KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







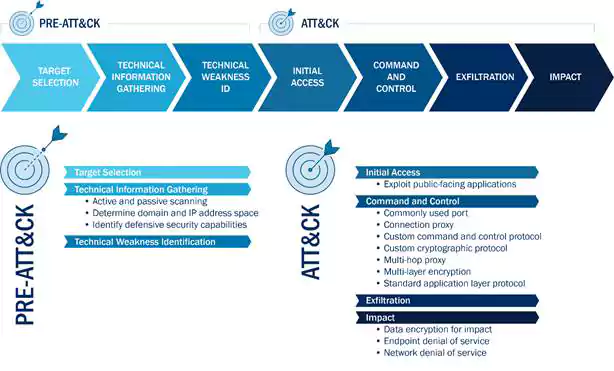
The Cybersecurity and Infrastructure Security Agency (CISA) today issued guidance on how to protect against cyberattacks launched from the activity originating from or routed through the Tor anonymity network.
Tor is a software enabling internet anonymity by automatically encrypt and reroute a user’s web requests through a network of Tor nodes (relay layers).
Tor’s infrastructure is also used by threat actors to hide their identity and location by hiding their real IP address under the protection of a Tor exit node when engaging in malicious cyber activity.
The advisory was written in collaboration with the Federal Bureau of Investigation (FBI) and it shares technical details on how threat actors can use Tor’s software and network infrastructure for anonymity during their malicious campaigns.
“Malicious cyber actors use Tor to mask their identity when engaging in malicious cyber activity impacting the confidentiality, integrity, and availability of an organization’s information systems and data,” CISA and the FBI said.
“Examples of this activity include performing reconnaissance, penetrating systems, exfiltrating and manipulating data, and taking services offline through denial-of-service attacks and delivery of ransomware payloads.
“CISA and the FBI recommend that organizations assess their individual risk of compromise via Tor and take appropriate mitigations to block or closely monitor inbound and outbound traffic from known Tor nodes.”
CISA advises organizations to determine their “individual risk by assessing the likelihood that a threat actor will target its systems or data and the probability of the threat actor’s success given current mitigations and controls.”
“This assessment should consider legitimate reasons that non-malicious users may prefer to, or need to, use Tor for accessing the network.”
To detect malicious activity targeting their assets, orgs can use an indicator-based approach by looking for evidence of unusual traffic levels with Tor exit nodes in netflow, packet capture (PCAP), and web server logs that could potentially represent malicious reconnaissance, exploitation, C2, or data exfiltration behavior.
Network defenders can also take a behavior-based approach that requires searching for operational patterns of Tor client software and protocols such as increased usage of TCP and UDP ports commonly affiliated with Tor (9001, 9030, 9040, 9050, 9051, and 9150), higher incidence of DNS queries for domains ending with the .onion or torproject.org, suffixes.
Web application and router firewalls, and host/network intrusion detection systems are solutions that may already give some level of detection capability for discovering key indicators of malicious activity routed through the Tor network.
“Organizations should research and enable the pre-existing Tor detection and mitigation capabilities within their existing endpoint and network security solutions, as these often employ effective detection logic,” CISA recommends.
Also read: The impact of GDPR and PDPA in Singapore
Organizations that are at risk of being attacked by malicious actors as part of campaigns making use of the Tor network for concealment purposes are advised by CISA to implement a series of mitigations as defense measures.
Unfortunately, mitigations might also have an impact on the access of legitimate users who could want to visit the organizations’ internet-facing assets while having their privacy protected by Tor.
CISA recommends taking three different approaches when mitigating Tor-associated malicious activity, depending on the impact they might have on legitimate Tor users:
• Most restrictive approach: Block all web traffic to and from public Tor entry and exit nodes (does not completely eliminate the threat of malicious actors using Tor for anonymity, as additional Tor network access points, or bridges, are not all listed publicly.)
• Less restrictive approach: Tailor monitoring, analysis, and blocking of web traffic to and from public Tor entry and exit nodes: orgs that do not wish to block legitimate traffic to/from Tor entry/exit nodes should consider adopting practices that allow for network monitoring and traffic analysis for traffic from those nodes, and then consider appropriate blocking. This approach can be resource-intensive but will allow greater flexibility and adaptation of defensive. Legitimate usage examples: deployed military or other overseas voters.
• Blended approach: Block all Tor traffic to some resources, allow and monitor for others (i.e., intentionally allowing traffic to/from Tor only for specific websites and services where legitimate use may be expected and blocking all Tor traffic to/from non-excepted processes/services). This may require continuous re-evaluation as an entity considers its own risk tolerance associated with different applications. The level of effort to implement this approach is high.
While blocking outbound and inbound traffic to and from known Tor entry nodes should protect against less sophisticated actors, experienced threat actors can circumvent such mitigation measures by using other anonymization tactics and tech like virtual private networks (VPNs) or Tor features like Tor bridges and pluggable transports.
“Ultimately, each entity must consider its own internal thresholds and risk tolerance when determining a risk mitigation approach associated with Tor,” CISA concludes.
Also read: Digital Transformation – Do Or Die in 2020