KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Vote Joe app, used by the Biden 2020 Presidential campaign to better engage with voters, was found to be leaking potentially sensitive information about voters, such as their political affiliations and past voting choices.
The iOS app also didn’t enforce email verification which would let anybody, including non-US citizens, download the app and have access to this data.
Vote Joe app leverages what’s called “relational organizing.” Volunteers who download the app can promote the campaign by sending pre-typed promotional text messages to others, and provide information about their contacts to the app creators.
Voter registration records are already public information, so the app providing access to these isn’t concerning. However, the app corroborated this information with an intelligence service Target Smart and returned their predictions via its API endpoint, which can be problematic.
Target Smart’s VoterBase product claims to be “containing the contact and voting information of over 191 million voters, and 58 million unregistered, voting age consumers.”
Also Read: How a Smart Contract Works and Why it is Important
The app’s user interface would only let you query the public voter records, and see if they had voted in the past years or not.
However, digging deeper, mobile apps researcher The App Analyst found the API endpoint providing this data, was returning some additional fields.
While not all of these fields were visible in the interface, the app paved a way for providing Target Smart’s proprietary voter data to anyone with access to the app (including those using a fake, unverified email address). The proprietary data specifically exposed the past voter choices.
As shown in the researcher’s blog post, the “vb.vf-g…” fields returned the “B” or “R” flags indicating whether the voter would have voted Blue (Democrat) or Red (Republican) respectively, in the past.
These are predictions, of course, made by Target Smart and not an authoritative answer, but this kind of proprietary information was not meant to be available to anyone.
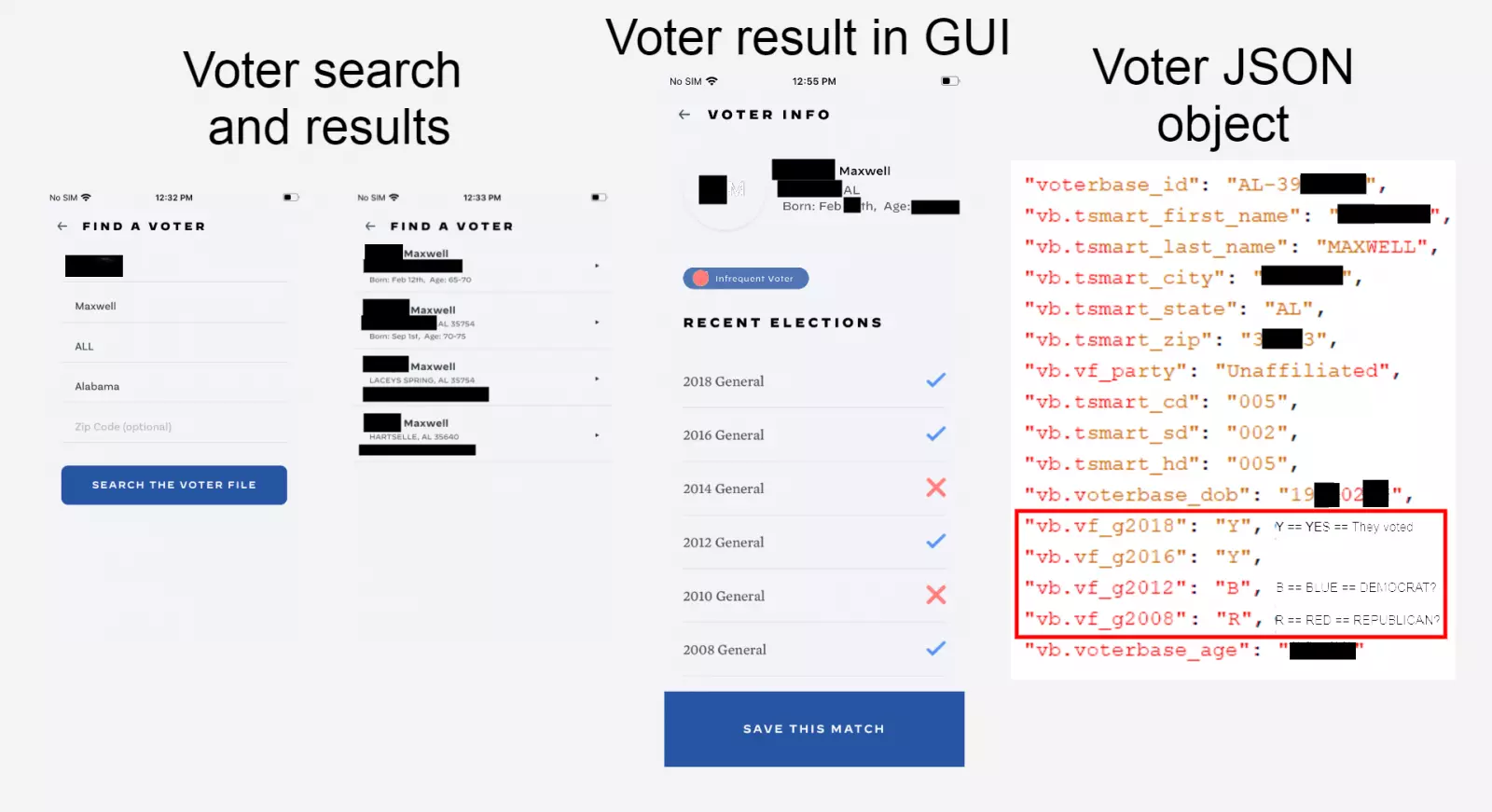
“There is additional hidden information about the voter such as their specific date of birth, “voterbase_id” (a value unique to Target Smart and not an official voter id), and some Target Smart fields (prefixed with “tsmart”) corresponding to the voters senate, congressional, and house districts (more “tsmart” fields,” the blog post continues.
The app harvests valuable information from user’s contacts as a part of its terms of service.
But because anyone can download the app and there are no strict authentication requirements, anybody could potentially “pollute” the data being harvested by the app’s creators.
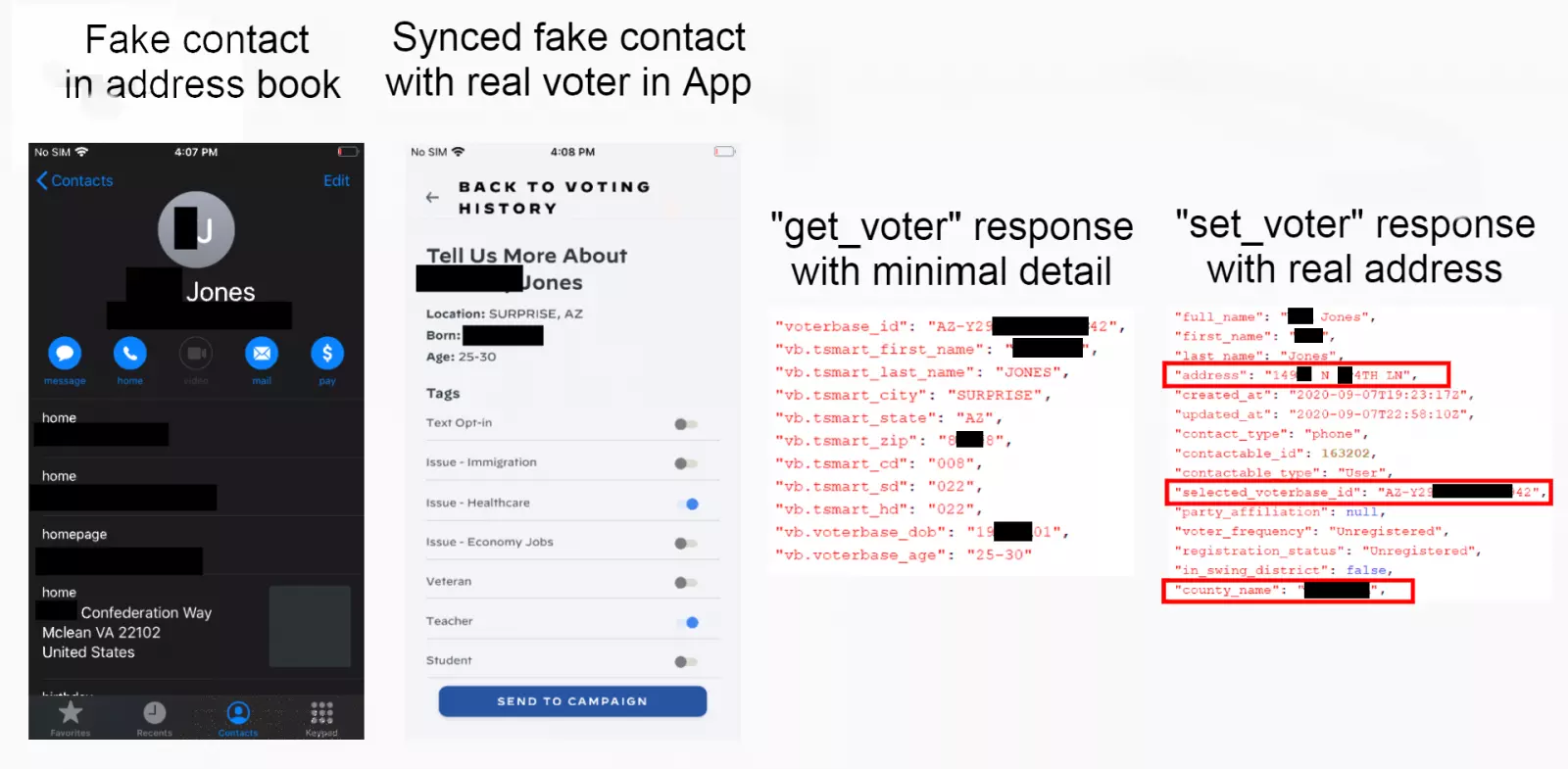
For example, an adversary could create fake contacts with deceptive information in their phonebook which when uploaded to the app, corrupts the overall dataset being relied on by the campaign.
“When a user syncs their contacts with the Vote Joe App they will be presented with a corresponding voter entry from the Biden campaigns voter database. The contact data then enriches the database entry and is stored to help solicit their vote in the future,” explains the blog post, further adding:
“An issue occurs when the contact in the phone does not correspond with the voter but the data continue to enrich the voter database entry. By adding fake contacts to the device a user is able to sync these with real voters.”
