KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





Trojanized versions of SolarWinds’ Orion IT monitoring and management software have been used in a supply chain attack leading to the breach of government and high-profile companies after attackers deployed a backdoor dubbed SUNBURST or Solorigate.
The list of victims of this large scale attack, coordinated by what Microsoft and FireEye consider to be nation-state hackers, include several federal agencies such as the US Treasury and the US National Telecommunications and Information Administration (NTIA), as first reported by Reuters.
SolarWinds’ customer listing [1, 2] (with over 300,000 customers worldwide) includes over 425 of the US Fortune 500, all top ten US telecom companies, hundreds of universities and colleges, all five branches of the US Military, the US Pentagon, the State Department, NASA, NSA, Postal Service, NOAA, Department of Justice, and the Office of the President of the United States.
DHS-CISA has also issued an alert over the weekend warning of active exploitation of trojanized SolarWinds Orion Platform software versions which the attackers use to deploy a backdoor on unpatched servers via the update mechanism.
DHS-CISA also issued Emergency Directive 21-01 which orders all federal civilian agencies to “immediately disconnect or power down SolarWinds Orion products, versions 2019.4 through 2020.2.1 HF1, from their network.” The agencies are also prohibited from “(re)joining the Windows host OS to the enterprise domain.”
“We are aware of a potential vulnerability which if present is currently believed to be related to updates which were released between March and June 2020 to our Orion monitoring products,” Kevin Thompson, SolarWinds President and CEO, told BleepingComputer.https://www.ad-sandbox.com/static/html/sandbox.html
Also Read: Data Storage Security Standards: What Storage Professionals Need to Know
“We believe that this vulnerability is the result of a highly-sophisticated, targeted, and manual supply chain attack by a nation-state.
“We are acting in close coordination with FireEye, the Federal Bureau of Investigation, the intelligence community, and other law enforcement to investigate these matters. As such, we are limited as to what we can share at this time.”
In an 8K filing with the U.S. Securities and Exchange Commission, SolarWinds also said that it “believes the actual number of customers that may have had an installation of the Orion products that contained this vulnerability to be fewer than 18,000.”
SolarWinds is also working with Microsoft to remove an attack vector leading to the compromise of targets’ Microsoft Office 365 office productivity tools.
SolarWinds uses Microsoft Office 365 for its email and office productivity tools. SolarWinds was made aware of an attack vector that was used to compromise the Company’s emails and may have provided access to other data contained in the Company’s office productivity tools. SolarWinds, in collaboration with Microsoft, has taken remediation steps to address the compromise and is investigating whether further remediation steps are required, over what period of time this compromise existed and whether this compromise is associated with the attack on its Orion software build system. SolarWinds also is investigating in collaboration with Microsoft as to whether any customer, personnel or other data was exfiltrated as a result of this compromise but has uncovered no evidence at this time of any such exfiltration. – SolarWinds 8K SEC filing
This ongoing campaign has started as early as spring 2020 (starting with March 2020 when the first malicious SolarWinds Orion versions were introduced via the compromise of the Orion software build system) and its goals include but are probably not limited to data theft.
Nation-state hackers who coordinated these attacks have most likely been active in compromised networks since then, given that the first hacked targets were discovered in December.
The hacking group behind the SolarWinds supply chain attack are focusing their attacks against a large assortment of worldwide targets including “government, consulting, technology, telecom and extractive entities in North America, Europe, Asia, and the Middle East.”
“We anticipate there are additional victims in other countries and verticals,” FireEye said yesterday.
“FireEye has notified all entities we are aware of being affected,” the company said, confirming that the nation-state hackers that breached its systems (tracked as UNC2452) are the same as the ones abusing SolarWinds’ Orion business software.
Microsoft also published a blog and guidance for customers to defend against these ongoing attacks, also confirming the nation-state nature of the hacking group behind the SolarWinds Orion compromise.
As explained by Microsoft, the attacks start with “an intrusion through malicious code in the SolarWinds Orion product” after trojanized updates delivering a backdoor (tracked as SUNBURST by FireEye and Solorigate by Microsoft) are deployed on the targets’ systems.
