KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







An undisclosed Cross-Site Scripting (XSS) vulnerability in Apache Velocity Tools can be exploited by unauthenticated attackers to target government sites, including NASAand NOAA.
Although 90 days have elapsed since the vulnerability was reported and patched, BleepingComputer is not aware of a formal disclosure made by the project.
Apache Velocity is a Java-based template engine used by developers for designing views in a Model-View-Controller (MVC) architecture.
Velocity Tools is a subproject comprising classes that further ease the Velocity integration within standard and web applications.
Apache Velocity Tools has an undisclosed XSS vulnerability, which impacts all its versions despite a fix having been published on GitHub months ago.
Although a formal vulnerability disclosure has not taken place, BleepingComputer has been informed that this flaw is being internally tracked as CVE-2020-13959.
On querying Sonatype’s Nexus Intelligence systems, I discovered the Apache Velocity Tools class containing this flaw is included in over 2,600 unique binaries of prominent software applications available to download from npm, PyPI, Maven Central, and other open-source repositories.
The component’s popularity among developers makes timely disclosure of vulnerabilities impacting Velocity Tools crucial.
Security researcher Jackson Henry of the Sakura Samurai ethical hacking group had first discovered and reported the vulnerability to Apache in early October, 2020.
Although the project had acknowledged Henry’s report and issued a publicly visible fix on GitHub on November 5th, 2020, a proper public disclosure never took place which left Sakura Samurai researchers concerned.
Also Read: Key PDPA Amendments 2019/2020 You Should Know

The reflected XSS flaw exists in how the VelocityViewServlet viewclass renders error pages.
When an invalid URL is accessed, the “template not found” error page reflects the resource path portion of the URL as it is without escaping it for potential XSS scripts.
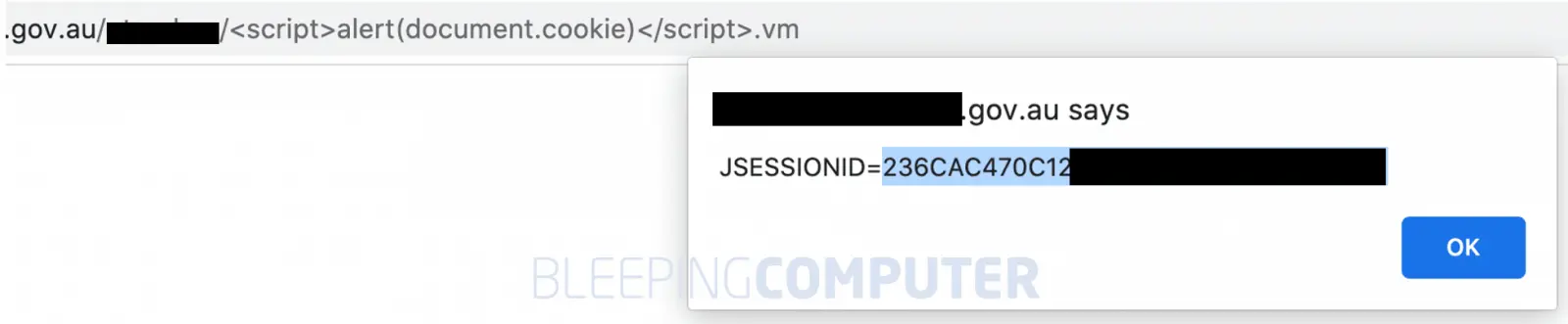
An attacker can consequently trick a victim into clicking such a URL, which leads the victim to an altered phishing page, or exfiltrates their login session information.
As observed by BleepingComputer, the vulnerable Apache Velocity Tools instances are being used by government websites, including *.nasa.gov and *.gov.au.
