dark web sources to breach their systems,
“The FBI, CISA, ACSC, and NCSC urge critical infrastructure organizations to apply the recommendations listed in the Mitigations section of this advisory to mitigate risk of compromise from Iranian government-sponsored cyber actors,” the agencies added.
More technical details on these attacks, including indicators of compromise, MITRE ATT&CK tactics and techniques, detection measures, and mitigations, can be found in the joint advisory published earlier today.