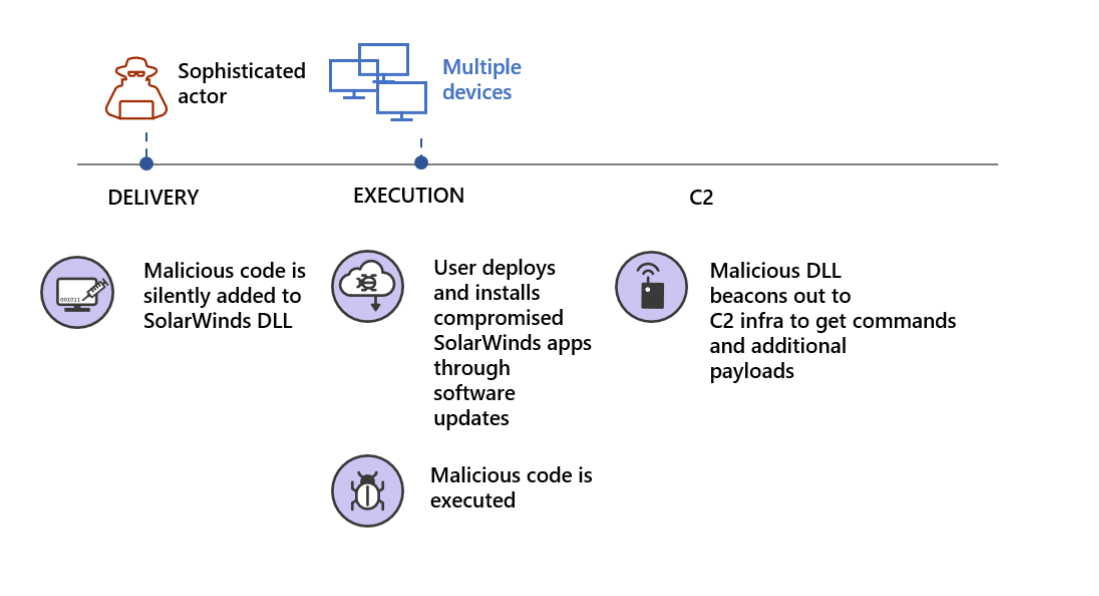
“While updating the SolarWinds application, the embedded backdoor code loads before the legitimate code executes,” Microsoft said.
“Organizations are misled into believing that no malicious activity has occurred and that the program or application dependent on the libraries is behaving as expected.”
“This results in the attacker gaining a foothold in the network, which the attacker can use to gain elevated credentials.
Once inside the victim’s network, the threat actors are elevating privileges to a global admin account or gain access to the victim’s trusted SAML token signing certificate.
This allows them to impersonate any account or user on the network, “including highly privileged accounts.”
Also Read: IT Governance Framework PDF Best Practices and Guidelines
SolarWinds has released Orion Platform version 2020.2.1 HF 1 to allow admins to secure systems running compromised versions (from 2019.4 HF 5 to 2020.2.1, released between March 2020 and June 2020).
“We are recommending you upgrade to Orion Platform version 2020.2.1 HF 1 as soon as possible to ensure the security of your environment,” SolarWinds’ security advisory reads. “The latest version is available in the SolarWinds Customer Portal.”
“An additional hotfix release, 2020.2.1 HF 2 is anticipated to be made available Tuesday, December 15, 2020.
“We recommend that all customers update to release 2020.2.1 HF 2 once it is available, as the 2020.2.1 HF 2 release both replaces the compromised component and provides several additional security enhancements.”
The company also provides additional hardening and mitigation info for those who cannot immediately apply the hotfix on vulnerable servers.
“The primary mitigation steps include having your Orion Platform installed behind firewalls, disabling internet access for the Orion Platform, and limiting the ports and connections to only what is necessary,” SolarWinds said.
“Additionally, we recommend customers scan their environment for the affected file: SolarWinds.Orion.Core.BusinessLayer.dll. If you locate this .dll, you should immediately upgrade to remove the affected file, and follow security protocols to protect your environment.”
Update December 14, 10:26 EST: The Russian Embassy in the USA reacted [1, 2] to a Washington Post report [1, 2] linking these attacks to APT29 (aka Cozy Bear and The Dukes), a group of nation-state hackers associated with the Russian Foreign Intelligence Service (SVR).
We paid attention to another unfounded attempt of the U.S. media to blame Russia for hacker attackes on U.S. governmental bodies.
Update December 14, 14:05 EST: The hacking group that breached the U.S. Treasury and the US NTIA has also infiltrated the U.S. Department of Homeland Security according to a Reuters report.