KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







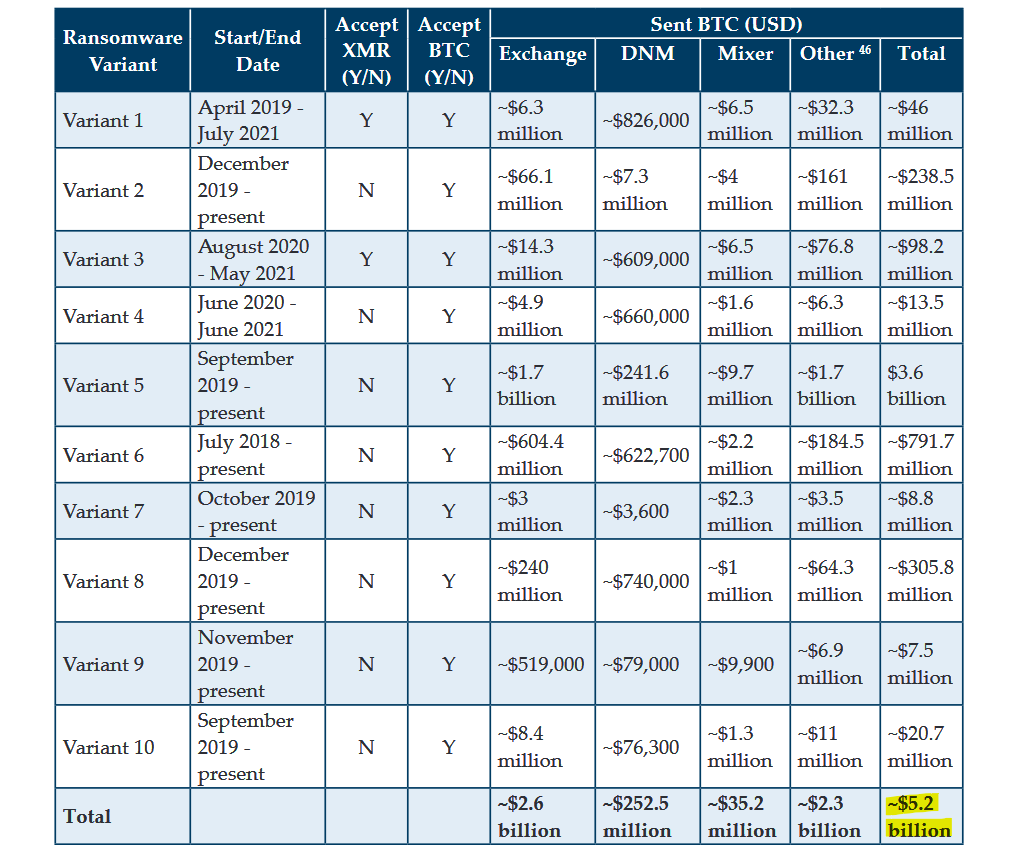
The U.S. Treasury Department’s Financial Crimes Enforcement Network (FinCEN) has identified roughly $5.2 billion worth of outgoing Bitcoin transactions likely tied to the top 10 most commonly reported ransomware variants.
FinCEN identified 177 CVC (convertible virtual currency) wallet addresses used for ransomware-related payments after analyzing 2,184 SARs (Suspicious Activity Reports) filed between January 1, 2011, and June 30, 2021, and reflecting $1.56 billion in suspicious activity.
Based on blockchain analysis of transactions tied to the 177 CVC wallets, FinCEN identified roughly $5.2 billion in outgoing BTC transactions potentially tied to ransomware payments.
FinCEN also linked these transactions to a total of $590 million exposed by 458 transactions reported and 635 SARs filed by financial institutions this year, between January 2021 and June 2021.
Also Read: What is Pentest Report? Here’s A Walk-through
“According to data generated from ransomware-related SARs, the mean average total monthly suspicious amount of ransomware transactions was $66.4 million and the median average was $45 million,” FinCEN said.
“FinCEN identified bitcoin (BTC) as the most common ransomware-related payment method in reported transactions.”
The total value of ransomware-related SARs from the first six months of 2021, $590 million, already exceeds the $416 million reported for the entire year of 2020. The 635 SARs filed until June 2021 have also exploded compared to the 487 SARs reported last year.
From SARs filed until June 2021, FinCEN also identified 68 active ransomware variants (most commonly reported were REvil/Sodinokibi, Conti, DarkSide, Avaddon, and Phobos), as well as the top 10 ransomware with most victims and highest demanded ransoms.
FinCEN’s Financial Trend Analysis report comes on the heels of governments worldwide announcing that they will crack down on cryptocurrency payment channels used by ransomware gangs.
The joint statement was issued afer virtual Counter-Ransomware Initiative meetings facilitated this week by the White House National Security Council in response to ongoing ransomware attacks targeting critical worldwide infrastructure.
Also Read: The PDPA Data Breach August 2020: A Recap of 8 Alarming Cases
As revealed today, mitigating ransomware groups’ abuse of virtual assets on a global scale would directly impact their business model and the main instrument used to collect ransoms from their victims.
This way, the Counter-Ransomware Initiative wants to drain their accounts and take down their operations by disrupting the ransomware gangs’ funding channels.
Last month, the U.S. Treasury also announced its first-ever sanctions against a cryptocurrency exchange for facilitating ransom transactions for ransomware gangs. as well as helping them evade sanctions.
One year ago, it also warned that ransomware negotiators that they could face civil penalties for facilitating ransom payments if ransomware gangs already on its sanctions list were involved.