The Vote Joe app team was notified by The App Analyst of these security flaws on September 7, 2020. The team promptly patched these in the iOS versions of the app by September 11th.
As verified by the researcher, the app’s API endpoints now return minimal information about a voter and the user interface goes even a step further to redact fields like the voter’s date of birth.
Also Read: How to Send Mass Email Without Showing Addresses: 2 Great Workarounds
The app created and distributed by the Trump 2020 campaign comes with its fair share of issues as well.
In June, the app’s Android APK file exposed hardcoded secret keys associated with the Twitter and Google services it used.
And just last month, the Trump 2020 app was found to be collecting large amounts of user data, ironically engaging in what the Presidential executive order banned TikTok for.
“Cyber security researchers have poured over the source-code and found exposed app keys, and the severity of it’s user tracking has been compared to TikTok. Needless to say the application has been reviewed quite heavily by security researchers,” explained The App Analyst in a separate blog post.
What distinctively stands out about Trump campaign’s app though is, what The App Analyst calls, their “election gamifying” model.
The app offers rewards and honorable mentions to users who are able to gather significant amounts of donations for the campaign: either from their own donations or through referrals.
Every dollar donated to the Trump campaign earns the supporter 10 points. Supporters gaining the most points get their names mentioned on the Official Trump 2020 leader board.
