





The Federal Bureau of Investigation (FBI) and the Australian Cyber Security Centre (ACSC) are warning of an ongoing Avaddon ransomware campaign targeting organizations from an extensive array of sectors in the US and worldwide.
The FBI said in a TLP:GREEN flash alert last week that Avaddon ransomware affiliates are trying to breach the networks of manufacturing, healthcare, and other private sector organizations around the world.
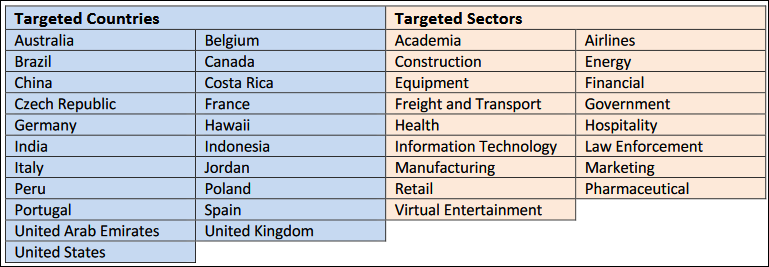
The ACSC expanded on the targeting information today, saying that the ransomware gang’s affiliates are targeting entities from a wide range of sectors, including but not limited to government, finance, law enforcement, energy, information technology, and health.
While the FBI only mentions the ongoing attacks, the ACSC also provides a list of countries under attack, including the US, UK, Germany, China, Brazil, India, UAE, France, and Spain, to name just a few.
“The Australian Cyber Security Centre (ACSC) is aware of an ongoing ransomware campaign utilizing the Avaddon Ransomware malware [..] actively targeting Australian organisations in a variety of sectors,” the ACSC added [PDF].
“The ACSC is aware of several instances where the Avaddon ransomware has directly impacted organizations within Australia.”
Also Read: 4 Best Practices On How To Use SkillsFuture Credit
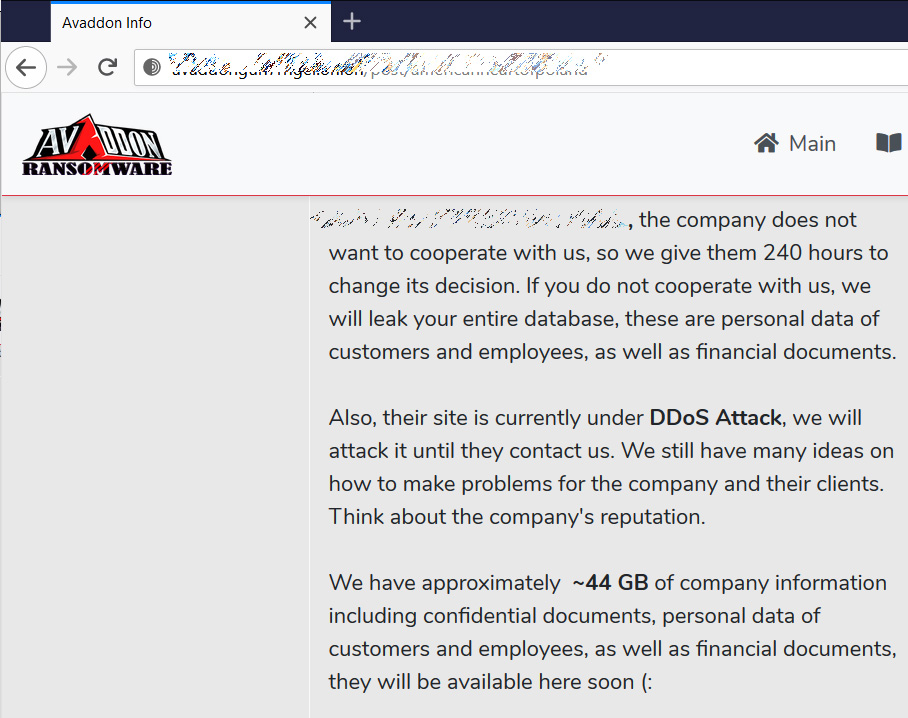
The ACSC also mentions Avaddon threat actors threatening with denial-of-service (DDoS) attacks to persuade victims into paying ransoms (in addition to leaking stolen data and encrypting their system).
However, as the FBI said, no evidence has been found of DDoS attacks following Avaddon ransomware attacks.
The Avaddon ransomware gang first announced in January 2021 that they will launch DDoS attacks to take down victims’ sites or networks until they reach out and begin negotiating to pay the ransom.
BleepingComputer first reported about this new trend in October 2020, when ransomware groups began using DDoS attacks against their victims as an additional leverage point.
At the time, the two ransomware operations that were using this new tactic were SunCrypt and RagnarLocker.
Also Read: 3 Reasons Why You Must Take A PDPA Singapore Course
Avaddon ransomware samples were first detected in February 2019, and it began recruiting affiliates in June 2020 after it launched a massive spam campaign targeting users worldwide.
Affiliates who join this RaaS operation are responsible for compromising networks to deploy payloads or distribute the ransomware via spam or exploit kits. At the same time, its operators are accountable for developing the malware and operating the TOR payment site.
The Avaddon RaaS operation also asks affiliates to follow a set of rules, one of them being not to go after targets from the Commonwealth of Independent States (CIS).
Avaddon pays each affiliate 65% of ransom payments they bring in, with the operators getting a 35% share. However, as with other RaaS programs, larger affiliates can usually negotiate higher revenue shares depending on the size of their attacks.
The average ransom payment demanded by Avaddon affiliates is roughly 0.73 bitcoins (approximately $41,000) in exchange for a decryption tool (Avaddon General Decryptor).
Avaddon ransomware affiliates are also known for stealing data from their victims’ networks before encrypting systems for double-extortion.
This strategy has become commonplace for almost all active ransomware operations, with victims commonly notifying their customers or employees of possible data breaches following ransomware attacks.