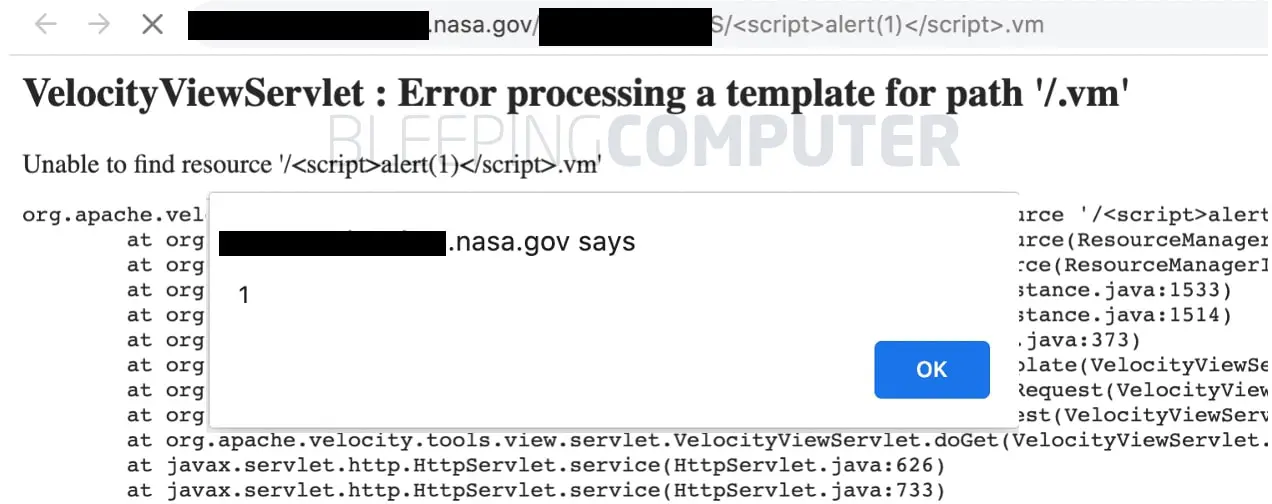
More sophisticated variations of this XSS exploit, when combined with some social engineering tricks, can let attackers collect the logged-in users’ session cookies, and potentially hijack their sessions.
This is especially relevant to employee and contractor login portals hosted on government domains such as the one shown below.
When contacted by BleepingComputer for comment, the Apache Software Foundation (ASF) stated that the Apache Security Team receives hundreds of vulnerability reports in a year and that they respond to them in a timely manner based on the severity of the issue, as shown in their annual security report.
“With regard to the XSS vulnerability in Apache Velocity tools, the Apache Security Team were first contacted by an individual (referred to as an issue reporter) on 6 October 2020 who disclosed an issue they had found affecting part of the Velocity Tools package.”
Also Read: The 5 Benefits Of Outsourcing Data Protection Officer Service
“We shared this privately with the Apache Velocity Project Management Committee (PMC) who investigated and accepted the report on 7 October and suggested that the reporter submit the patch.”
“The reporter then submitted a pull request and over the course of a couple of weeks, the team worked to refine the fix. That fix was applied on 5 November. The reporter submitted their patch in public on 8 October and due to the non-critical nature of the vulnerability, the Velocity team decided to continue to work on the issue in public.”
“The issue was internally assigned CVE-2020-13959 on 8 October,” Mark J Cox, Vice President ASF Security told BleepingComputer in a statement.
The next step left for the project is to make a fixed Velocity Tools release that will mention the CVE, and an upgrade path, the date for which is yet to be determined.
However, users who would rather not wait for a fix to be released can experiment with applying the publicly visible fix themselves.
In recent times as the number of vulnerability reports continues to grow exponentially, MITRE, the nonprofit body tasked with assigning CVE IDs has met with scalability challenges.
To speed up the CVE assignment and responsible disclosure process, the concept of CVE Numbering Authorities (CNAs) was introduced.
The organizations that get approved as a CNA are authorized to assign CVEs for vulnerability reports, and handle the responsible disclosure process on behalf of MITRE.
However, lately, more and more vendors are stepping up to become CNAs and taking control of the vulnerability disclosure process.
This has left infosec professionals concerned if this development could actually hinder security in the long run.
As previously reported by The Daily Swig, under MITRE’s rules, a CNA is not required to assign CVEs to vulnerabilities reported privately to projects, some of which could include their own products.
This means vendors get to quietly fix even the most severe security issues now without having to immediately report them publicly.
Most recently, this happened in VMWare’s case when an unauthenticated file read vulnerability was reported in vCenter by PT Swarm researchers and quietly patched by VMWare, without a CVE being issued immediately.
“Companies need to take security vulnerabilities seriously and work with researchers to devise patches.”
“Communication and status updates are essential for keeping researchers in the loop, it’s an important aspect of remediation that can be overlooked and detrimental to transparency—discouraging even,” Henry told BleepingComputer in an email interview.
Apache Security Team has shared details of their CVE handling process with BleepingComputer which can sometimes involve briefly delaying vulnerability disclosures for non-critical issues.
“Where security issues are not critical, some projects will hold off a short time for a release to allow other issues to be addressed at the same time.”
“Of note in this instance is that every email that the issue reporter sent to the ASF security team was responded to within one working day, with the reporter praising our fast response, so we’re a little surprised to learn that the reporter feels they have been ghosted,” Apache Security Team told BleepingComputer.