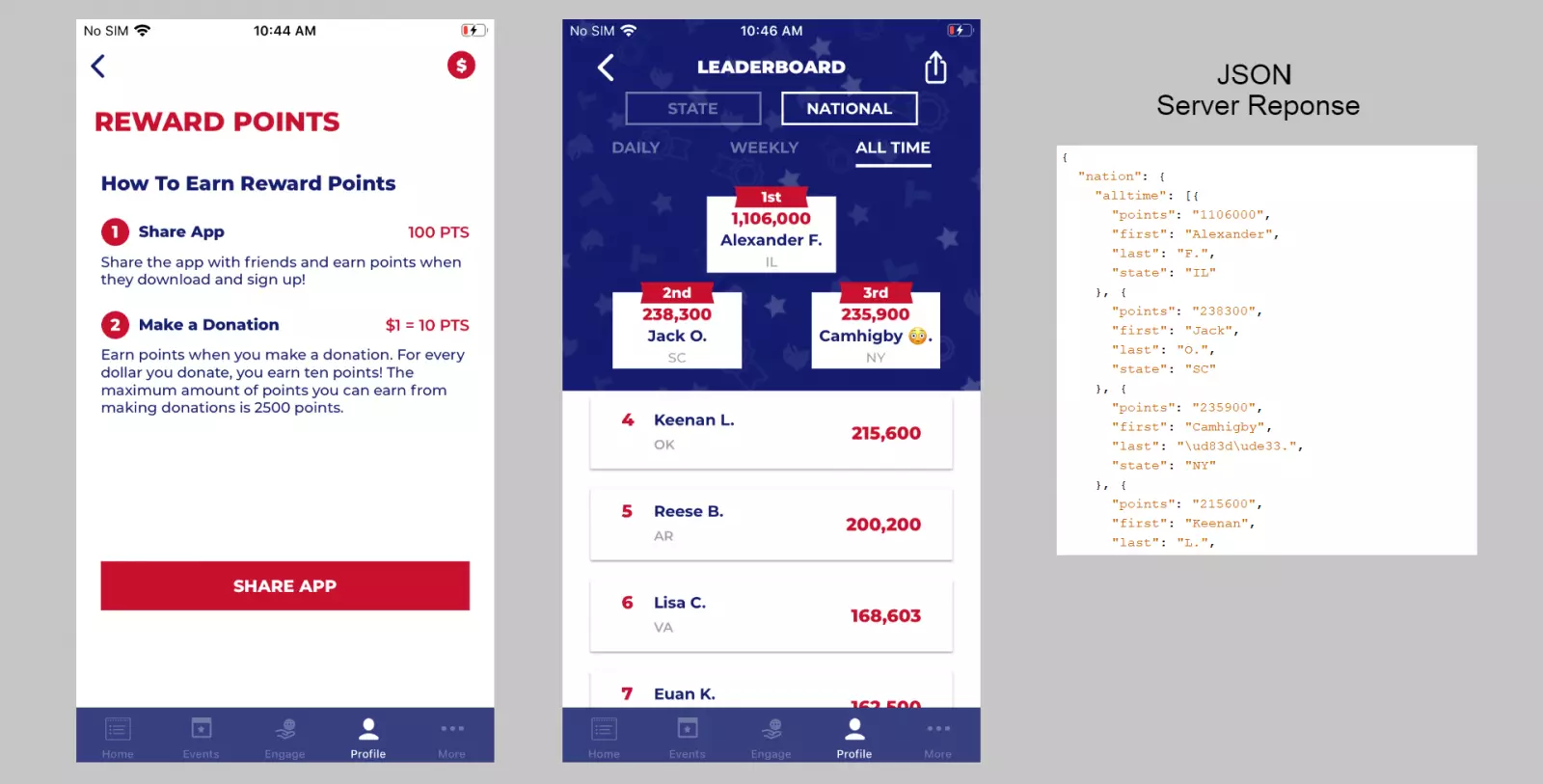
“The leader board currently lists Alexander F. from Illinois as the nations leading scorer with 1,106,000 points. This could have been achieved through having 11,060 of Alexanders friends install the application, a donation of $110,600, or a mix of the two,” The App Analyst explains.
At a first glance, these privacy and security flaws may seem innocuous since political campaign promotional apps typically use government-provided public data. However, complications arise when the apps collect too much data and the public data is corroborated with targeted intelligence which can predict people’s voting choices.
By exposing information about how people vote to anyone, these flaws compromise the privacy implicitly expected by the voters in a democratic election process.
Unless data security and privacy can be absolutely guaranteed by an app developer, it may be a good idea to collect minimal information from the users, to begin with.