KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The US Department of Justice (DOJ) announced today that a Latvian national was charged for her alleged role as a malware developer in the Trickbot transnational cybercrime organization.
Alla Witte (aka Max) was charged with 19 counts of a 47-count indictment after being arrested on February 6 in Miami, Florida.
As a Trickbot malware developer, Witte wrote the code used by the malware to control, deploy, and manage payments of ransomware, the DOJ said in a press release published today.
Witte also purportedly provided the Trickbot Group with the code needed to monitor and track authorized malware users and developed the tools and protocols required to store login credentials stolen from victims’ networks.
The case was investigated by the FBI’s Cleveland Office and DOJ’s Ransomware and Digital Extortion Task Force, created to battle the increasing number of ransomware and digital extortion attacks.
“Witte and her associates are accused of infecting tens of millions of computers worldwide, in an effort to steal financial information to ultimately siphon off millions of dollars through compromised computer systems,” FBI special agent Eric B. Smith said.
Also Read: The DNC Singapore: Looking at 2 Sides Better
Trickbot is a malware strain first spotted in October 2016 as a modular banking trojan that has been continuously upgraded with new modules and features since then.
Even though initially used only for harvesting sensitive data, Trickbot has slowly evolved into a highly dangerous malware dropper used to deliver additional, usually a lot more dangerous, malware payloads on infected devices.
This regularly happens after all sensitive information (system info, credentials, and any interesting files) has been collected and exfiltrated to attacker-controlled servers.
On October 12, Microsoft and several partners announced that they took down some Trickbot C2s. The US Cyber Command also reportedly tried to cripple the botnet before the presidential elections by pushing a configuration file to infected devices to cut them off from the botnet’s C2 servers.
However, despite these coordinated attacks against TrickBot’s infrastructure, the TrickBot gang’s botnet is still active, and the group is still releasing new malware builds.
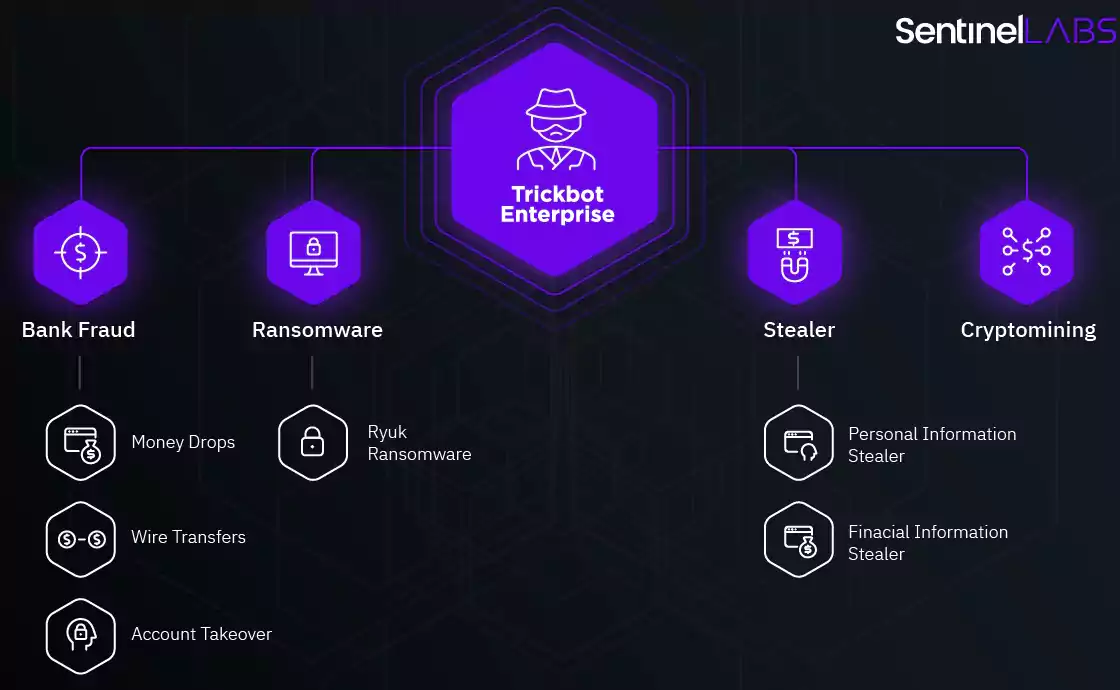
The TrickBot gang is known for distributing Ryuk and Conti ransomware onto the compromised network of valuable corporate targets.
Also Read: 4 Best Practices on How To Use SkillsFuture Credit
“Trickbot infected millions of victim computers worldwide and was used to harvest banking credentials and deliver ransomware,” Deputy Attorney General Lisa O. Monaco said today.
“The Trickbot malware was designed to steal the personal and financial information of millions of people around the world, thereby causing extensive financial harm and inflicting significant damage to critical infrastructure within the United States and abroad,” Acting US Attorney Bridget M. Brennan of the Northern District of Ohio added.